Rproxy
fireeye/RProxy – GitHub
RProxy is a reverse proxy server written with performance and scale in mind.
Dependencies
Libevent
Libevhtp
OpenSSL
Libconfuse
Building with all dependencies compiled and statically linked
cd build
cmake -DRPROXY_BUILD_DEPS:STRING=ON..
make
Build using system-wide dependencies
cmake..
Base Configuration
Before any other sub-section of the configuration is processed, the following
options can be set.
daemonize = false
rootdir = /tmp
user = nobody
group = nobody
max-nofile = 1024
daemonize
The value of this option is a boolean (either true or false). If the value
is true, RProxy will daemonize after start, otherwise the server will run in the
foreground.
rootdir
If RProxy is configured to daemonize, the service will daemonize into this
i directory.
user
Drop permissions to this user once root operations have been executed.
The default of this is to run as the current user.
group
Drop permissions to this group once root operations have been executed.
The default of this is to run as the current group.
max-nofile
If your system supports set/get rlimits, this sets the maximum number of
file-descriptors the server can use at one time. Since RProxy will attempt
to keep all of the downstream connections alive, it is suggested that this
number be pretty high.
It should be noted that by default, most systems won’t allow a user to go
over a static number (most of the time 1024) even with setrlimit. In this
case, a user must perform system-wide configurations.
On linux you can add the following to the file /etc/security/
Note a reboot is required for this setting to take effect.
On OSX, the following command can be run
“sudo launchctl limit maxfiles 590000 590000”
Base Server Configuration
RProxy configuration must contain one or more “server” configuration sections.
These sections contains all the required information to deal with an incoming
request. The base configuration for a server is as follows:
addr = 127. 0. 1
port = 8080
threads = 4
read-timeout = { 0, 0}
write-timeout = { 0, 0}
pending-timeout = { 0, 0}
high-watermark = 0
max-pending = 0
backlog = 0
addr
The IP address in which to listen on.
port
The port to listen on
threads
The number of threads to use for this server (note that downstream
connections are multiplied by this number).
read-timeout
The timeout in { ‘seconds’, ‘microseconds’} for a client connection who has
not sent any data. For example, if the value of this was “{ 1, 0}”, if the
client has not been active for 1 second, the connection is closed.
Setting this will evade potential idle connection DoS attacks.
write-timeout
The timeout in { ‘seconds’, ‘microseconds’} to wait for data to the client
to be written. If a client is blocking on the read for this long, the
connection is closed.
pending-timeout
When a connection is first made to RProxy, it is not immediately processed,
instead it is placed in a pending queue. Only when a downstream connection has
become available for use does the client get serviced. If a downstream does not
become available for this amount of time, the client connection is shut down and
removed from the pending queue.
This makes sure both the RProxy service and the downstream services are
never overloaded.
max-pending
If there are this many clients waiting for a backend server to be available,
the incoming connection will not be accepted.
This setting assures that the server cannot be overloaded with too many
connections.
high-watermark
In many cases, a downstream may write faster to the RProxy than it can to
the client. If the client is unable to keep up with the speed the backend server
is sending, you may experience very high memory consumption. This is called a
fast-writer/slow-reader effect.
If the number of bytes in the output buffer to the client goes over this
number, RProxy will disable reading data from the backend until all data in the
output queue to the client has been sent.
