Free Proxy Server For Utorrent

Why you should NEVER use Free Proxy servers for Torrenting
All over the internet, I see forum threads recommending the use of free HTTP proxies for torrents and I cringe. At their best, free proxy servers are crowded and slow, and at worst they’re downright dangerous.
Because 99% of them don’t work to hide your IP address from Torrent Peers (which is how torrents are monitored).
Not only is it crazy to trust a total stranger (offering you free service) with your privacy, but most free proxy servers are technologically incompatible with BitTorrent protocol.
This article will teach you about the reality of ‘free’, the limitations of HTTP/HTTPS proxies, and the potential dangers of giving total strangers access to your data stream.
Instead do this: consider choosing a torrent-friendly VPN like NordVPN (which also includes torrent-compatible SOCKS5 proxy servers).
INTRODUCTION TO FREE PROXIES
There are numerous websites with lists of free proxy servers, often sorted by country or uptime. A few examples are,, and
These are public proxy servers, accessible by anyone who knows the address and port number (listed on the website).
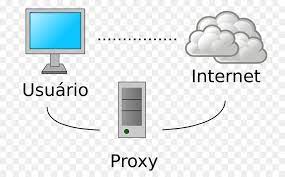
What is a Proxy?
A proxy is a data tunnel that is routed from you computer to a 3rd party (proxy server) before reaching the internet. The proxy is the middleman, and if used properly can help hide your identity from whoever is on the other end of your connection.
A proxy is generally configured to work with a specific program, not your entire internet connection. Common programs configured with a proxy are:
A Web Browser – To get through firewalls are access geo-blocked sites like ttorrent Client Software – To prevent ip-based torrent monitoring
When used properly, a proxy allows you to do 2 things while torrenting:
Change your visible locationHide your real IP address from torrent peers and trackers
One notable thing a proxy lacks compared to a VPN, however, is encryption.
Types of Proxy Servers
There are a few different proxy ‘protocols’ that you’ll see in free proxy lists. Each one is designed to handle and transport different types of data (they are not created equal).
The most common proxy types are:
HTTP: Transports regular non-encrypted HTTP web traffic, such as web browser The encrypted version of an HTTP proxy, it wraps the proxied traffic in a layer of encryption making it difficult for a middleman (like your ISP) to read the traffic. SOCKS5: The all purpose proxy protocol. It can transport both UDP & TCP packets, and can hold any type of data, including HTTP, Video, Files, and p2p/torrent data.
IMPORTANT TO NOTE: Bittorrent traffic is not HTTP, so it’s not compatible with HTTP/S proxies. If you try to use an HTTP proxy with your torrent client, it will simply ignore the proxy rules for peer communications and expose your IP address (bad! )
Reasons your should Avoid ‘Free Proxy’ servers
There are tons of amazing free things on the internet. In our experience, proxy service is not one of them.
The reasons to avoid free proxy servers range from inconvenience to genuine risk.
Slow: Free proxy servers are overcrowded and have hundreds or thousands of users sharing the limited bandwidth. Speeds below 0. 1Mbps are Protocol: The fast majority of free servers available are HTTP or HTTPS. This doesn’t work with BitTorrent peer communications, so torrent peers (and monitoring firms) will still see your real IP address in swarms. What you need is a SOCKS5 Proxy. Unreliable: Free servers crash or go offline constantly. You’ll have frequent connection errors, and the proxy may even go down mid-torrent (which could leak your identity depending on your torrent client’s settings). Dangerous: Free proxies cost money to run, but give full access to users’ data-stream. This attracts unsavory characters some free servers may be BitTorrent honeypots, Hacker Honeypots, or data-mining operations.
Now if that list isn’t enough to convince you, I’m not sure what is.
But if you’re ready to join our community of informed (and secure) BitTorrent fans, read on…
Free Proxy Alternatives: a Zero-Log VPN or SOCKS5 Proxy
By far the best tool for anonymizing your torrent downloads is a non-logging, torrent-friendly VPN service.
A VPN has all the benefits of a proxy service, plus additional security features:
Strong Torrent Encryption: Encrypt your torrents and browsing so your Internet provider has not idea what you’re doing Leak ProtectionZero-log Privacy: No logs or record of your online activity or IP address historyEasy-to-use Software
VPNs are hugely popular within the torrent community, thanks to the peace of mind and privacy they provide. They even allow you to get around torrent-blockades if your country (or firewall) has them.
