How To Find A Scammer Ip Address
How to Identify Anonymous IP Addresses to Detect Online Fraud
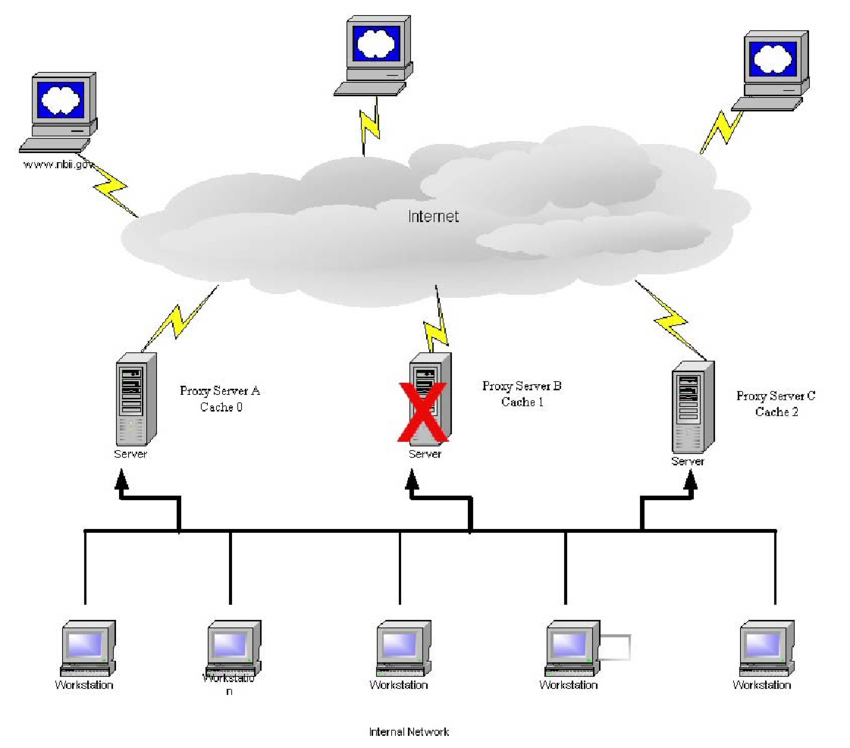
BigDataCloudEssential APIs for feature-rich eCommerce, ad agencies, financial institutions & CRM we make our way through the global pandemic, the Internet is playing a crucial role in normalising our day to day activities. Businesses have been going through rapid digital transformation, contributing to increased online financial transactions, shopping, communication, education, and entertainment. We are also witnessing an increase in cybercrime and other malicious online behaviours. There is a growing concern among people about online security. As more and more news of scams and fraud make their way into our everyday conversations, we are continuously made aware of the danger of being the victim of cybercrime. To make matters worse, the rising concern of being monitored by government agencies and tech corporate giants have also created an uneasy sense of being watched 24/7, resulting in paranoia and speculation. Right to digital freedom and online privacyAs a result, our right to digital freedom, online privacy and security have become key topics of discussion on public forums. Not just for individuals but also for small to large businesses that are concerned about the security of their business. This concern has given meteoric rise to the popularity of VPN (Virtual Private Network)/proxy fear of online scams and unauthorised surveillance, combined with aggressive marketing from VPN service providers, are driving the adoption of such services. Further, a simple and affordable VPN service can start at just $10 per month, allowing you to switch your anonymity on or off as easily as clicking a latest research from the Global Web Index has reported that more than 26% of all internet users rely on VPN services. The potential market size of VPN is predicted to reach $88. 6 Billion by 2027. The Implication of Online Anonymity Towards SecurityHowever, the growing use of such services also means it’s getting difficult for online businesses to separate scammers from the good ones. Using online services like VPNs or proxies is similar to visiting a physical store with a mask. It does hide your identity, but it also signals a threat to the shopkeeper. What would you do if someone wearing a mask enters your shop, office or home? So there are two sides to maintaining your anonymity on the Internet. If you are living in a country which has an oppressive government that monitors your digital footprints then, yes, it might make a lot of sense to hide your identity to protect yourself. However, if you intend to carry out criminal activities or break the law, then it might not be fair use. It’s important to note that anonymity only hides your identity and you are still vulnerable from cybercrime like getting tricked by phishing websites to share your personal information. For example, if your iCloud account gets hacked, it has more to do with the weak password and lack of additional validation processes, than with not using VPN of VPN and ProxiesOne of the most popular uses of VPNs or proxies is to circumvent geo-blocking to access locked digital content in your region on platforms like YouTube, Netflix, online games or other popular streaming services. You will also find VPN services promoting this on their homepages, and so this might be a principal reason for users to adopt the service rather than just for the sake of security or Source: GlobalWebIndex Though digital services implement robust technologies to detect unsolicited access, it has become a cat and a mouse game where each side is trying to gain an advantage. Further, not all VPN services are created equally. Many free and cheaper services don’t have strong security measures. It must be remembered that when you try to hide your identity from someone, you are also at the same time giving it away to others. You might be invisible to others on the Internet, but the VPN/proxy service providers still have all your historical behavioural data. Hence, it is a question of who do you trust, your local ISPs or some international proxy services are notorious for being a hotbed for attackers. They are mostly insecure, don’t necessarily hide your identity, and are filled with malicious ad Oct 2019, one of the most popular VPN service providers NordVPN confirmed that it was hacked. This exposed vulnerabilities in VPN services and opened them for scrutiny on public FraudAmong many types of cybercrime, payment fraud is the most common, where your credit card details are stolen and misused by the criminal to carry out fraudulent transactions. In 2018 alone, the total loss due to global card fraud was $27. 