Sock Server
SOCKS – Wikipedia
SOCKS is an Internet protocol that exchanges network packets between a client and server through a proxy server. SOCKS5 optionally provides authentication so only authorized users may access a server. Practically, a SOCKS server proxies TCP connections to an arbitrary IP address, and provides a means for UDP packets to be forwarded.
SOCKS performs at Layer 5 of the OSI model (the session layer, an intermediate layer between the presentation layer and the transport layer). A SOCKS server accepts incoming client connection on TCP port 1080, as defined in RFC 1928. [1]
History[edit]
The protocol was originally developed/designed by David Koblas, a system administrator of MIPS Computer Systems. After MIPS was taken over by Silicon Graphics in 1992, Koblas presented a paper on SOCKS at that year’s Usenix Security Symposium, [2] making SOCKS publicly available. [3] The protocol was extended to version 4 by Ying-Da Lee of NEC.
The SOCKS reference architecture and client are owned by Permeo Technologies, [4] a spin-off from NEC. (Blue Coat Systems bought out Permeo Technologies. )
The SOCKS5 protocol was originally a security protocol that made firewalls and other security products easier to administer. It was approved by the IETF in 1996 as RFC 1928 (authored by: M. Leech, M. Ganis, Y. Lee, R. Kuris, D. Koblas, and L. Jones). The protocol was developed in collaboration with Aventail Corporation, which markets the technology outside of Asia. [5]
Usage[edit]
SOCKS is a de facto standard for circuit-level gateways (level 5 gateways). [6]
The circuit/session level nature of SOCKS make it a versatile tool in forwarding any TCP (or UDP since SOCKS5) traffic, creating a good interface for all types of routing tools. It can be used as:
A circumvention tool, allowing traffic to bypass Internet filtering to access content otherwise blocked, e. g., by governments, workplaces, schools, and country-specific web services. [7] Since SOCKS is very detectable, a common approach is to present a SOCKS interface for more sophisticated protocols:
The Tor onion proxy software presents a SOCKS interface to its clients. [8]
Providing similar functionality to a virtual private network, allowing connections to be forwarded to a server’s “local” network:
Some SSH suites, such as OpenSSH, support dynamic port forwarding that allows the user to create a local SOCKS proxy. [9] This can free the user from the limitations of connecting only to a predefined remote port and server.
Protocol[edit]
SOCKS4[edit]
A typical SOCKS4 connection request looks like this:
First packet to server
VER
CMD
DSTPORT
DSTIP
ID
Byte Count
1
2
4
Variable
SOCKS version number, 0x04 for this version
command code:
0x01 = establish a TCP/IP stream connection
0x02 = establish a TCP/IP port binding
2-byte port number (in network byte order)
DESTIP
IPv4 Address, 4 bytes (in network byte order)
the user ID string, variable length, null-terminated.
Response packet from server
VN
REP
reply version, null byte
reply code
Byte
Meaning
0x5A
Request granted
0x5B
Request rejected or failed
0x5C
Request failed because client is not running identd (or not reachable from server)
0x5D
Request failed because client’s identd could not confirm the user ID in the request
destination port, meaningful if granted in BIND, otherwise ignore
destination IP, as above – the ip:port the client should bind to
For example, this a SOCKS4 request to connect Fred to 66. 102. 7. 99:80, the server replies with an “OK”:
Client: 0x04 | 0x01 | 0x00 0x50 | 0x42 0x66 0x07 0x63 | 0x46 0x72 0x65 0x64 0x00
The last field is “Fred” in ASCII, followed by a null byte.
Server: 0x00 | 0x5A | 0xXX 0xXX | 0xXX 0xXX 0xXX 0xXX
0xXX can be any byte value. The SOCKS4 protocol specifies that the values of these bytes should be ignored.
From this point onwards, any data sent from the SOCKS client to the SOCKS server is relayed to 66. 99, and vice versa.
The command field may be 0x01 for “connect” or 0x02 for “bind”; the “bind” command allows incoming connections for protocols such as active FTP.
SOCKS4a[edit]
SOCKS4a extends the SOCKS4 protocol to allow a client to specify a destination domain name rather than an IP address; this is useful when the client itself cannot resolve the destination host’s domain name to an IP address. It was proposed by Ying-Da Lee, the author of SOCKS4. [10]
The client should set the first three bytes of DSTIP to NULL and the last byte to a non-zero value. (This corresponds to IP address 0. 0. x, with x nonzero, an inadmissible destination address and thus should never occur if the client can resolve the domain name. ) Following the NULL byte terminating USERID, the client must send the destination domain name and terminate it with another NULL byte. This is used for both “connect” and “bind” requests.
Client to SOCKS server:
SOCKS4_C
DOMAIN
8+variable
variable
SOCKS4 client handshake packet (above)
the domain name of the host to contact, variable length, null (0x00) terminated
Server to SOCKS client: (Same as SOCKS4)
A server using protocol SOCKS4a must check the DSTIP in the request packet. If it represents address 0. x with nonzero x, the server must read in the domain name that the client sends in the packet. The server should resolve the domain name and make connection to the destination host if it can.
SOCKS5[edit]
The SOCKS5 protocol is defined in RFC 1928. It is an incompatible extension of the SOCKS4 protocol; it offers more choices for authentication and adds support for IPv6 and UDP, the latter of which can be used for DNS lookups. The initial handshake consists of the following:
Client connects and sends a greeting, which includes a list of authentication methods supported.