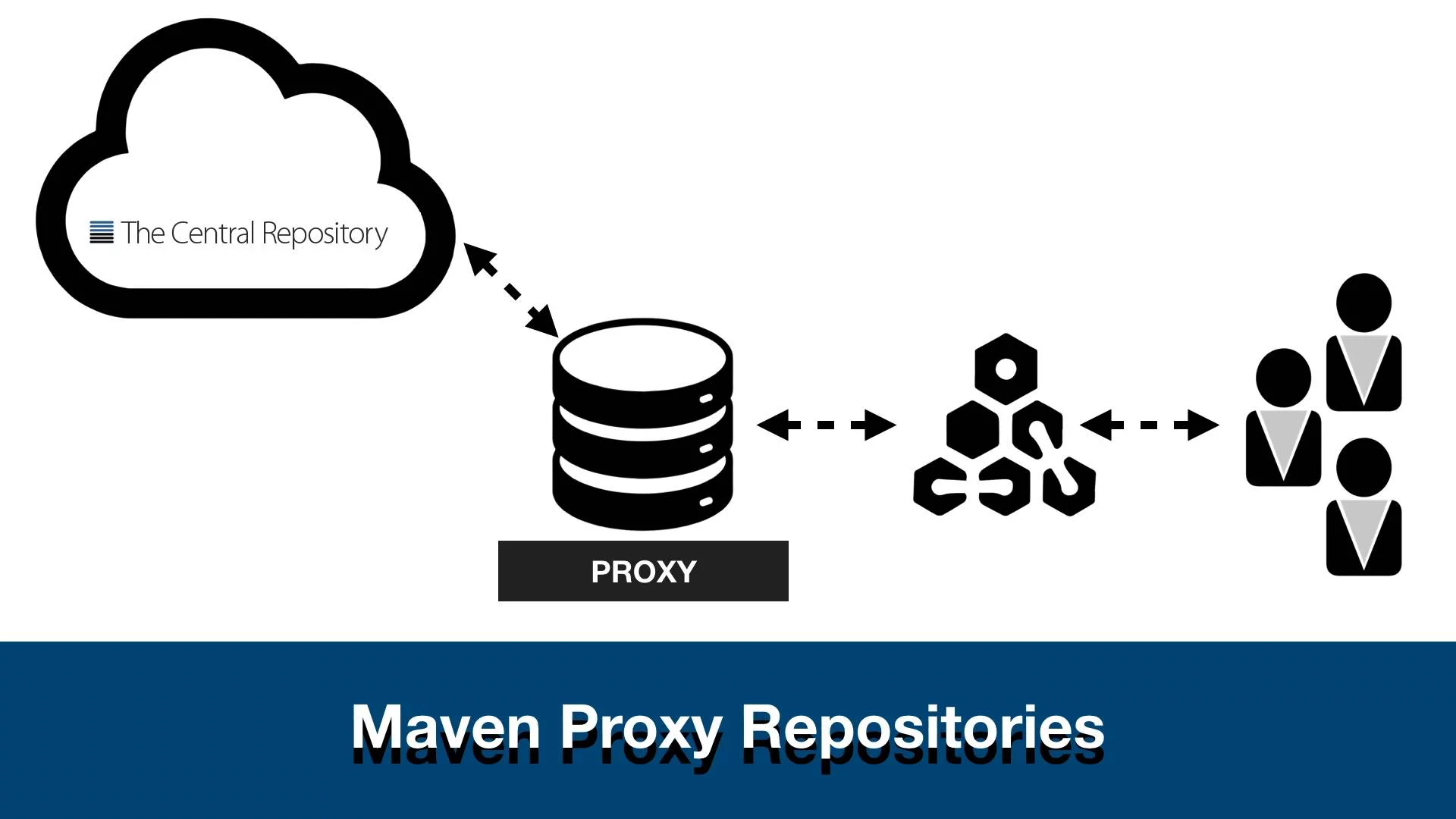
Server::Downstream Configuration
Each server section contains one or more “downstreams” (in other words, a
backend service). Each downstream configuration directive is named, which is
referenced by a rule (discussed later).
The information contained within the downstream configuration is global to a
server; all virtual host and rule will use the downstream information contained
within each downstream section.
downstream
enabled = true
addr = x. x. x
port = nnnn
connections = 4
retry = { 0, 500000}}
NAME
Each downstream must have a unique name.
enabled
If this value is set to false, RProxy will not attempt to make connections
or utilize this downstream in any of the rules.
The FQDN or IP address of this downstream server.
The listening port of the downstream server.
connections
The number of connections RProxy will attempt to keep available. Note that
this number is multiplied by the number of threads configured for the
server. For example if you have 4 threads, and 2 connections, RProxy actually
maintains 8 connections.
If number of bytes in the sendQ is over the value of this number (in bytes),
further reading from the client is disabled until the sendQ has been emptied.
This setting assures that backend servers will not be overloaded by clients.
If no data has been read from this downstream for this many { seconds,
microseconds}, the connection is terminated.
If a write request takes over { seconds, microseconds} to happen, the
connection is terminated.
retry
If one of the downstream connections has been terminated for some reason,
this is the time in { seconds, microseconds} RProxy will wait until it tries to
re-establish the connection.
