
Security Headers Io
Introducing SecurityHeaders.io – Scott Helme
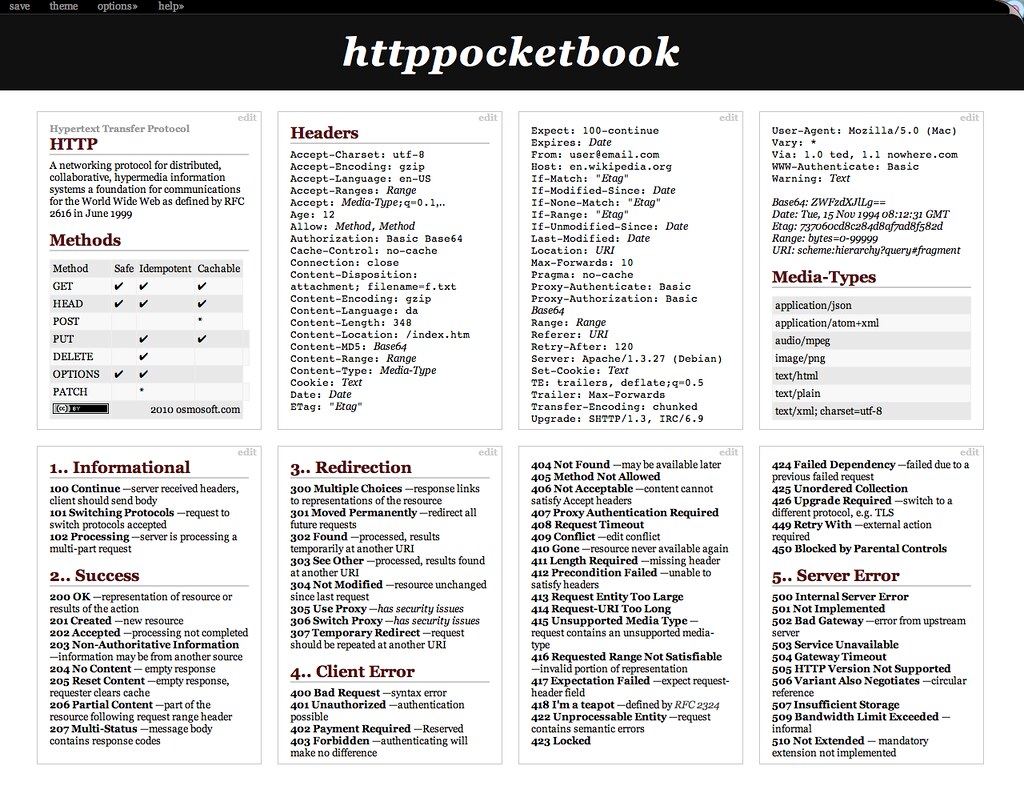
HSTS
Scott Helme
Security researcher, entrepreneur and international speaker who specialises in web technologies.
More posts by Scott Helme.
2 Feb 2015
• 2 min read
After looking around for a quick and easy way to analyse the HTTP response headers of websites, I regularly found myself looking in Chrome Dev Tools. This isn’t the most user friendly method of extracting this information and trying to ascertain just what was going on wasn’t always easy. This is what lead me to create
Introduction
Have you ever wanted to know if a site issues a HTTP Strict Transport Security header? What about if they’re using Content Security Policy, HTTP Public Key Pinning or perhaps the X-Frame-Options header? When these questions came up, I would invariably find myself looking in either the Chrome Developer Tools or sat at a command line using cURL. Whilst both of these methods would retrieve the raw information required, there was still a level of analysis required and neither of them presented the information in a user friendly format. This is where steps in.
Simplicity
To check the HTTP response headers for any site, simply navigate over to, insert the domain of the site you want to scan and hit the ‘Scan’ button.
After that, it’s a simple case of casting your eyes over the easy to read report!
Results
The results of the scan are colour coded to make it easier to identify security based headers and there are more details about each header further down the page.
I’ve placed in a couple of quick links in so you can easily scan the same domain again over HTTP/HTTPS, depending on the scheme of the current scan, and implemented a basic API to pull and display the raw headers should you need them.
Feedback
The site is still in beta, but all feedback is welcome and you can find my email address at the top of the page. If you find the service useful or have any suggestions, you can also drop a comment in the comments section below. I know there’s nothing groundbreaking going on here, but I couldn’t find anything that quite fit the bill and this site was intended to just fill that gap. It’s free to access, requires no account or registration and at present, there is no rate limiting either! Enjoy!