Server chooses one of the methods (or sends a failure response if none of them are acceptable).
Several messages may now pass between the client and the server, depending on the authentication method chosen.
Client sends a connection request similar to SOCKS4.
Server responds similar to SOCKS4.
The initial greeting from the client is:
Client greeting
NAUTH
AUTH
Byte count
SOCKS version (0x05)
Number of authentication methods supported, uint8
Authentication methods, 1 byte per method supported
The authentication methods supported are numbered as follows:
0x00: No authentication
0x01: GSSAPI (RFC 1961
0x02: Username/password (RFC 1929)
0x03–0x7F: methods assigned by IANA[11]
0x03: Challenge-Handshake Authentication Protocol
0x04: Unassigned
0x05: Challenge-Response Authentication Method
0x06: Secure Sockets Layer
0x07: NDS Authentication
0x08: Multi-Authentication Framework
0x09: JSON Parameter Block
0x0A–0x7F: Unassigned
0x80–0xFE: methods reserved for private use
Server choice
CAUTH
chosen authentication method, or 0xFF if no acceptable methods were offered
The subsequent authentication is method-dependent. Username and password authentication (method 0x02) is described in RFC 1929:
Client authentication request, 0x02
IDLEN
PWLEN
PW
(1-255)
0x01 for current version of username/password authentication
IDLEN, ID
Username length, uint8; username as bytestring
PWLEN, PW
Password length, uint8; password as bytestring
Server response, 0x02
STATUS
0x00 success, otherwise failure, connection must be closed
After authentication the connection can proceed. We first define an address datatype as:
SOCKS5 address
TYPE
ADDR
type of the address. One of:
0x01: IPv4 address
0x03: Domain name
0x04: IPv6 address
the address data that follows. Depending on type:
4 bytes for IPv4 address
1 byte of name length followed by 1–255 bytes for the domain name
16 bytes for IPv6 address
Client connection request
RSV
DSTADDR
0x01: establish a TCP/IP stream connection
0x02: establish a TCP/IP port binding
0x03: associate a UDP port
reserved, must be 0x00
destination address, see the address structure above.
port number in a network byte order
BNDADDR
BNDPORT
status code:
0x00: request granted
0x01: general failure
0x02: connection not allowed by ruleset
0x03: network unreachable
0x04: host unreachable
0x05: connection refused by destination host
0x06: TTL expired
0x07: command not supported / protocol error
0x08: address type not supported
server bound address (defined in RFC 1928) in the “SOCKS5 address” format specified above
server bound port number in a network byte order
Since clients are allowed to use either resolved addresses or domain names, a convention from cURL exists to label the domain name variant of SOCKS5 “socks5h”, and the other simply “socks5”. A similar convention exists between SOCKS4a and SOCKS4. [12]
Software[edit]
Servers[edit]
SOCKS proxy server implementations[edit]
Sun Java System Web Proxy Server is a caching proxy server running on Solaris, Linux and Windows servers that support HTTPS, NSAPI I/O filters, dynamic reconfiguration, SOCKSv5 and reverse proxy.
WinGate is a multi-protocol proxy server and SOCKS server for Microsoft Windows which supports SOCKS4, SOCKS4a and SOCKS5 (including UDP-ASSOCIATE and GSSAPI auth). It also supports handing over SOCKS connections to the HTTP proxy, so can cache and scan HTTP over SOCKS.
Socksgate5 SocksGate5 is an application-SOCKS firewall with inspection feature on Layer 7 of the OSI model, the Application Layer. Because packets are inspected at 7 OSI Level the application-SOCKS firewall may search for protocol non-compliance and blocking specified content.
Dante is a circuit-level SOCKS server that can be used to provide convenient and secure network connectivity, requiring only the host Dante runs on to have external network connectivity. [13]
Other programs providing SOCKS server interface[edit]
OpenSSH allows dynamic creation of tunnels, specified via a subset of the SOCKS protocol, supporting the CONNECT command.
PuTTY is a Win32 SSH client that supports local creation of SOCKS (dynamic) tunnels through remote SSH servers.
ShimmerCat[14] is a web server that uses SOCKS5 to simulate an internal network, allowing web developers to test their local sites without modifying their /etc/hosts file.
Tor is a system intended to enable online anonymity. Tor offers a TCP-only SOCKS server interface to its clients.
Shadowsocks is a circumvent censorship tool. It provides a SOCKS5 interface.
Clients[edit]
Client software must have native SOCKS support in order to connect through SOCKS. There are programs that allow users to circumvent such limitations:
Socksifiers[edit]
Socksifiers allow applications to access the networks to use a proxy without needing to support any proxy protocols. The most common way is to set up a virtual network adapter and appropriate routing tables to send traffic through the adapter.
Win2Socks, which enables applications to access the network through SOCKS5, HTTPS or Shadowsocks.
tun2socks, an open source tool that creates virtual TCP TUN adapters from a SOCKS proxy. Works on Linux and Windows, [15] has a macOS port and a UDP-capable reimplementation in Golang.
proxychains, a Unix program that forces TCP traffic through SOCKS or HTTP proxies on (dynamically-linked) programs it launches. Works on various Unix-like systems. [16]
Translating proxies[edit]
Polipo, a forwarding and caching HTTP/1. 1 proxy server with IPv4 support. Open Source running on Linux, OpenWrt, Windows, Mac OS X, and FreeBSD. Almost any Web browser can use it.