85 billion. As more and more small and medium businesses move online, we might see this number key component of detecting such fraud is the detection of anonymous IP addresses. No hackers or cybercriminals use their home internet service to carry out their nefarious activities. Most attacks are originating from hosting services and other services which hide their real IP erefore, detecting anonymous IP addresses has become essential for online businesses. Though not all anonymous IP addresses can be detected with 100% accuracy, such technology can certainly act as a deterrent against online for example the case of credit card fraud. The usual standard checks are to compare the billing address, delivery address and the IP address of the user. Any detection of discrepancy or anomaly can be used to probe the transaction further and prevent adding additional checks for identifying if an IP address is originating from hosting, VPN or proxy servers, instances of fraud can be reduced even further. However, attackers are getting more sophisticated in their approach. For example, it is common for attackers to hijack a residential router and use it as a proxy to carry out fraudulent activities. This method is really difficult to detect because the originating IP address appears benevolent and genuine. Even many fraud detectors would fail to classify such transactions as fraud. But, hijacking home routers in itself is a difficult task. Hence stories have been emerging that suggest many global and reputed ISP providers have been selling their residential IP blocks to proxy/VPN service providers. More about this story can be read has heavy implications on our cybersecurity because an attack originating from a residential network is very difficult to detect. Not to mention that it is already a mammoth task to detect hosting and cellular network connections with IP a side note, this is the key area where BigDataCloud has been innovating and developing technologies that can detect hosting networks which are not listed in any public registry or directories. More about this in a later erefore, despite the popularity of VPN for protecting privacy and security, it has a dominant role in the growth of online attacks. Is hiding an IP address worth it? The main purpose of hiding an IP address is to protect your identity and hide your online activities. However, hiding an IP address alone is only one way of protecting your online identity. Today, when you visit a website there are various components working together to identify you. For example, the use of social networking tracking tools like Facebook pixel, Linkedin tracker or Twitter tracker can reveal more about your identity than an IP address. Moreover, if you are browsing through a mobile device you are likely to reveal your personal information to companies like Google and Apple, even if you hide your IP you are really concerned about your identity then just hiding your IP address is not enough. The ownership of an IP address is frequently changing, unless you have a statically assigned IP address from your ISP, or you own a chunk of IP addresses and you are using them for your official or internal purpose. Hence, masking IP addresses doesn’t provide 100% hacking and cybercrime is the result of our own carelessness while surfing the Internet and revealing our personal information to untrustworthy sites. A compromised email address, social account or website is much more harmful than exposing your IP of IP Address ExposureThe general fear about exposing an IP address is that it reveals the location from where you are accessing the Internet, which is true to some extent. With advanced IP geolocation technology and the support of government officials and ISPs, it is possible to identify the location of IP addresses with high accuracy. (If you are interested to learn more about IP addresses and how IP geolocation technology works, check out our detailed blog post here) But, you need to invest huge amounts of time, resources and support from the law to accurately and precisely pursue geolocating IP addresses – and you need to be lucky in your, if your IP address is compromised, it is possible for hackers to launch DDoS attacks at your IP address by IP spoofing. This type of attack exploits the vulnerability of the design of TCP/IP protocol where it is possible to falsify the IP address in the source header of the IP packets. As a result, anyone can send random packets on the Internet by making them look like they are originating from your IP address. As a result, your IP address starts to get continuous hits from everywhere resulting in temporary or indefinite network congestion. This is analogous to someone sharing your email address to a list of junk websites and jamming your mailbox with spam