And all 3 of our recommended VPNs actually include zero-log SOCKS5 proxy service at no additional charge.
1. NordVPN (Includes SOCKS5 proxy in 10 p2p-enabled locations) | from $2. 99/month
NordVPN is now the fastest zero-log VPN in the world, thanks in large part to their insane $2. 99/month offer, which is 70% off the normal monthly price.
Based in Panama, NordVPN has less exposure to the governmental pressures of companies located in the Five Eyes countries, like the USA, Canada, UK and Australia.
And NordVPN is quite torrent-friendly. They have p2p-optimized servers in more than 10 countries, a dual-mode kill-switch for security, and included SOCKS5 Proxy service.
Oh, and NordVPN isn’t blocked by Netflix or Hulu (unlock most VPNs).
2. Other great options (that also include a FREE Proxy)
There are two other VPN services that we highly recommend, both of which include a Netherlands-based logless SOCKS5 proxy (in addition to full VPN service).
1: IPVanish – They’re the leaders in speed, and have excellent software for Windows/Mac/iOS/Android and even a Firestick app (for Kodi).
Related: Read our IPVanish review
2: Private Internet Access – PIA is the gold standard and the godfather of the zero-logging movement. They’ve beaten the FBI in court and take customer privacy incredibly seriously. Bonus: PIA is one of the only VPNs with built-in port forwarding.
Related: Read our Private Internet Access review
David started torrenting before it was cool. He enjoys hiking, strategy games and eats watermelon year round. He still rocks his Napster t-shirt once a month.

Torrent Proxy: How to set up a proxy for your torrents? (2021 …
A torrent proxy allows you to share torrents anonymously. For instance, proxies like the popular SOCKS5 can be more cost-efficient than VPNs and yet provide a similar security level.
In this torrent proxy guide, you’ll learn the advantages, use cases, and configuration of proxies. You’ll also learn the why and when of using a proxy vs a VPN for torrenting. Plus, we’ll also go through the step-by-step proxy setup in torrent clients, such as uTorrent, qBittorrent, and Deluge.
This guide intends to help you maximize your anonymity and privacy while torrenting with proxy servers.
In a nutshell, a SOCKS5 proxy server should be enough to provide you with adequate anonymity and speed. All it takes is configuring your torrent client with the optimal settings and that your proxy server comes from a reliable provider.
Table of Contents.
The benefits of using a proxy for would a proxy do for your torrent client? What type of proxy to use for torrenting? Configuring proxy in a torrent client. uTorrent proxy up a proxy for up a proxy in to set up proxy in to set up proxy in up SOCKS5 proxy in to configure proxy settings on other torrent clients? Final Words
1. The benefits of using a proxy for torrenting.
Proxy servers were designed to simplify complex distributed networks by centralizing requests and responses. There are many types of proxies used for different use cases, but the two most common are HTTP and SOCKS5 proxies. These two proxies provide a different degree of anonymity and functionality.
Obviously, using free proxies or VPNs will not give you an advantage. There are many reasons to get a paid proxy service, but the most important is that service providers will protect your identity, provide support, and provide you with more resources (dedicated or regulated).
a. Benefits of a proxy for torrenting.
Hide your true identity behind the proxy’s identity. So, when you are participating in a torrent swarm and using a torrent tracker, the IP address visible to your peers will be the anonymous proxy’s, and not yours. With the adequate proxy, tracing your torrenting activity back to you (source IP) can be extremely rare and difficult to achieve.
b. Mask your identity (IP).
When you route the traffic of your torrent client, including uTorrent, BitTorrent, Vuze, or qBittorrent, via an anonymous proxy server, your torrent traffic gets a new identity. The P2P and torrent tracker communications are handled by the proxy, and not by your client’s source IP. Having this flexibility, allows you to use segregate your Internet traffic based on application. For example, you could use your normal IP for web browsing and the proxy’s IP for torrenting.
c. Faster torrent transfer.
A proxy server can be an extremely efficient way to hide your identity within torrent swarms and trackers and still get decent download speeds. Proxies lack encryption overhead, so they are generally faster than VPNs, but less secure. For more on this comparison and more, check our deep VPNs vs proxies comparison.
d. Won’t keep logs.
Traffic logs could be the only way to link a proxy’s IP activity to your IP, and the proxy server provider is the only one with access to these logs. However, the advantage of paid proxy service providers is that they do not keep those logs. On the other hand, free proxy servers might even be free due to the fact that they sell data logs to third-party marketing, advertising, or law firms.
e. Support and allow torrent traffic.