Privoxy, a non-caching SOCKS-to-HTTP proxy.
Docker based[edit]
multsocks, [17] an approach based on Docker which would run on any platform that runs Docker, using client, server, or both to translate proxies.
Security[edit]
Due to lack of request and packets exchange encryption it makes SOCKS practically vulnerable to man-in-the-middle attacks and IP addresses eavesdropping which in consequence clears a way to censorship by governments.
References[edit]
^ “Service Name and Transport Protocol Port Number Registry”. Internet Assigned Numbers Authority. 19 May 2017. Retrieved 23 May 2017.
^ Koblas, David; Koblas, Michelle R. SOCKS (PDF). USENIX UNIX Security Symposium III. Retrieved 16 November 2019.
^ Darmohray, Tina. “Firewalls and fairy tales”. ;LOGIN:. Vol 30, no. 1.
^ Archive index at the Wayback Machine
^ CNET: Cyberspace from outer space
^ Oppliger, Rolf (2003). “Circuit-level gateways”. Security technologies for the World Wide Web (2nd ed. ). Artech House. ISBN 1580533485. Retrieved 21 January 2020.
^ “2010 Circumvention Tool Usage Report” (PDF). The Berkman Center for Internet & Society at Harvard University. October 2010.
^ “Tor FAQ”.
^ “OpenSSH FAQ”. Archived from the original on 2002-02-01.
^ Ying-Da Lee. “SOCKS 4A: A Simple Extension to SOCKS 4 Protocol”. OpenSSH. Retrieved 2013-04-03.
^
^ “CURLOPT_PROXY”. Retrieved 20 January 2020.
^ “Products developed by Inferno Nettverk A/S”.. Retrieved 2021-03-20.
^ “Easy Net with SOCKS5”. ShimmerCat. Archived from the original on 2018-09-13. Retrieved 20 April 2016.
^ Bizjak, Ambroz (20 January 2020). “ambrop72/badvpn: NCD scripting language, tun2socks proxifier, P2P VPN”. GitHub. Retrieved 20 January 2020.
^ Hamsik, Adam (20 January 2020). “proxychains: a tool that forces any TCP connection made by any given application to follow through proxy like TOR or any other SOCKS4, SOCKS5 or HTTP(S) proxy”. Retrieved 20 January 2020.
^ Momm, Gregorio (2020-08-24), gregoriomomm/docker-multsocks, retrieved 2020-08-29
External links[edit]
RFC 1928: SOCKS Protocol Version 5
RFC 1929: Username/Password Authentication for SOCKS V5
RFC 1961: GSS-API Authentication Method for SOCKS Version 5
RFC 3089: A SOCKS-based IPv6/IPv4 Gateway Mechanism
Draft-ietf-aft-socks-chap, Challenge-Handshake Authentication Protocol for SOCKS V5
SOCKS: A protocol for TCP proxy across firewalls, SOCKS Protocol Version 4 (NEC)
How to Securely Bypass Blocks, Safe Torrenting, Free Proxy List …
The internet is in a strange place right now. It’s no longer the open, free place it used to be. Increasingly, users are being subject to website blocks, attacks, and surveillance. For true safety or anonymity, precautions must be taken. Thankfully, there many ways for you to protect yourself, one of them being Socket Secure (SOCKS) proxies.
While many have heard about SOCKS Proxies not many truly understand their purpose, how they work and the security-privacy levels they can offer. SOCKS proxies are often mistakenly considered an alternative or equivalent to VPNs causing major confusion amongst users and providing false sense of security.
In this article we’ll be covering a wealth of topics relating to SOCKS Proxies, SSL, Configuration advise, Torrenting via SOCK, compare them with VPNs and much more so let’s take a quick look at what we have in store before diving deeper:
Introduction to SOCKS Proxies
Understanding how HTTPS Encryption – SSL & HTTPS Proxies work
How SOCKS5 Proxy Works
Why Would I Use a SOCKS5 Proxy?
When to Use SOCKS5 Proxies, VPN or Both
Combine a SOCKS5 Proxy and a VPN
SOCKS5 Proxy vs VPN for Torrenting and P2P
Configuring SOCKS5 Proxy for Torrenting (qBittorrent, uTorrent)
Configuring Firefox and Chrome to Use SOCKS5 Proxy
Free Proxy vs Paid
Using SOCKS5 Proxy for US Netflix
Like HTTP, SOCKS is an internet protocol, but it offers a further degree of anonymity. Connecting to a SOCKS proxy routes your traffic through a third-party server via TCP, assigning you a new IP address in the process. Because the IP address is different, web hosts can’t determine the physical location.
This has the add-on effect of bypassing regional filtering. However, unlike a VPN, SOCKS doesn’t provide encryption. This means users don’t have true privacy and aren’t safe from attacks on Public WiFi and government surveillance. In addition, SOCKS doesn’t run through every application, meaning regular browsing is not always safe.
However, this lack of encryption does provide some benefits. The main one is speed. A SOCKS proxy doesn’t need resources to encrypt traffic and has far less overhead, so it’s usually faster than a VPN. Though proxies don’t provide protection from monitoring, they are a nice middle ground between HTTP and VPNs.