emails. However, the implementation of robust network security can easily avoid such erefore the fear of someone stealing your IP addresses to reveal your home address or using it to access your device is just a thods of hiding your IP addressBefore digging deeper into detecting anonymous IP addresses, let’s try to understand the various ways in which a user can mask their IP address while browsing the Space WiFi:By surfing the Internet using publicly available WiFi networks in restaurants, libraries or airports, you are not compromising your personal home or office location. Hence, it is the easiest way to surf the internet with anonymity. However, public space WiFi isn’t the safest place for accessing sensitive websites because the network is widely accessible to anyone in the area and is susceptible to threats. Further, as mentioned above, IP addresses are just one aspect of your identity available on the Internet, your apps, social sites and many other agents are more prone to Proxy servers:A proxy server essentially acts as a middleman between the client and the server. It can be placed at both the client-side and server-side. Based on where it is located it might be named differently – forward proxy and reverse proxy. With the help of forward proxy, schools and offices can restrict access to the entire Internet and limit their content. Reverse proxy, on the other hand, is implemented at the server-side to filter the incoming requests and has various applications like load balancing, threat protection, caching, SSL encryption etc. When the proxy server is placed at a different location than yours, it can be used to mask your location because all your requests will be served by the proxy server. However, not all proxy servers hide your IP address and use secure connections. Therefore, while using public proxy servers, you have to be careful that you are not unknowingly compromising your data instead of protecting it. TOR:The Onion Router(TOR) is a popular method of surfing the Internet to hide one’s identity and it is commonly used by journalists and activists who have to bypass the authorities to communicate or access information on the Internet. It is based on a decentralised system where the user’s request goes through several servers before reaching the target. In addition, the requests are encapsulated with layers of encryptions that are decrypted at each node, one by one, hence the name The Onion is also a free and open-source project where volunteers worldwide participate to create an overlay network consisting of more than seven thousand relays. You can easily use TOR by downloading their browser from their website. The browser is available for all major desktop OS and mobile devices. However, due to the nature of the network, it is comparatively slower than regular internet browsing. Hence, it might not be effective for streaming video content, playing games and other data-heavy recent years, VPN services have been mushrooming all over the place promising security and privacy for the general public. However, the original intention of a VPN (Virtual Private Network) was to allow users to remotely access a private network over a public network, hence simulating the experience of being locally connected to the private network. This was established so that large organisations could connect multiple branch offices together in order to access and share resources allowing remote workers to access official resources securely via the VPN. Due to the nature of the network and how it encrypts data, it is widely illustrated as a secure tunnel between two disparate networks. The popular VPN services, today, are using a wide range of security protocols like OpenVPN, IKEv2/IPsec, WireGuard and so on to tunnel traffic from point to point or between networks. As a result, VPN services allow users to mask their location and access restricted content or bypass ever, many services are actively implementing technologies to detect VPN and flag them. China, for example, only allows approved VPN providers to operate. Any use of unapproved providers is considered a crime and users may have to pay a hefty penalty for ing Providers:Though not popular among the general public, using web hosting services to create proxies to hide your IP address is a widely used method by bots and cyber attackers. As it is highly unlikely for criminals to use their own ISP network to launch an attack, they are often found using hosting services. As there are many hosting providers across the world, it is quite challenging to detect and flag them. Hosting services are also popular among VPN providers and sidential Proxy/VPN:As mentioned in the previous section, the use of residential IP addresses as a host for VPN services is growing and are