The majority of proxy providers do allow torrent traffic. As long as you are using a SOCKS5 proxy, all your torrent traffic can be routed towards the proxy server.
2. What would a proxy do for your torrent client?
As mentioned earlier, without a proxy, peers sharing a singular torrent file will be able to see the identity (public IP address) of every other peer within a torrent swarm. Obviously, this isn’t a bad thing. After all, giving your IP is how P2P operates and shares information. But having your public IP address exposed in this way isn’t a good thing when torrent swarms (especially in public trackers) are filled up with ill-intentioned hackers or copyright trolls.
Without a proxy, any IP disclosed in the swarm, can be easily logged and then ran through IP traceback technology.
With those popular geolocation services or IP traceback technology, most IP addresses can be traced to their country of origin, town, ISP, and sometimes even to a home address.
With a Proxy?
Your participation in the torrent swarm and communications with the tracker server will happen through the proxy’s IP. Your uTorrent or BitTorrent client will forward their traffic to the proxy so that it uses its identity to talk to the torrent swarm and tracker.
What wouldn’t a proxy do?
A proxy does not encrypt traffic in the same way a VPN does. Obviously, this has its disadvantages and advantages. First, not using encryption makes your traffic “potentially visible” to the eyes of any middle-man, which includes your ISP, hackers, or government. Anyone could identify your torrent traffic via port numbers and throttle its bandwidth simply by setting up a packet sniffer or a Deep Packet Inspection (DPI) device at the first or middle mile.
For example, my Vuze torrent client is using a listening port, 25849 UDP. Someone could set a Wireshark packet trace to a set of network interfaces and then filter for that specific could read my interface IP (public or private) and the destination IP (a peer in the torrent swarm). This shows that someone within the network is using a P2P application. A proxy does not encrypt the contents of this traffic, especially port information and data.
The advantage of not using encryption is simply the lower overhead. Compared to VPNs, proxy servers are much faster and efficient for those bandwidth-intensive traffic applications, like P2P and torrenting.
3. What type of proxy to use for torrenting?
There are different types of proxies out there. The most frequent and available are HTTP and SOCKS5, which can be used for a wide variety of applications. But when it comes to torrenting, SOCKS5 can be a much better option.
SOCKS5 vs HTTP proxies for torrenting.
Technically, you could use HTTP/HTTPS proxies for torrenting, but these are designed for anonymous HTTP web browsing (port 80 or 443). You’ll have to configure your torrent client to use these web browsing ports, which can be good because they are generally not blocked by ISPs, but they will likely leak torrent data easily. Plus, HTTP proxies transport the entire hypertext data, which makes it slower.
SOCKS5 proxy servers are recommended over the HTTP proxies for torrenting.
Why?
SOCKS5 works at the session (layer 5 of the OSI model) level, which means they don’t rewrite requests or responses, and they are not forced to use a specific protocol, as layer 7 proxies do (HTTP). SOCKS5 can be used for web browsing, torrenting, gaming, file transferring, etc. The SOCKS5 may be used with authentication. SOCKS5 proxies are the only type of proxy that provides optional authentication. With this feature, only authorized users may access the SOCKS5 proxy server. User/password authentication mechanisms for SOCKS5 are defined in RFC1929.
4. Configuring proxy in a torrent client.
So now, you know why you need to mask your identity and the benefits of using a SOCKS 5 proxy. It is time to configure the proxy information in your torrent client.
To configure a proxy, you’ll need the IP address (or hostname) of the proxy, port number, and in some cases, authentication. But bear in mind that not all torrent clients allow proxy configuration.
The popular torrent clients with build-in proxy settings include:
uTorrent BitTorrentqBittorrentDelugeVuzeTixati.
Some of these torrent clients provide a great degree of flexibility and added security when configuring a proxy. For example, you can configure your client to use the proxy only for peer connections. This option will ensure that your home IP address does not leak peer connections. In addition, you can also only choose your client to use the proxy for tracker communications.
Some torrent clients allow you to disable connections not supported by proxies. For example, when a peer connection does not support the proxy, it will likely drop the connection, making your ISP or anyone in between notice. Instead, disabling all these connections that do not support proxy will help avoid leaks.