The security of a SOCKS proxy also depends on the version it utilizes. Most modern proxies use either SOCKS4 or SOCKS5 to protect users, and there are some fundamental differences. As you would expect from a lesser version, SOCKS4 has fewer features.
One example is the lack of support for UDP protocol-based applications. This cuts out programs that need faster, more efficient transfers, like games. SOCKS5 also supports IPv6 and Domain Name Resolution. This means the client can specify a URL rather than an IP address. This feature is also supported by SOCKS4a.
As well as SOCKS, users can utilize the HTTP/HTTPS proxy method. HTTP proxies work similarly to SOCKS5, but utilize the HTTP protocol instead. This is the same method that transfers data to your computer when you type. These proxies fetch and receive primarily in HTTP and are generally used for web browsers. Some applications support HTTP proxy, others SOCKS proxy, and many both. HTTP is more intelligent than SOCKS5, but also less secure.
Due to lack of UDP support and limited TCP support, HTTP proxies don’t fully support torrenting. Often, they will filter out this type of data or block it. This blocking is especially prevalent in public HTTP proxies. In addition, HTTP tries to re-write the headers of the data in transit. The result is extremely slow or non-existent torrenting.
Understanding How HTTPS Encryption – SSL & HTTPS Proxies Work
HTTPS proxies utilize something called the Secure Socket Layer. In your browser, you’ll notice this as a green padlock next to the URL bar:
In short, SSL creates a secure connection between the web server and the user’s browser. When you request a URL, the server sends your browser a copy of its SSL certificate. The browser verifies that it’s authentic, and the server then sends back a signed acknowledgment. Upon arrival, both start an SSL encrypted session and can share data safely.
This encryption uses a method called public key cryptography. A server using SSL has both a public key and a private key. When a server first negotiates an SSL session with a client, it sends a copy of its public key. The client’s browser verifies the certificate and then uses the public key to create a symmetric key which is then sent to the server. The private key is never sent and always kept secret.
The symmetric key is unique to the SSL session and used to encrypt/decrypt data exchanged between the client and server.
HTTPS proxy works slightly differently. Using the CONNECT method, requests are converted to a transparent tunnel. However, this feature isn’t available in a lot of proxies and, when it is, users can still be vulnerable.
Some versions of SSL are still open to attack through the Heartbleed bug. This serious vulnerability was discovered in 2014 and allows attackers to steal private keys from servers, eavesdropping on communications and gaining access to passwords, emails and instant messages. Vulnerabilities in SSL and its predecessor TLS have been found several times since then, including man-in-the-middle attacks that downgrade the user to a less secure version.
While an HTTP proxy is designed to work in the web browser, a SOCKS5 proxy is more wide-reaching. SOCKS sits on the higher levels of the OSI model, below SSL, which sits on the seventh application layer, and above TCP and UDP on the transport layer (Layer 4). This offers several advantages. TCP works by forming a physical connection between the client and the server, trying to guarantee that every packet arrives at the destination in the same order it was sent. To do this, it puts all the content into a fixed format.
Another use of UDP is in the Domain Name System (DNS), which allows for translation of URLs into IP addresses. The combination of both TCP and UDP creates a more flexible and reliable experience.
The low level of SOCKS5 also means it can handle several different request types: HTTP, HTTPS, POP3, SMTP and FTP. As a result, SOCKS5 can be used for email, web browsing, peer-to-peer and more. More importantly, users can do this in a somewhat anonymous fashion.
When you connect to a website, the traffic usually runs through a firewall on the router or by the ISP. A SOCKS5 proxy routes your data through its proxy server, creating a path through the network’s firewall. In doing so the user is assigned an IP address, which makes it look like they’re browsing from a different location and protects their identity.
As mentioned before proxies don’t encrypt data like a VPN, which means you can access these services with very little slowdown. This is because there is no need to re-write header data. This, in turn, leads to less chance of errors, and fewer errors means more speed.
Although it doesn’t handle encryption, SOCKS5 does provide methods of authentication, as mentioned earlier. In general, a SOCKS5 handshake looks like this:
The client sends a connection request, stating the list of authentication methods it supports.
The server looks at these methods and chooses one. In the case that none are acceptable, it sends a failure response.
Once accepted, information can pass between the client and server. The client can send a connection request and the server can respond.
This authentication removes many of the security concerns that plagued SOCKS4. The proxy isn’t open to anybody with the details, resulting in less chance of malicious attacks. Usually, authentication comes in the form of a simple username and password combination. However, SOCKS5 also supports GSSAPI (Generic Security Services Application Program Interface) and IANA methods.
Now that you know the features of SOCKS5 proxies, you may be wondering why you even need one. One of the main uses is to circumvent internet censorship. If your ISP blocks access to movie streaming websites, The Pirate Bay or other questionable content, a proxy will circumvent it. This can be useful on restricted networks. Work and school connections are often monitored and block access to social media, games, and anything else that isn’t relevant. Broad sweeping policies can often cause issues if you need to access one of those sites for research or you just want to slack.
You’ll also be able to access services that are limited to certain countries. BBC iPlayer, for example, is only available from a UK IP address. A proxy located in the UK would allow you to watch British TV without a TV license. This also applies to services like Netflix, which has significantly more content in the US region than others. Utilizing a SOCKS5 proxy from several different locations can significantly expand your viewing catalogue.