largely undetected. This might sound alarming but security researchers have been discovering services that claim to anonymise your IP address with residential IP addresses, making it difficult to detect. Residential IP addresses are those that are assigned by ISPs to the general public such as home internet service order to use such illegal services, users are mostly required to voluntarily share their residential connection making it a part of a larger peer to peer network. However, research has also shown that compromised IoT devices, malware and other illegal ways are also being widely used to hijack a residential user’s internet connection to use it as a proxy. The other corroborating stories have also revealed that the global ISP providers are illegally trading their IP addresses with nefarious ISP service providers who are using them for creating residential IP based VPN and proxy nsidering that the setup of residential proxy/VPN services is highly suspicious, they are mostly used to fraud or scam the system. One popular use includes creating fake social profiles on Facebook or Gmail to carry out internet fraud like generating spammy website traffic or ad clicks. In recent cyber security research, it was reported that Australian marketers will lose $756 million in 2020 due to invalid clicks on their paid search campaigns. Similarly, such proxies can be used to create multiple fake accounts for games and other social platforms to generate fake hits in order to manipulate the tecting Anonymous IP address – Proxies/VPNsThough anonymising IP addresses provides privacy and some level of security to the users, this is often exploited by scammers, hackers and fraudsters to carry out malicious activities. Hence, it is of great importance for businesses to detect such connections and flag them for further investigation. Imagine being able to detect fraudulent clicks and nullify the transaction, it would save millions to brands and add value to the a result, various non-profit organisations and communities are constantly monitoring the Internet to detect malicious activities and create blacklists. Spamhaus project is one of such international organisations that are working to provide real-time threat and reputation blocklists. These are widely used by ISPs, mail service providers, corporations, universities, governments and the military to protect against cybercrime. Such lists are really helpful in detecting anonymous IP addresses and suspicious activities. UCEprotect is another community that is working on a mission to obliterate mail spam. They have a stringent policy of blacklisting IP addresses at three different levels. At each level, the range of IP addresses increases to include the entire AS network. They also use various spam traps and work with partners to monitor servers that are sending spam emails. Upon detection, the IP address is blacklisted until no further spam activities are detected. The above lists are generally created based on the detection of cyber attacks and spam activities. However, the other method is to discover a list of IP addresses listed on free public proxy service providers and use them to create a list of IP addresses belonging to proxy servers. Generally, bots are implemented to crawl sites that advertise proxy servers to build such, on the other hand, publicly shares the list of TOR nodes on their website making it easier for businesses to detect traffic from their network. Another rather technically complex method in detecting proxy access is by using Snort rules. Snort is a popular and widely used open-source Intrusion Detection System. It operates at the network (IP) layer and transport (TCP/UDP) layer protocols where you can write snort rules to check various parts of data packets for known attack signatures. However, this method requires active monitoring of packets arriving at your server and flagging activities that look suspicious. All the methods listed above are reactive to a threat that has already been observed and listed. They cannot detect all the malicious services and are limited to identifying only services that are listed on relevant websites. The next section discusses how to protect against a new unknown attack from a fresh tecting Hosting EnvironmentsA more proactive approach needs to be implemented to detect new attacks from unknown sources and handle them. One such method lies in detecting the likelihood of IP addresses belonging to hosting environments. Considering that the majority of cyber-attacks originate from hosting environments, detecting the network type of an IP address can play a huge role in fraud example, a data centre or widely speaking a hosting IP address originated activity should always be handled with great caution, for