5. uTorrent proxy setup.
uTorrent is a multiplatform torrent client, supported by Microsoft Windows, Linux (server version only), macOS, and Android. You can get uTorrent through different consoles, including uTorrent Web, uTorrent mobile, uTorrent Remote, and uTorrent Desktop classic and Pro.
Some of these uTorrent clients do allow changing the proxy settings, but not all.
uTorrent Web and uTorrent Mobile won’t let you modify the proxy settings. uTorrent Desktop classic and uTorrent Pro do support proxy configuration.
How to set up SOCKS5 proxy in uTorrent for Windows?
To configure uTorrent proxy in your Windows machine:
Go to “Options > Preferences > Connection > Proxy Server. Here you’ll be able to select the type of Proxy Server (SOCKS5), the proxy IP or domain, port (SOCKS is usually 1080), and then authentication (if required). Check “use proxy for peer connections” and “disable connections not supported by proxies. ”
To improve your anonymity level when setting a uTorrent proxy:
The uTorrent proxy configuration can be improved with additional features. In addition to the previous selection, if you want to enhance your anonymity, you can also do the following:
In uTorrent’s Connection window, check the “Use proxy for hostname lookups” option. Rather than having your client resolve hostnames in plain text, make the client forward DNS queries to the SOCKS5 proxy. This option avoids potential DNS leaks. Check “Use proxy for peer-to-peer connections. ” Choose this option so the proxy’s IP is used on the peer-to-peer connection. Check everything under “Proxy Privacy. ” These settings below “Proxy privacy” will help you avoid potential IP leaks. Click on “Apply” > “Ok” > and restart your client.
6. How to set up a proxy for BitTorrent.
Although BitTorrent and uTorrent look alike, they do have some differences like size and number of releases. The BitTorrent client is supported by Android, iOS, Linux, macOS, and Windows. Plus, BitTorrent has the following versions, Android, Classic, and Web. You can only modify the proxy settings in the BitTorrent Classic and Pro versions.
To configure a proxy for the BitTorrent classic client, follow these steps:
Go to “Options > Preferences > Connection > Proxy Server. Enter the BitTorrent proxy server information, including IP or hostname, port, and credentials (if required) the two options: “use proxy for peer connections” and “disable connections not supported by proxies. ”
Similar to uTorrent’s configuration, check the following options to avoid IP leaks. Improve the Bit torrent proxy configuration with the following features.
Check the “Use proxy for hostname lookups” and “Use proxy for peer-to-peer connections” options. Check everything under “Proxy Privacy. ”Click on “Apply” > “Ok” > and restart your client.
7. How to set up proxy in qBittorrent.
qBittorrent is a popular cross-platform torrent client supported by: FreeBSD, Linux, macOS, OS/2, and Windows. The current stable versions, as officially stated, are for the following platforms, Windows (7, 8, and 10), macOS (Mojave, Catalina, and Big Sur), and Linux (Source Tarball). Fortunately, you can configure your qBittorrent proxy in all these versions.
To set up the proxy on qBittorrent client for Windows:
Go to Tools > Options > Connection > Proxy Server. In the Proxy Server section, enter the type of proxy (HTTP or SOCKS5), the Host or IP address of the proxy server, and the port number. The proxy service provider should give you all this information. Check the “use proxy for peer connections. ” This option will ensure that your home IP address does not leak peer connections.
Setup qBitTorrent proxy for macOS?
Go to Preferences > Connection > Proxy Server. Enter the proxy’s information and check the “use proxy for peer connections”.
8. How to set up proxy in Deluge.
Deluge is another popular torrent client supported by FreeBSD, Linux, macOS, and Windows. Thankfully, you can configure Deluge proxy settings for any of these platforms. To optimize speed and improve anonymity, check this comprehensive guide to Deluge.
Configure the proxy on Deluge for Windows, using the following steps:
To open Deluge proxy settings, go to Preferences > Proxy.
As you notice, you’ll see four different sections to configure Proxy information in Deluge: Peer, Web Seed, Tracker, and DHT. A different approach on how to configure proxy settings compared to other torrent clients.
Side Note: Many experts in the area suggest that after libtorrent 0. 16, all the torrent traffic uses the proxy and not separate sections, as Deluge’s settings suggest. Libtorrent is an open-source implementation of the BitTorrent protocol. Its main features are the support for Mainline DHT, IPv6, HTTP seeds, and uTorrent’s peer exchange. Our recommendation is to update your Deluge torrent client and set your proxy information on all four sections. But, you can also update libtorrent for Deluge.