If you want to get notified when I publish a new blog, please consider subscribing!
Tags: HSTS, HTTP, HTTPS, CSP, HPKP,, response headers
Configure HTTP security headers
Security headers are directives used by web applications to configure security defenses in web browsers. Based on these directives, browsers can make it harder to exploit client-side vulnerabilities such as Cross-Site Scripting or Clickjacking. Headers can also be used to configure the browser to only allow valid TLS communication and enforce valid certificates, or even enforce using a specific server certificate.
The sections below detail the various security headers and support for them in Deep Security:
Customizable security headers
Enforced security headers
Unsupported security headers
The following headers can be enabled and configured based on specific environment requirements:
HTTP Strict Transport Security (HSTS)
Content Security Policy (CSP)
HTTP Public Key Pinning (HPKP)
As the primary tenant, you can Enable customizable security headers in the Deep Security Manager or Reset your configuration.
HTTP Strict Transport Security is a header that configures the web browser to always use a valid secure connection with the web application. If the server TLS certificate suddenly becomes expired or untrusted, the browser will no longer connect to the web application. Also, if the user attempts to access the web application using an url, the browser will automatically change it to. These countermeasures help prevent Man-in-the-middle attacks as well as other attacks such as Session Hijacking.
On install, the Deep Security Manager console has a self-signed (untrusted) certificate and HSTS is turned off. This is because each organization must configure the Deep Security web application with a specific certificate that matches the manager hostname. This can also be achieved by configuring a Load Balancer with TLS termination such as AWS ELB/ALB.
Once a valid TLS configuration is in place, the HTTP Strict Transport Security Header can be enabled from Administration > System Settings > Security.
For instructions on enabling HTTP Strict Transport Security (HSTS), see Enable customizable security headers.
Content Security Policy includes a comprehensive set of directives that help prevent client-side attacks, such as Cross-Site Scripting and Clickjacking, by restricting the type of content the browser is allowed to include or execute.
Enabling CSP can have adverse effects. For example, embedded scripts might stop working or certain types of images required by third-party components such as jQuery might not load.
When you enable CSP, it is always a good idea to run it in Report only first and observe if any violations are reported to the provided URL for expected application functionality.
The Deep Security CSP can be configured under Administration > System Settings > Security.
Deep Security works best with the following settings:
default-src ‘self’
script-src ‘self’ ‘unsafe-eval’ ‘unsafe-inline’
frame-src ‘self’
frame-ancestors ‘self’
style-src ‘self’ ‘unsafe-inline’ blob:
form-action ‘self’
img-src ‘self’ data:
report-uri By default, the Report only check box is selected. Once you confirm that the CSP does not break the expected application functionality, you can deselect Report only to enforce the policy.
For instructions on enabling Content Security Policy (CSP), see Enable customizable security headers.
The HPKP header forces browsers to only trust a specific certificate or certificate authority for secure communications. This prevents attacks that leverage a trusted certificate authority which has been compromised or maliciously installed on the client.
Enabling HPKP can leave browsers unable to connect if a certificate is changed without its header also being changed.
For instructions on enabling HTTP Public Key Pinning (HPKP), see Enable customizable security headers.
Enable customizable security headers
In multi-tenant mode, security header settings are only available to the primary tenant.
Go to Administration > System Settings > Security.
Enter your HTTP Strict Transport Security (HSTS), Content Security Policy (CSP), or HTTP Public Key Pinning (HPKP) directive(s) in the corresponding field(s). Before you enable settings, you can test them by selecting the Report Only option and verifying that the policy violation reports are can enter individual policy directives on separate lines.
Click Save at the bottom of the page.