instance, when placing an e-commerce order or leaving a comment on a straightforward method of detecting hosting environments is by carrying our reverse DNS on the IP address and parsing the domain name to detect the company or service name. Most standard and global hosting providers like Google or Amazon, use standard naming systems that are easy to identify. But there are thousands of hosting providers who don’t follow the standards and further curating the list of hosting providers name in itself is a challenging task. Similarly, with VPN providers, we might be able to detect VPN connections based on their DNS information but it is not BigDataCloud, we utilise our proprietary AI-based technology to examine every IP address globally to estimate the likelihood of the network being assigned to a hosting environment. The outcome of this assessment is provided as a ‘hostingLikelihood’ score ranging from 0 to 10. Moreover, we also provide a metric to detect if the Autonomous System, which announced the network, is likely to be a hosting provider or ever, detecting the hosting environment is difficult and rare. Due to our existing IP geolocation technology, which is the first fully scientific method, we are able to detect hosting environments using various forms of evidence available. This method not only works for unidentified VPN/Proxy and hosting networks but also residential proxy connections which are more fuzzy in nclusionDetecting a malicious IP address is complex and a 100% accuracy rate cannot be achieved. Though not all anonymous IP addresses are malicious, all malicious IP addresses are definitely anonymous. Hence, a false positive result of detecting such IP addresses is much better suited for dealing with fraud rather than accurate detection. Further, IP detection combined with other common logics and available user data can strengthen fraud detection. Though anonymous IP addresses have their place in protecting privacy and security to some level, their usage in cyber-crime threatens the security and growth of online commerce. As more and more people start using VPNs and similar services to browse the internet, it is going to become more difficult to identify them. A single technology isn’t going to be enough to prevent an increase in global cybercrime, it will require the collaboration of various parties involved in delivering internet services and products around the eviously published at Hacker Noon Create your free account to unlock your custom reading experience.
How to Track Someone’s IP (and Location) With a Link
nmedia/Shutterstock
Where is the person you’re talking to located? Are they who they say they are? To check, you can have that person click a special link. You’ll see their IP address, and that will tell you their rough location.
How IP Tracking Links Work
Wait a minute: They said they were in the US, but this says Nigeria!
We recently played along with a fake job recruiter scam. We knew at the start this was a scam, but we wanted to confirm the scammer’s location. They said they were in the US—but were they? We checked by tracking their IP with a link.
There’s nothing special about this—when someone accesses a resource online, the server sees their unique IP address. And IP addresses are tied to rough geographic areas. But popular web services don’t usually show you the IP address of that person, although you could certainly see it yourself if you were hosting your own web server. The method here uses an online service that “wraps” a real link for you, tracking the IP address that accesses it before quickly sending the person to the real target of the link.
This has its limitations. Anyone can use a VPN to mask their real location. But, even if they are, there’s a good chance the VPN will show a different location from where they claim to be. In the case of our fake job recruiter, the scammer claimed to be in the US, but they accessed our link from an IP address based in Nigeria.
If you don’t already know the location someone claims to be from and are just trying to figure out whether they’re genuine, you’ll need to convince the person to say where they are before sending them the link. Working that into conversation shouldn’t be too tricky, the nature of the internet makes asking for location a routine part of an online discussion—does anyone else remember A/S/L?
Once you do, you’ll need to prepare a digital file to send them. A picture, a Word document, or anything you can attach to a cloud storage link will do. If you’re dealing with a possible scammer, that scammer might ask you to send them something as part of a scam. If you’re dating online, you might want to send a photo. Once you’re ready to send a file, you’ll need to wrap that normal link with an IP tracking service.