What is each of these Deluge proxy settings for? “Peer” to exchange torrent content with peers via proxy. “Web Seed” to share the contents of the torrent with a server. “Tracker” to exchange IP information with a tracker via proxy. “DHT” to share IPs with a Distributed Hash Table.
As suggested above, configure your Deluge Proxy settings on all four sections. Type your SOCKS5 username/password (if needed) and add the Host (Server IP) and port number.
9. How to set up proxy in Vuze.
Vuze is a fully-featured and robust BitTorrent client, supported by Linux, Windows, Android, and OS X. Thankfully, you can configure Vuze proxy in all of these platforms.
Set up a SOCKS5 proxy in Vuze for Windows:
To configure Vuze proxy, go to Tools > Options > Connection > Proxy. If you can’t access the “Proxy” option, you’ll need to enable the advanced configuration. Go to Options > Mode > and click on “Advanced” to unlock full access to all settings and features. Expand “Connection” settings again and choose Proxy.
Vuze divides the proxy configuration into two sections: Tracker Communications and Peer Communications.
Check on “I have a SOCKS5 proxy” and on “Enable proxying of tracker communications [restart required]. ” These two options ensure that the torrent tracker you are connecting to uses the proxy’s IP and not the SOCKS5 proxy’s configuration, including Host, port (1080), and authentication (if required).
Check on the “Enable proxying of peer communications (outgoing connections only)” box. Although not mandatory, “Check on “inform tracker of limitation. ” Choose the SOCKS version as “V5” on the dropdown menu. Check on the “Use same proxy settings for tracker and peer communications proxy” box. Leave the rest by default, and click on Save. Vuze has this great feature that allows you to test the SOCKS proxy connection right from the configuration panel. Go ahead and test your proxy connection!
Once connected to the SOCKS5 proxy, Vuze will show a small connectivity status icon on the bottom of the interface in the status area. You can also see the detailed SOCKS5 connection information in the statistics view.
Set up SOCKS5 proxy in Vuze, for macOS:
The Vuze macOS client uses a similar GUI to Windows.
To change your Vuze proxy settings for macOS: Go to Options > Preferences > Connection > Proxy. To unlock proxy settings, go to Mode, then click on Connection > Proxy, enable both Tracker and Peer Communications for maximum anonymity. Vuze separates these two types of torrent connections so that you can separate proxying for tracker proxying of peer your SOCKS5 proxy information, and choose V5 as the SOCKS version. At this point, you can Test your proxy connection.
If you tick on “Use the same proxy setting for tracker and peer communications proxy, ” you won’t have to enter the information again.
Leave the rest by default and restart your torrent back to your Vuze client and test the connection of your SOCKS5 proxy.
Once connected to the SOCKS5 proxy, Vuze will show a small connectivity status icon on the bottom of the interface. In addition, you can also see the detailed SOCKS5 connection information in the statistics view.
To see the connection details of your proxy.
Tools > Statistics > the top right, you’ll see the SOCKS panel. Click on “more. ”This window will show you the proxy’s connection stats.
10. Set up SOCKS5 proxy in Tixati.
Tixati is a Linux and Window BitTorrent client designed for light computer resources. Like all other torrent clients, Tixati has built-in proxy support. But there is a difference, Tixati only supports TCP connections going out through the proxy, which means that UDP traffic won’t be forwarded to the proxy. UDP is essential for P2P features, including DHT and Magnet links.
If you decide to use a proxy on Tixati, bear in mind that only TCP connections will be routed through the proxy. All non-supported UDP connections will not use the proxy tunnel, so there is the risk of getting your IP exposed.
To configure the Tixati proxy settings:
Disable DHT and UDP. Since Tixati does not route UDP-based peer-to-peer traffic through the proxy, you should disable DHT and UDP trackers to prevent IP leaks. Disabling UDP connections will not affect your torrenting experience, as long as your proxy provider provides good TCP to Settings > DHT > Disable DHTGo to Settings > Transfers > Disable UDP trackers.
Enter Tixati proxy information. Now, go to Settings > Network > Proxy. In addition, notice that Tixati proxy settings point out the lack of UDP support with “TCP Outgoing Connection Proxy” and the below IMPORTANT note. Select SOCKS5 proxy, and enter the proxy’s information. Tick on “Use proxy to resolve names, ” if you want the SOCKS5 proxy to resolve the hostname to IPs. The reason for this is that DNS uses either TCP or UDP, so even if you are using a proxy, UDP connections might leak your IP. If you enable this feature, the name resolution will be taken care of by the SOCKS5 proxy.