Reset your configuration
If you experience trouble while configuring your directive and cannot correct it in the Deep Security Manager, SSH into the manager and run the corresponding commands to reset your configuration:
HTTP Strict Transport Security
dsm_c -action changesetting -name nfiguration. enableHttpStrictTransportSecurity -value “”
dsm_c -action changesetting -name nfiguration. enableHttpStrictTransportSecurity -value “false”
Content Security Policy
dsm_c -action changesetting -name ntentSecurityPolicy -value “”
dsm_c -action changesetting -name ntentSecurityPolicyReportOnly -value “true”
Public Key Pinning Policy
dsm_c -action changesetting -name licKeyPinPolicy -value “”
dsm_c -action changesetting -name licKeyPinPolicyReportOnly -value “true”
The following headers are enforced by default and cannot be changed:
Cache-Control and Pragma
X-XSS-Protection
X-Frame-Options
These headers configure how the browser caches content. Caching sensitive content from an authenticated application can be a security vulnerability if the content is cached on a machine that is used by multiple users or if an attacker gains access to an unlocked machine after the user has logged out of the application. For this reason, Deep Security disables caching on all content that is not static by enforcing the no-cache and no-store values.
This XSS-Protection header forces the browser’s Cross-Site Scripting (XSS) heuristics to detect XSS attacks. Deep Security enforces this header in block mode by default. This means that if the browser detects a potential XSS attack it will stop the page from loading altogether—a safer approach than the alternative of trying to sanitize the page by replacing potentially malicious elements.
XSS-Protection does not work for all types of attacks and not all browsers have an XSS filter.
This header helps to prevent Clickjacking attacks. The Deep Security Manager enforces the SAMEORIGIN value for this header, only allowing it to be embedded in web applications that are hosted on the same domain.
This header has the same effect as the frame-ancestors CSP directive. The frame-ancestors directive will override the value of the X-Frame-Options header.
The following header type is unsupported.
X-Content-Type-Options
This header with the nosniff value helps protect against mime type sniffing. Mime type sniffing attacks are only effective in specific scenarios where they cause the browser to interpret text or binary content as HTML. For example, if a user uploads an avatar file named and the web application does not set a Content-type header when serving the image, the browser will try to determine the content type and will likely treat as an HTML file. The attacker can then direct users to and conduct a Cross-Site Scripting attack.
Deep Security does not currently support enabling this header as it has been observed to cause adverse effects on redirects, however the relevant attack scenarios are not likely to impact the manager web application and its usual functionality.
Configure HTTP security headers
Security headers are directives used by web applications to configure security defenses in web browsers. Based on these directives, browsers can make it harder to exploit client-side vulnerabilities such as Cross-Site Scripting or Clickjacking. Headers can also be used to configure the browser to only allow valid TLS communication and enforce valid certificates, or even enforce using a specific server certificate.
The sections below detail the various security headers and support for them in Deep Security:
Customizable security headers
Enforced security headers
Unsupported security headers
The following headers can be enabled and configured based on specific environment requirements:
HTTP Strict Transport Security (HSTS)
Content Security Policy (CSP)
HTTP Public Key Pinning (HPKP)
As the primary tenant, you can Enable customizable security headers in the Deep Security Manager or Reset your configuration.
HTTP Strict Transport Security is a header that configures the web browser to always use a valid secure connection with the web application. If the server TLS certificate suddenly becomes expired or untrusted, the browser will no longer connect to the web application. Also, if the user attempts to access the web application using an url, the browser will automatically change it to. These countermeasures help prevent Man-in-the-middle attacks as well as other attacks such as Session Hijacking.
On install, the Deep Security Manager console has a self-signed (untrusted) certificate and HSTS is turned off. This is because each organization must configure the Deep Security web application with a specific certificate that matches the manager hostname. This can also be achieved by configuring a Load Balancer with TLS termination such as AWS ELB/ALB.
Once a valid TLS configuration is in place, the HTTP Strict Transport Security Header can be enabled from Administration > System Settings > Security.
For instructions on enabling HTTP Strict Transport Security (HSTS), see Enable customizable security headers.
Content Security Policy includes a comprehensive set of directives that help prevent client-side attacks, such as Cross-Site Scripting and Clickjacking, by restricting the type of content the browser is allowed to include or execute.
Enabling CSP can have adverse effects. For example, embedded scripts might stop working or certain types of images required by third-party components such as jQuery might not load.
When you enable CSP, it is always a good idea to run it in Report only first and observe if any violations are reported to the provided URL for expected application functionality.
The Deep Security CSP can be configured under Administration > System Settings > Security.
Deep Security works best with the following settings:
default-src ‘self’
script-src ‘self’ ‘unsafe-eval’ ‘unsafe-inline’
frame-src ‘self’
frame-ancestors ‘self’
style-src ‘self’ ‘unsafe-inline’ blob:
form-action ‘self’
img-src ‘self’ data:
report-uri By default, the Report only check box is selected. Once you confirm that the CSP does not break the expected application functionality, you can deselect Report only to enforce the policy.