Unfortunately, that process creates a link that’s obviously for tracking. You’ll need to use another service to hide that. You probably don’t want the other person to spot your trick.
RELATED: Scam Alert: Fake Job Recruiters Tried to Catfish Us, Here’s What Happened
How to Create a Disguised Tracking Link
You can use a link to any web page online, but this process will guide you through creating a link that goes to one of your files or photos.
The first step is to upload your file to a cloud service like Dropbox or Google Drive. If you suspect the person you’re interacting with isn’t trustworthy and you don’t want to give any personal information away, it’s a good idea not to use any main account you have. You may want to create a second “throwaway” account if you don’t already have one.
With your file uploaded, use the website to create a shareable link. In Google Drive, you can right-click on the file and choose “shareable link. ” In Dropbox, hover your mouse over the file and select share.
This is the link your suspected scammer will land on at the end of the process. But don’t give this link to them. By itself, it tells us nothing.
Instead, go to the IP logger website and paste your URL into the “URL and Image Shortener” field. Click the “Get IPlogger code” button below it.
The next screen will give you an “IP logger link for collecting statistics” and “link for viewing statistics. ” Copy the “viewing statistics” link to a safe spot. This is what you’ll use to see the person’s IP address and location afterward.
The link for “collecting statistics” is the one with IP tracking in it. Unfortunately, that “” link will be a dead giveaway to your recipient.
To hide what you’re doing, you can use a URL shortening service. Unfortunately, those shortening services don’t like the IP Loggers URLs and generate errors. To get around this, click on the drop-down to the right of “Select a domain name” and choose “” for your domain. The tracking link at the top will update, copy that new link.
Next, go to —you can try another shortening service if you prefer, but we tested with Bitly. If you don’t already have an account, create one.
Click the “Create” button in the upper right-hand corner of the Bitly website.
Paste your tracking link into the “Paste long URL” box and click the “Create” button.
You now have a Bitly link you can give to your potential scammer. You can click the copy button to retrieve it quickly.
How to See the Recipient’s IP Address
Send that link to the person you’re talking to as you would a standard link. After you have, go back to IP logger, copy the viewing statistics link, and paste it into your browser.
You’ll see a list of any IP addresses that accessed the link, what location they’re from, and possibly what browser they’re using.
Remember, this won’t tell you everything. If the person is using a VPN or similar technology, you won’t see their true location. But it’s one more tool in your arsenal to spot people who aren’t who they claim to be. If your tracking results show a different country than you’re expecting, be wary and consider walking away.
READ NEXT
› How to Upgrade Your PC to Windows 11
› How to Put a Link in Your Instagram Bio
› Surprise: Windows 11 Arrives a Day Early
› How to Find, Add, and Remove Fonts in Google Slides
› Epic Games Store Finally Getting Achievements
IP Address Fraud Check – Scamalytics
Lookup any IP address to fraud check that IP. Check the fraud score, view supporting information including true country, operator, proxy status, and Tor status.
High Risk IP Addresses
100161. 97. 119. 195
Contabo GmbH
10046. 36. 200. 91
NFOrce Entertainment BV
10080. 141. 194. 174
Deutsche Telekom AG
100213. 23. 94. 34
Mannesmann Arcor Telecommunications AG & Co
10087. 152. 211. 169
10091. 52. 99
10077. 14. 208
Vodafone Kabel Deutschland
100173. 212. 240. 169
10080. 134. 140. 223
10091. 86. 41. 210
Mobistar Cable
100107. 15. 114. 147
Charter Communications
10069. 124. 199. 107
Cablevision Systems Corp.
10091. 237. 161. 215
Global Polska Tomasz Zaplacinski – Sieniawa
10062. 48. 26
MEO – SERVICOS DE COMUNICACOES E MULTIMEDIA S. A.
