Tor Proxy Server List

Online proxy lists – hidemy.name
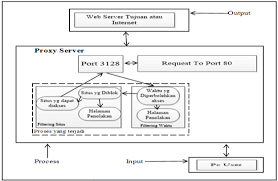
All proxies are thoroughly and regularly checked for ping, type, country, connection speed, anonymity, and uptime by the number of checks. Exporting the proxy list in the IP:Portformat and API access are available with the paid oxies are needed when using a VPN is either impossible or inconvenient. For example, when mass action is required from multiple IP addresses simultaneously, such as parsing, increasing views, visits, removing limits on the number of requests from online services, oxies from our list do not belong to us. They are collected automatically by the “spider robot” from thousands of different sites on the internet, including closed forums and even some private proxy note that these are not our own proxies, so we can not be held responsible for their performance and stability, but only show their status at the time of verification. The right column in the list shows how long ago the check was proxy servers in the list are checked and sorted according to various example, the type of proxy depends on how you will be able to use it. Here are the types:HTTP: regular proxies that support HTTP requests. You can use them to view websites and download files over Also called SSL-enabled proxy servers. Allow you to view HTTPS sites. Using specialized programs, they can be used for any protocol, like SOCKS proxy 4: Proxies that support the SOCKS protocol version 4. They can be used to connect over TCP / IP protocol to any address and 5: Includes all the features of version 4. Additional features include use of the UDP Protocol, the ability to make DNS requests through a proxy, and use of the BIND method to open the port for incoming anonymity is a very important parameter. This determines whether your real address will be hidden and whether or not the destination server will suspect that you’re using a proxy. Anonymity categories that are in our proxy list:No anonymity: The remote server knows your IP address and knows that you are using a anonymity: The remote server does not know your IP, but knows that you are using a proxy. Average anonymity: The remote server knows that you are using a proxy and thinks that it knows your IP, but it is not yours (these are usually multi-network proxies that show the remote server the incoming interface as REMOTE_ADDR) anonymity: The remote server does not know your IP, and it has no direct evidence that you are using a proxy. These are anonymous speed is indicated in milliseconds, but it is not a ping. You can see how fast a small text file was uploaded via proxy. The easiest way is to focus on the color of the strip: green is fast, and red is ping will vary. If this is an important parameter for you, it is better to check it directly from the device where the proxy will be owners of paid subscription, you can download the proxy list in and formats, as well as get API access. You can request access to the API from technical support.
Tor browser proxy. Andvantages and disadvatages of free tor …
Most people are of the opinion that TOR is a cent percent private and safe way to get on the World Wide Web without being traced. Is this fact or just a rumor? There are many ways to find out the answer for that. However, not all the sites case of it.
The truth is that TOR does not really provide the privacy and anonymity solution. It has various other limitations coupled with risks that one needs to be aware of before making use of it.
The Exit Nodes are possibly sniffed
On using tor, the internet traffic passes through the tor’s network and then makes way through the various selected relays even before it exits the Tor’s network. The whole idea of using tor is to not identify the computer used. The computer used might have only initiated the first connection or could have possibly acted as a relay that is relying on the encrypted traffic to other Tor nodes. But the truth is that most of the traffic would have to emerge straight from the Tor network. For instance, if one is connected via Tor to Google, then this traffic gets passed through many Tor relays, however, it eventually rises from the tor network and gets connected to the servers of Google. The very last Tor node, when the traffic is left by the Tor network on entering the free Internet gets monitored. The particular node, wherein the traffic exits the network of Tor is known as the exit relay or the exit node.
The exit nodes are much riskier than the relay node which passes the traffic. It is very likely of the government to go ahead with the exit nodes and then monitor the amount of traffic which leaves it.
This poses much more than a theoretical risk. When making use of Tor always ensures that the HTTPS sites are encrypted especially when the site contains sensitive matters. The traffic would be tracked and this would not only be done by the government but also by anti social elements of the society so as to access the private data.