On home networks, users must be careful about their privacy, especially when torrenting. Using a SOCKS5 proxy can provide fast download speeds while adding a layer of protection against copyright holders. Many BitTorrent clients support a weak form of encryption when using SOCKS5, which prevents further obstacles.
SOCKS5 torrenting doesn’t offer the same protection as a VPN, but it’s better than nothing at all. In addition, it can give an obscured connection from only one application on your PC. As a result, you can perform fast P2P downloads while still using location services such as Google Maps. You’ll retain your normal download rate for any other browsing or streaming.
When to use SOCKS5 Proxies, VPNs or Both
For the privacy and security conscious, VPNs are a great option. They are superior to a SOCKS5 proxy in almost every way. The Best VPN Service Providers give unparalleled protection from government agencies, copyright holders and hackers. Many of them even provide proxy services as a free add-on. Other than speed, VPNs do everything SOCKS5 does and more. However, VPN subscriptions can be more expensive and require extra setup to run. In some situations, a proxy is the most economical option.
When it comes to accessing content with region restrictions, for example, a SOCKS5 proxy is great. You can easily spoof a different location, and don’t have to worry too much about security – repercussions are rare. You can find a proxy from almost every country on the planet, often free of charge. A VPN will provide the same benefit, but comes from a trusted provider who has put considerable thought into the safety and privacy of its users.
SOCKS5 proxies can hide your identity from web servers. Low stakes tasks like voting on polls multiple times from the same computer are fine. Most don’t make use of cookies or JavaScript to track the same browser across multiple IPs.
However, if you’re accessing blocked content, things are a little different. While a proxy is good for low stakes, it doesn’t remove identifying information other than the IP address. It’s open to snooping from anyone with access to your data stream, such as your ISP and government. Accessing censored file-sharing websites and other questionable content is best done through a VPN.
This lack of protection from those with network access can pose considerable risk in public. No encryption means little protection from prying eyes. On a WiFi hotspot, attackers can still see and interpret your data. Browsing websites without SSL encryption could result in password and information compromises. Furthermore, the previously mentioned security issues in SSL mean that hackers could get hold of it even then. For public WiFi safety, a VPN is the only true option.
It’s clear that there are some merits to using a proxy over a VPN. The extra speed makes them suitable for a wide range of low-risk tasks. It’s advantageous to be able to utilize both a VPN and a SOCKS5 proxy. Thankfully, any of the Best VPN service providers supply this at no extra cost. IPVANISH and Private Internet Access are great examples of this. Switching the two methods in and out is a no-brainer, but what about using both at once?
Using both in tandem usually results in increased privacy, if it’s supported by your VPN provider. Be that as it may, the benefits are limited. If a VPN is connected already, you probably won’t see speed increases. Instead, the advantage comes as a safety net. If your VPN cuts out and the Kill-Switch fails, you still have some protection from SOCKS5 VPN proxy, and vice versa. This is relevant if a provider hands over your details – the copyright holder will only see the IP address of the other service. Using both creates an extra barrier to entry.
For most users, this extra barrier is far from essential. A properly configured VPN should pose little problem. However, if you’re doing something particularly sensitive the combination is a good option. For the best security, you should email your provider and make sure your SOCKS5 VPN proxy has no logs.
Speaking of torrenting, it’s important to be aware of the benefits and limitations of using a VPN SOCKS5 proxy for it. SOCKS5 torrenting will show only the IP address of the proxy server if a media company is looking through a certain swarm and provides a small amount of encryption. This gives the small degree of protection mentioned earlier.
However, there are still many avenues of attacks for copyright holders. The encryption method torrent clients use is shaky and not reliable. It can be cracked quickly, revealing the information beneath. Although this wouldn’t reveal the user’s IP address, it could give information such as the version of the client, the operating system, settings and download speed. Copyright holders could use this to narrow down to an individual user and their ISP. They can then send a legal request to that ISP for information. The lack of proper encryption means the ISP can clearly see what a user is doing on its network.
SOCKS5 torrenting does provide an increase in speed, but it comes at a price. A determined copyright troll or government entity may still get leverage over the user. In the end, it’s up to the individual to decide if the speed increase is worth the risk. This will probably depend on how significant the difference is.
SOCKS5 VPN proxies come with an additional caveat. A fully-fledged VPN won’t just protect you from copyright holders, it will also bypass ISP throttling. It’s becoming increasingly common for service providers to set speed limits on peer-to-peer downloads, resulting in speeds that are as much as one fifth of normal speed. Service providers can only do this if they can interpret and categorize the data, so VPN encryption provides a natural wall.
Proxies do not generally provide encryption, and you may experience significant throttling. This can easily offset the speed gains of SOCKS5, so proxies are only the best option if your ISP does not throttle. You can test for throttling though web services like Glasnost. Even with the encryption built into torrent clients, most service providers can tell if you’re using P2P. If you’re unsure, you can always test with a free proxy.
Configuring SOCKS5 Proxy for Torrenting
Thankfully, setting up a SOCKS5 proxy for torrenting is very simple. It requires fewer steps than a VPN, and all you’ll need is a torrent client. In our examples, we’ll be showing uTorrent and qBittorrent, using a VPN SOCKS5 proxy from IPVANISH and Private Internet Access. Both providers give the functionality free of charge and provide a premium service and no logs policy.
Set up a SOCKS5 Proxy with IPVANISH and qBittorrent
To emphasise the divide between the two services, IP Vanish’s SOCKS5 details can’t be found in the regular VPN client. Instead, you’ll have to go to the My Account section of its website and click on the SOCKS5 Proxy tab.