For instructions on enabling Content Security Policy (CSP), see Enable customizable security headers.
The HPKP header forces browsers to only trust a specific certificate or certificate authority for secure communications. This prevents attacks that leverage a trusted certificate authority which has been compromised or maliciously installed on the client.
Enabling HPKP can leave browsers unable to connect if a certificate is changed without its header also being changed.
For instructions on enabling HTTP Public Key Pinning (HPKP), see Enable customizable security headers.
Enable customizable security headers
In multi-tenant mode, security header settings are only available to the primary tenant.
Go to Administration > System Settings > Security.
Enter your HTTP Strict Transport Security (HSTS), Content Security Policy (CSP), or HTTP Public Key Pinning (HPKP) directive(s) in the corresponding field(s). Before you enable settings, you can test them by selecting the Report Only option and verifying that the policy violation reports are can enter individual policy directives on separate lines.
Click Save at the bottom of the page.
Reset your configuration
If you experience trouble while configuring your directive and cannot correct it in the Deep Security Manager, SSH into the manager and run the corresponding commands to reset your configuration:
HTTP Strict Transport Security
dsm_c -action changesetting -name nfiguration. enableHttpStrictTransportSecurity -value “”
dsm_c -action changesetting -name nfiguration. enableHttpStrictTransportSecurity -value “false”
Content Security Policy
dsm_c -action changesetting -name ntentSecurityPolicy -value “”
dsm_c -action changesetting -name ntentSecurityPolicyReportOnly -value “true”
Public Key Pinning Policy
dsm_c -action changesetting -name licKeyPinPolicy -value “”
dsm_c -action changesetting -name licKeyPinPolicyReportOnly -value “true”
The following headers are enforced by default and cannot be changed:
Cache-Control and Pragma
X-XSS-Protection
X-Frame-Options
These headers configure how the browser caches content. Caching sensitive content from an authenticated application can be a security vulnerability if the content is cached on a machine that is used by multiple users or if an attacker gains access to an unlocked machine after the user has logged out of the application. For this reason, Deep Security disables caching on all content that is not static by enforcing the no-cache and no-store values.
This XSS-Protection header forces the browser’s Cross-Site Scripting (XSS) heuristics to detect XSS attacks. Deep Security enforces this header in block mode by default. This means that if the browser detects a potential XSS attack it will stop the page from loading altogether—a safer approach than the alternative of trying to sanitize the page by replacing potentially malicious elements.
XSS-Protection does not work for all types of attacks and not all browsers have an XSS filter.
This header helps to prevent Clickjacking attacks. The Deep Security Manager enforces the SAMEORIGIN value for this header, only allowing it to be embedded in web applications that are hosted on the same domain.
This header has the same effect as the frame-ancestors CSP directive. The frame-ancestors directive will override the value of the X-Frame-Options header.
The following header type is unsupported.
X-Content-Type-Options
This header with the nosniff value helps protect against mime type sniffing. Mime type sniffing attacks are only effective in specific scenarios where they cause the browser to interpret text or binary content as HTML. For example, if a user uploads an avatar file named and the web application does not set a Content-type header when serving the image, the browser will try to determine the content type and will likely treat as an HTML file. The attacker can then direct users to and conduct a Cross-Site Scripting attack.
Deep Security does not currently support enabling this header as it has been observed to cause adverse effects on redirects, however the relevant attack scenarios are not likely to impact the manager web application and its usual functionality.
Frequently Asked Questions about security headers io
What are the security headers?
Security headers are directives used by web applications to configure security defenses in web browsers. Based on these directives, browsers can make it harder to exploit client-side vulnerabilities such as Cross-Site Scripting or Clickjacking.
How do I set http security headers?
Enable customizable security headersGo to Administration > System Settings > Security.Enter your HTTP Strict Transport Security (HSTS), Content Security Policy (CSP), or HTTP Public Key Pinning (HPKP) directive(s) in the corresponding field(s). … Click Save at the bottom of the page.
How can I see the header of a website?
How to view HTTP headers in Google Chrome?In Chrome, visit a URL, right click , select Inspect to open the developer tools.Select Network tab.Reload the page, select any HTTP request on the left panel, and the HTTP headers will be displayed on the right panel.Jan 21, 2016