Plug-ins, JavaScript and other Apps that leak the IP
The browser bundle of Tor, comes with certain preconfigured settings which are secured. When the JavaScript gets disabled, the plug-ins are in no position to run, the browser would also give off warning signals when you attempt to get a file downloaded and then have it opened in another application.
If you are making efforts to handle your IP then using JavaScript must be avoided. Making use of JavaScripts like the various plug-ins, flash etc. can create leaks and hence a link to your real IP.
The Tor browser bundles get rid of all the issues with the help of its default settings however, one could even potentially disable such protections and make use of the Javascript or the plug-ins in the browser of Tor. Do not perform this setting if you are not sure about anonymity. Then again, if anonymity is not your criteria then making use of Tor is not required in at all.
This is not a mere theoretical risk. One must leave the browser of Tor in the security settings mode. Making use of Tor on any other browser should be avoided. The Tor bundle should be made use of which has already been preconfigured having the ideal settings already. No other apps should be made use of when using Tor.
Donating the bandwidth by means of running the Tor relay is the best way to remain anonymous. This does not come with a set of legal problems. A tor relay is nothing by but the passing on of the encrypted traffic up and down, within the Tor network, Anonymity is facilitated through the various relays that volunteers steer.
An exit relay is a risky option and should hence be thought over several times before running the relay. The relay is nothing but the place where the traffic from Tor comes out of its anonymous network and then connected back to the open net.
If the antisocial elements of the society make use of services like Tor, they can easily track your IP address.
The biggest risk that is involved with the running of the Tor exit nodes is that it is not a everyone piece of cake. The project has been running successfully. Suggestions are always welcome but it is advised not to try this task.
TorGuard SOCKS5 Network
Anonymous VPN
Business VPN
Private Email
VPN Routers
LOGIN
DOWNLOAD JOIN
TorGuard SOCKS5 is best used inside torrent clients.
« Global Network
AnyConnect Network »
SOCKS5 Locations
SOCKS5 IP Addresses
UDP Support
Ports
Canada
68. 71. 244. 6
1080/1085/1090
68. 10
68. 14
68. 18
68. 22
68. 26
68. 30
68. 34
68. 38
68. 42
68. 46
68. 50
68. 54
68. 58
68. 62
68. 66
68. 70
68. 78
68. 82
68. 90
68. 94
68. 98
68. 102
USA – NY
37. 120. 214
37. 230
37. 218
37. 226
37. 202
37. 222
37. 206
37. 198
37. 210
37. 194
Netherlands
37. 141. 114
37. 122
46. 23. 78. 24
46. 25
88. 202. 177. 230
88. 231
88. 233
88. 232
88. 234
88. 235
88. 237
88. 238
88. 239
88. 240
88. 241
88. 242
88. 243
185. 156. 172. 154
2. 58. 44. 226
89. 238. 202
89. 194
185. 198
185. 212. 171. 114
185. 118
Sweden
37. 153. 234
37. 242
194. 59. 250. 194
194. 202
194. 210
194. 218
194. 226
194. 234
194. 250
Payment Types Accepted
Credit cards Cryptocurrency
Frequently Asked Questions about tor proxy server list
Is TOR a proxy server?
Mobile compatibility. As mentioned above, proxies apply on a per-application basis. … The sole official mobile solution for Tor is an Android-only app — there’s no way for iOS users to access Tor on their phones and tablets without turning to intermediary apps.Mar 5, 2020
Where do I find proxy list?
Free Proxy List 2020 & Proxy Servers To Hide IP AddressFree Proxy – Best free proxy server to use for data scraping. … ProxyScrape – Popular Proxy site with ~10,000 free proxies. … ProxyNova – Free proxy list updated every 60 seconds. … SSL Proxy – Get free and working SSL proxies.More items…•Dec 1, 2020
How many proxies does Tor use?
Tor passes your traffic through at least 3 different servers before sending it on to the destination. Because there’s a separate layer of encryption for each of the three relays, somebody watching your Internet connection can’t modify, or read, what you are sending into the Tor network.