You’ll want to note down these credentials for use later. The username and password are specific to you, and provide the SOCKS5 authentication mentioned earlier. The hostname,, is thanks to SOCKS5 and its Domain Name Resolution feature. If you’re using a different proxy, just take note of those details instead.
For an extensive review on PIA, including security tests, DNS Leak tests, Torrent Protection, Kill-Switch test, Netflix support and much more, read our Best VPN Review: Private Internet Access (PIA)
Now, in qBittorrent, head to Tools > Options. On the left-hand side, you’ll see the Connection tab. Click it. You should be presented with the following menu:
Under the Listening Port heading, disable Use UPnP/NAT-PMP port forwarding from my router. Then input the following details under Proxy Server:
Type: Socks5
Host:
Port: 1080
Use proxy for peer connections: Yes
Disable connections not supported by proxies: Yes
Use proxy only for torrents: Yes
Authentication: Yes
Username: IP Vanish SOCKS5 generated username
Password: IP Vanish SOCKS5 generated password
For extra privacy, head to BitTorrent and change Encryption mode to Require encryption. This will force the in-application encryption discussed earlier. Also tick Enable anonymous mode. This will remove the peer ID from the client’s fingerprint and force all incoming connections through SOCKS5.
Finally, hit Apply and Okay. Restart qBittorrent just to be safe.
Set up a SOCKS5 Proxy with Private Internet Access and uTorrent
Finding your SOCKS5 VPN proxy settings for Private Internet Access is equally simple. Go to the client sign in page and login with your username and password. Scroll down until you see a heading with the label PPTP/L2TP/SOCKS Username and Password. Click Generate Username and Password and note down the details:
The hostname isn’t listed here, but a support article reveals that it’s that down too, or the details of your free proxy. Launch uTorrent and go to Options > Preferences (Ctrl + P).
Under the Connection subheading, disable Enable UPnP port mapping and Enable NAT-PMP port mapping. Then enter the following settings under Proxy Server:
Type: SOCKS5
·Proxy:
Username: PIA SOCKS5 user
Password: PIA SOCKS5 password
Use proxy for hostname lookups: Yes
Use proxy for peer-to-peer connections: Yes
Disable all local DNS lookups: Yes
Disable all features that leak identifying information: Yes
Disable connects unsupported by the proxy: Yes
To enable encryption, go to the BitTorrent subheading and look under the Protocol Encryption menu. Change Outgoing to Forced. Be aware that this could impair your ability to connect to peers. Click Apply and OK. SOCKS5 torrenting is now enabled.
Configuring your browser to use SOCKS can be a little more difficult. At this moment in time, neither Chrome nor Firefox support SOCKS5 with authentication by default. Instead, you can use the Maxthon browser. After install go to Settings > Advanced > Proxy Settings.
Now tick Use custom proxy setting and hit Manage Proxy. Click Add. Fill in the fields as follows:
Name: IPVanish SOCKS5
Address:
Hit OK. Below the config, you’ll see a Bypass proxy server for heading. Here you can set exceptions for websites for which you need to keep your local IP, such as Google Maps. You can also switch this to Use proxy server for and only use the VPN SOCKS5 proxy on certain websites.
Though premium paid SOCKS5 proxies like the one above are often best, it’s possible to get one free of charge. Many websites even compile free proxy lists that are open for anyone to use. Here are just a few examples:
If you already have a VPN, you may have access to a free SOCKS5 proxy without even knowing it. It’s becoming increasingly common for the Best VPN service providers to offer this service. Some of the major ones include:
IPVANISH – Netherlands
Private Internet Access – Netherlands
NordVPN – 25 Severs across multiple countries
It may be tempting to just grab the first free SOCKS proxy you see, but there are a few things to consider. A free anonymous proxy isn’t going to be fast. It’s more common for download speeds to sit in the kilobytes rather than megabytes. You’ll also notice far less reliability, so you’ll probably have to switch between different servers for long downloads. This unreliability extends to response time.
In addition, a free anonymous proxy often lacks security. In many cases, they have no security at all, leaving users open to hackers. In many cases free providers keep logs, which may cause issues for P2P downloads and other illegal activities.
In all, you’ll be hard pressed to find a good, reliable free proxy. If you want to protect your identity, paying is almost essential. In some cases, you can pick up a full VPN service for the same price or less than premium SOCKS5 services, making it a no-brainer. You’ll have access to strong encryption when you need it, and a proxy when you’re just looking for speed.
One of the best uses of a SOCKS5 proxy is for Netflix. The catalogue of the service has been limited of late, and people outside the US seem to be particularly affected. Thankfully, you can trick Netflix into giving you shows from regions across the world. Here’s my Netflix UK homepage before using a proxy:
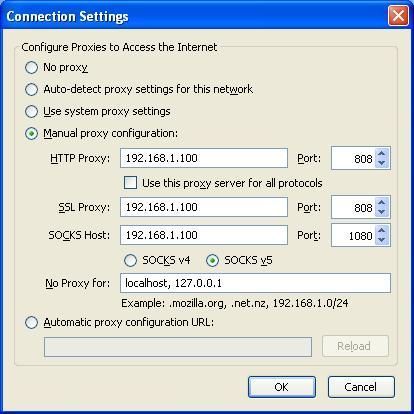
In this example, we’ll be using Firefox. Go to the flyout menu on the top right, then select Options. Go to Advanced and click the Network tab. Under Connection > Configure how Firefox connects to the Internet, click Settings…
First, change Configure Proxies to Access the Internet to Manual proxy configuration. Under SOCKS Host enter the URL or IP address of your proxy server. Under Port, enter the number your Netflix SOCKS5 proxy has provided. Tick SOCKS v5 and Proxy DNS when using SOCKS v5.