10066. 189. 98. 114
Spectrum
100185. 178. 239. 195
ITCOMP sp. z o. o
1005. 61. 34. 49
LeaseWeb DE
10091. 103. 79. 165
JSC “Rosintel”
10098. 116. 57. 70
MCI Communications Services, Inc. d/b/a Verizon Business
10073. 159. 37
Comcast Cable Communications, LLC
10079. 168. 207. 223
NOS Comunicacoes S. A.
10096. 56. 158
Static IP Services
100108. 35. 16. 83
10067. 243. 217. 48
Charter Communications Inc
10069. 118. 218. 161
10073. 249. 223. 147
10084. 63. 91. 207
ARCOR-IP
100108. 21. 60. 117
100104. 226. 29. 18
Frontier Communications Solutions
10085. 241. 43
PT Comunicacoes S. A
100109. 132. 247. 224
Proximus
1002. 80. 105. 183
10024. 145. 120. 138
Atlantic Broadband Finance, LLC
10024. 146. 184
10024. 231. 148
Community Antenna Service, Inc.
10031. 71. 170
NEANET Lukasz Lugowski
10037. 2
Polkomtel S. A
10050. 137. 178
10067. 82. 180
10068. 160. 2
10069. 201. 30. 88
10071. 66. 74
10072. 69. 148. 89
10073. 234. 161
10074. 65. 108. 253
10074. 102. 6
10075. 130. 142
10077. 26. 84
Vodafone Czech Republic
10077. 64. 244. 108
PRIMACOM
10078. 153. 104. 93
OzdKabel-Tv
10079. 175. 235. 59
SMSNET Sosnowiec
10084. 90. 95. 169
Nowo Communications
10085. 246. 173
PT Comunicacoes S. A.
10087. 10. 208
Telecom Italia S. p. A. IPTV
10089. 154. 205. 210
NOS COMUNICACOES S. A
10093. 39. 25
Fastweb SpA
10094. 12. 137
10095. 196. 53
10095. 1
10098. 112. 92
10098. 209. 148
100144. 31
100144. 100. 67
PT Comunicacoes
100176. 254. 221
Firma Tonetic Krzysztof Adamczyk
100178. 19. 179. 233
TB Telecom Sp. o.
100178. 255. 174. 140
Starnet s. r. o.
100185. 14
GreenLan Fiber Sp. o. Sp. k.
100185. 238. 206. 234
Kampinos telco Sp. o.
100188. 13. 122. 139
Telecom Italia S. A
100188. 157. 65
Magyar Telekom
100188. 251. 91
100193. 59. 80
Bajtnet Spolka Z Ograniczona Odpowiedzialnoscia
100194. 33. 77. 229
SPEED-NET Arkadiusz Broniecki
100194. 76. 231
Men Danil Valentinovich
100194. 66
INTERBUSINESS
100198. 46. 67
ColoCrossing
100207. 223
RCN
100212. 88. 227. 171
Telenet BVBA
100212. 185. 222. 54
100213. 98
OnCloud SAS
10037. 6. 177
Vodafone
10095. 247
10093. 151. 95
VODAFONE
10095. 78. 231
10073. 253. 252
Comcast Cable Communications
10073. 47. 231
10066. 31. 87. 52
10024. 208
10073. 136. 107
10024. 1
10024. 182. 105
10066. 59
Google LLC
10089. 215. 189
Network
10094. 177. 233. 143
10094. 97
10094. 242. 201
10094. 219
10094. 36
10094. 76
10089. 40. 40
IP Address data partner
Proxy data sponsored by IP2Proxy:
IMPORTANT: Scamalytics Ltd operate a fraud-detection network with visibility into many millions of internet users per month. We do not have visibility into the entire internet. The statements on this page represent our opinion based on the limited information we have available to us, and specifically only cover web connections made by internet users to websites and applications, not other connections such as server to server connections.