11. How to configure proxy settings on other torrent clients?
Not all popular clients support proxy configuration. In fact, some popular clients have deprecated its support due to data leaks, while others have maintained it. Below is a brief list of the current landscape of proxy support on popular torrent clients.
Transmission: A popular macOS client that used to support proxy configuration. Proxy support in Transmission was deprecated on version 1. 4. Unfortunately, there is no plan to implement proxy support in this client after version 1. Ticket 3688. rTorrent: No support for proxy configuration. tTorrent: Android torrent client that does support proxy configuration. Open tTorrent > Top left Menu > Settings > Network Settings > Proxy Settings. Tick the “Use Proxy” box > click on Proxy Settings > enter the Proxy information. BitComet: Supports HTTP/HTTPS and SOCKS5. To set up proxy on BitComet: From the BitComet client, go to Tools > Options > Proxy > Enter your proxy configuration. Leave the rest of the options unchecked, except for “DNS query using proxy server”. BitLord: Supports HTTP/HTTPS and SOCKS5. To set up proxy on BitLord: go to Options > Preferences > Connection > Proxy. Enter your proxy’s configuration.
Final Words.
Using a torrent proxy is the best idea if you want to remain anonymous without compromising torrent speed and performance. Using a VPN while torrenting obviously has the benefit of encryption and IP masking, but generally, if configured properly, a SOCKS5 proxy from a reliable provider (not free) should be as secure as a VPN (if not more).
The most popular torrent clients, like BitTorrent, uTorrent, Deluge, qBittorrent, Vuze, etc., come with built-in proxy setting support. You can, not only configure proxy settings for these clients but also set up additional options to lower the risk of a data leak.
Get an IPv6 and IPv4 proxy to improve the torrenting experience and anonymity. Rapidseebox, offers, optimized, anonymous, IPv6, and IPv4 proxies for everyday use and with a 24-hour money-back guarantee.

Socks5 Proxy Setup for uTorrent
The socks5 proxy appears to be broken on uTorrent for OSX.
ttps Setup uTorrent on MS Windows 1. Open your uTorrent client. 2. Click on Options and then press Preferences.
3. A new window pops up. Click on Connection.
4. On the Proxy Server section choose the Type Socks5 5. For Proxy, enter one of our VPN servers addresses, that allows torrent traffic. (Click to find our VPN Server List) 6. For Port type 1080 and make sure you check the following boxes: Authentication, Use proxy for hostname lookups, Use proxy for peer-to-peer connections, Disable all local DNS lookups, Disable features that leak identifying information, Disable connections unsupported by the proxy. 7. Type in your Username and Password in the authentication fields and press OK You have just set up Socks5 for uTorrent. If you want to check whether it really works, here is what you have to do: 1. Go to this website
2. Copy “Magnet link” address and open it in uTorrent client. 3. The file ipMagnet Tracking Link starts synchronizing.
4. While the file is connecting to peer return to the ipMagnet website. A new IP address, the one that you chose, appears.
As you can see, it is the IP address of VPN server which indicates uTorrent is downloading files through VPN proxy thus ensuring your downloads to be hidden and secured.
Did this answer your question?
Thanks for the feedback
There was a problem submitting your feedback. Please try again later.
Last updated on December 7, 2020
Frequently Asked Questions about free proxy server for utorrent
How do I setup a proxy server on uTorrent?
Setup uTorrent on MS WindowsOpen your uTorrent client.Click on Options and then press Preferences.A new window pops up. … On the Proxy Server section choose the Type Socks5.For Proxy, enter one of our VPN servers addresses, that allows torrent traffic. (More items…•Dec 7, 2020
What is uTorrent proxy server?
New Torrent Proxy Software & Servers This new anonymous bittorrent app automatically configures the optimal security settings with popular torrent clients like uTorrent, Bittorrent, Deluge or Vuze.
Is proxy safe for Torrenting?
The best/most-secure proxy type for torrenting is Socks5 (don’t use HTTP proxies). A proxy allows your Torrent IP address to be different than the IP for all other internet traffic (good). Unfortunately, most torrents don’t encrypt their traffic, so your ISP could still monitor your downloads if they wanted to.Jul 5, 2017