You can now click OK and head to. You should immediately notice a change in your browsing catalogue.
Unfortunately, those with a free SOCKS proxy may get stuck here. Netflix monitors proxy lists and blocks them to stop users accessing content they aren’t supposed to. You’ll know if you receive the following error when trying to play a show:
Trying to access Netflix US via Free SOCKS Proxy fails
You may be able to find a free proxy that Netflix hasn’t gotten around to yet, but it’s quite unlikely. A paid, private SOCKS5 proxy is less likely to be blocked, as the provider changes things often. You should notice much faster buffering times, so it’s worth paying the small monthly fee.
Most VPN SOCKS5 proxies use authentication, which isn’t supported by Firefox or Google Chrome. Instead, you’ll want to use the previously mentioned Maxthon browser method. This should give you fast, unblocked access to different films.
Summary
While SOCKS5 proxies offer better protection than HTML or nothing at all, they don’t shield the user from spying by ISPs or government. Free anonymous proxies offer even less protection, and can be open to hackers, cut out, or have slow download speeds. However, subscription-based proxies remain a great way to bypass regional blocks and carry out other, low-risk tasks.
Unfortunately, the price of a standalone SOCKS5 proxy is high compared to other services. In many cases, users can get a VPN subscription from IPVANISH or Private Internet Access and a VPN SOCKS5 proxy for the same monthly fee. This gives users access to the full, hardened security of a VPN, while also providing a fast, less secure proxy if they need it. At this moment in time, VPN providers like PIA, IPVANISH and NordVPN offer superior value for money.
Back to VPN Guides and Articles Section
SOCKS vs HTTP Proxy: What Is the Difference? – Blog | Oxylabs
Choosing between a SOCKS vs HTTP proxy requires a thorough understanding of how each type works and what configurations they convey. Only then you will be able to easily juggle between different types of proxies, as well as to find the best option for your specific use case.
In this article, we will outline what HTTP and SOCKS proxies are, how they operate, and what benefits each brings. Also, we will compare both proxy types and dwell on the differences between SOCKS proxies vs HTTP proxies.
Navigation:What are HTTP proxies? What are SOCKS proxies? Reasons to use SOCKS and HTTP proxies SOCKS vs HTTP proxies: the main differencesWrapping up
What are HTTP proxies?
HTTP stands for HyperText Transfer Protocol and is the foundation of any data exchange across the internet. It is a connectionless text-based protocol that allows fetching resources, like HyperText Markup Language (HTML) or other scripting languages, like CSS, and transmitting from web servers to web browsers.
HTTP is generally called a client-server protocol since it helps clients (usually web browsers) send requests to servers for data elements, such as pages, images, or videos. After the request is served, the connection between the web browser and server ends. Therefore, each request requires a new connection.
As the name implies, an HTTP proxy is specifically made for HTTP connections and operates via the same client-server model. Like any other regular proxy, it also acts as an intermediary: HTTP proxy stands between a server and a client (web browser) by transmitting requests and delivering the resource back to the client in HTTP format.
HTTP proxies can help cover many business use cases with high security and privacy
What are SOCKS proxies?
SOCKS is another internet protocol. It stands for SOCKet Secure and is commonly used for traffic-intensive tasks, like content streaming or P2P sharing. SOCKS uses a Transmission Control Protocol (TCP) connection that is designed to send and receive data packets across the internet, as well as to guarantee successful delivery of resources over networks.
When using SOCKS proxies, the internet traffic is routed through a proxy server via TCP connection on behalf of a client. Just like most other proxy types, SOCKS proxies hide the client’s IP address and serve when bypassing geo-restrictions.
Unlike HTTP, SOCKS cannot interpret web data. However, they are mostly used to facilitate communication with websites that have a firewall and limit regular client access. Most importantly, SOCKS proxies work on any kind of network protocol on any port.
What is SOCKS5? SOCKS5 is the latest edition of the SOCKS protocol. Compared with the older versions, SOCKS5 supports TCP or UDP connections and provides enhanced security.
Reasons to use SOCKS and HTTP proxies
Now we are going to outline why you should use SOCKS or HTTP proxies.
HTTP proxies are a reliable choice for many businesses that need to cover numerous goals and use cases. The HTTP proxy’s server configuration can be set according to your needs. Here are the main pros of using an HTTP proxy:
Clean data. While operating as a middleman between a client and its destination, an HTTP proxy has the ability to understand data. This means that an HTTP proxy can be set up for content filtering or caching web data. Therefore, HTTP proxies help extract relevant data from websites and avoid collecting what is unnecessary. Advanced security. HTTP proxies add an additional layer of security while detecting and denying suspicious data packets, such as spyware or malformed content, trying to enter your crease your scraper’s success rate. HTTP proxies are used for configuring HTTP request headers. This practice can help you to facilitate access to restricted targets and lower your chances of getting blocked. If you are interested in how to enhance your web scraping operations, read our article on “5 Key TTP Headers for Web Scraping. ”
Since SOCKS proxies are compatible with any network protocol or port, they can be used in multiple applications and in a wealth of scenarios. We have listed several reasons why SOCKS proxies can be beneficial:
Firewalls. As we already mentioned, SOCKS proxies can be an excellent choice for cases that involve firewalls. Whenever clients are behind a firewall and want to initiate arbitrary TCP connections to servers that are outside, they might not be able to. This is where SOCKS proxies come to play and make it happen. (In fact, this also applies to HTTP proxies – the firewall may restrict a client’s access to certain websites via an HTTP connection. )Compatibility with any network protocol or port. Unlike an HTTP proxy that establishes only an HTTP connection, SOCKS can go through TCP. Also, SOCKS5 proxies can use User Datagram Protocol (UDP) connection to deliver datagrams over a network, ensuring efficient performance.
SOCKS vs HTTP proxies: the main differences
The final decision on which proxy type you should choose depends mostly on your goals and needs. Equipped with the knowledge of both proxy types, we can now highlight their main differences.
Security
Ensuring privacy and security play an important role in the whole purpose of using a proxy. Both HTTP and SOCKS proxies act as mediators between a client and a server in order to secure your online activities and make them harder to be traced.
HTTP proxies are widely used for email protection and cybersecurity projects due to their ability to understand data packets and filter them according to specific needs. This also can be useful for web scraping and data mining activities.
Functionality
Although HTTP proxies can only handle HTTP(S) traffic, their configurations can be set according to numerous use cases. Since HTTP proxies can interpret network traffic between a client and a web server, they can spot repeated requests or cache responses.
As for SOCKS proxies, they are not liable to specific network protocols, thus can be more flexible to employ. As they are unable to understand network traffic, they are perfect for accessing connections behind the firewall.
Performance
As with any other proxy type, we generally advise on choosing private proxies if speed measures are of great importance to to their ability to filter data or cache web pages, HTTP proxies can fuel your scraping operations, as well as enhance load speeds and performance. As a result, these proxies allow you to manage more requests per second.
On the other hand, SOCKS proxies are widely appreciated for their speed as they are easier to apply: this makes them a right fit for downloading, transferring, and uploading web data online.
SOCKS proxyHTTP proxySecuritySOCKS proxies do not have standard tunnel proxies can add a layer of security between the client and the server and can detect and deny suspicious data packets or ctionalitySOCKS proxies do not directly use the HTTP protocol. It is commonly used for more general purposes such as content streaming and P2P file sharing. Since SOCKS proxies are protocol-agnostic, unlike HTTP proxies, they do not directly interpret or manipulate proxied proxies are more flexible to deploy as they are not bound to specific network protocols. They are great for accessing connections that are behind a proxies handle HTTP(S) traffic which is often used for retrieving information via web browsers. However, they can be configured for different use cases. HTTP proxies can interpret network traffic between web servers and clients. Thus, they can be set up to filter content or cache web rformanceSOCKS proxies offer great speeds, making them ideal for downloading or transferring data via the rare software clients or very specialized systems may only support ivate HTTP proxies deliver decent load speeds and are better suited for managing more requests per second.
Wrapping up
There is no question of rivalry since selecting between SOCKS vs HTTP proxies depends on your use case and needs. SOCKS may be a reliable choice for projects that involve downloading and transferring large amounts of data. On the other hand, HTTP proxies may be ideal for filtering data for security or performance reasons. If in doubt, if your target is HTTP(S), HTTP proxies should work just fine for you. Oxylabs’ HTTP proxies are considered as one of the most stable proxy types on the market.
If you want to learn more about web scraping, read our step-by-step Python Web Scraping Tutorial. And if you consider which solution meets your business needs, do not hesitate and contact our sales team for further advice and assistance.
About Vejune Tamuliunaite
Vejune Tamuliunaite is a Product Content Manager at Oxylabs with a passion for testing her limits. After years of working as a scriptwriter, she turned to the tech side and is fascinated by being at the core of creating the future. When not writing in-depth articles, Vejune enjoys spending time in nature and watching classic sci-fi movies. Also, she probably could tell the Star Wars script by heart.
All information on Oxylabs Blog is provided on an “as is” basis and for informational purposes only. We make no representation and disclaim all liability with respect to your use of any information contained on Oxylabs Blog or any third-party websites that may be linked therein. Before engaging in scraping activities of any kind you should consult your legal advisors and carefully read the particular website’s terms of service or receive a scraping license.
Frequently Asked Questions about sock server
How do you use a sock server?
Under SOCKS Host enter the URL or IP address of your proxy server. Under Port, enter the number your Netflix SOCKS5 proxy has provided. Tick SOCKS v5 and Proxy DNS when using SOCKS v5. You can now click OK and head to http://netflix.com.
What is the difference between HTTP and SOCKS proxy?
HTTP proxies can add a layer of security between the client and the server and can detect and deny suspicious data packets or spyware. SOCKS proxies do not directly use the HTTP protocol. It is commonly used for more general purposes such as content streaming and P2P file sharing.Jun 8, 2021
What is a VPN sock?
A SOCKS5 proxy is a private alternative to a VPN that protects the traffic within a specific source, such as an application. … SOCKS5 is the most recently optimized version of SOCKS; an internet protocol that funnels web traffic through a remote server.