Server::SSL Configuration
When this configuration section is present and enabled, RProxy will treat
incoming connections as SSL.
ssl {
enabled = false
protocols-on = { ALL}
protocols-off = {}
cert =
key =
ca =
capath = /capath/
ciphers = “ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-RC4-SHA:ECDHE-RSA-AES128-SHA:RC4-SHA:RC4-MD5:ECDHE-RSA-AES256-SHA:AES256-SHA:ECDHE-RSA-DES-CBC3-SHA:DES-CBC3-SHA:AES128-SHA”
verify-peer = false
enforce-peer-cert = false
verify-depth = 0
context-timeout = 172800
cache-enabled = true
cache-timeout = 1024
cache-size = 65535
crl = {}}
If set to true, SSL is enabled, otherwise SSL is disabled.
cert
The servers SSL cert
key
The servers private SSL key
ca
A specific CA file
capath
Relative path to search for valid CA’s
ciphers
Accepted ciphers
protocols-(on|off)
The SSL options for enabling or disabling SSL specific protocols. Options: SSLv2, SSLv3, TLSv1, or ALL
verify-peer
Enables SSL client peer verification
enforce-peer-cert
If true, a client is rejected if it does not supply a client certificate.
cache-enabled
Enable SSL certificate cache
cache-size
Maximum size of the SSL cache
cache-timeout
The lifetime a cert will be kept in the cache.
context-timeout
Timeout for (OpenSSL >= 1. 0) session timeouts.
Server::SSL::CRL Configuration
A server / vhost can be configured to use a CRL list or file which can be
reloaded without restarting or signals. This configuration is turned off by
default.
crl {
file = “/path/to/”
dir = “/path/to/crldir/”
reload = { 10, 0}}}
file
Read from a specific file for CRLs.
dir
Read from a specific directory for CRLs
reload
A timer (in secuds, useconds) to check for changes and reload the CRL
configuration if changes have been mae.
Server::Vhost Configuration
Server::Vhost::Rule Configuration
Server::Logging Configuration
rproxy: introduction
rproxy: introduction
introduction |
devel |
download |
cvs |
docs |
mailing lists |
resources
mirrors |
freshmeat |
sourceforge
This is so cool, I almost giggled
when I
checked the rproxy/libhsync pages.
— Alberto Accomazzi
project status
2002-10-03
The rproxy project is inactive.
It now seems that the effort to get rsync-in-HTTP widely adopted
is not justified giving the increasing availability of
high-bandwidth connections, and the decreasing fraction of web
traffic that is suitable for delta-compression.
The librsync library which
was developed as part of the project seems to have a more
generally useful future. It is likely to power the possible new
major revision of rsync. Early steps towards that are visible in
Wayne’s rzync prototype, and Martin’s superlifter design.
If you’re interested in developing the project then please go
ahead and feel free to contact mbp at
problem statement
Caches are used to good effect on today’s web to improve response
times and reduce network usage. For any given resource, such as an
HTML page or an image, the client remembers the last instance it
retrieved, and it may use it to satisfy future requests. However, the
current-system is all-or-nothing: the resource must either be exactly
the same as the cached instance, or it is downloaded from scratch.
The web is moving towards dynamic content: many pages are assembled
from databases or are customized for each visitor. In the existing
HTTP caching system, this means that many resources cannot be cached
at all.
proposed solution
A far better approach would be for the server to download a
description of the changes from the old instance to the new one: a
`diff’ or `delta’.
Some people have proposed that the server should send the resource
as an unchanging template plus variable values, or that the server
should retain all old instances and so calculate the differences.
These techniques have some value, but they constrain the server-side
developer and seem unlikely to be widely adopted.
The rproxy extensions to HTTP allow the server to generate a diff
relative to the cached instance in a way that is completely general,
and transparent to both the server and user agent.
protocol
rproxy adds backwards-compatible extensions to HTTP that come into
operation when two parties to a web request understand the `hsync’
encoding. If there are no two that can handle these extensions then
they are silently ignored, so that the software will interoperate
smoothly with existing systems. These parties might be the user agent
(browser), the origin server, or intermediate proxies. At this stage
of the project special-purpose proxies are used so that neither the
server nor user-agent need be changed, but we expect to integrate this
extension into popular web software in the near future.
When an rproxy-enabled client requests a resource, it first checks
whether it has a cached copy of the resource from a previous request.
If it does, then it finds a block-by-block signature of the file, by
computing a checksum over consecutive extents of equal length, such as
1024 bytes. The client adds this checksum into a header of the
request and transmits the request as usual.
When an rproxy-enabled server receives a request containing a
signature, it proceeds to generate the response, perhaps by running a
server-side script. It then searches through the new instance body
for blocks that have checksums that match those of blocks in the
signature from the client. When it finds a match, it decides that the
block is repeated from the old instance. Using this information, it
generates a diff composed of instructions to copy sections from the
old file, and instructions to insert new literal data. In fact,
encoding can be performed inline as the response is generated, so
large responses can be handled equally well.
The search for matching blocks obviously has to be able to cope
with blocks that don’t start on aligned boundaries, or it would not be
useful in the common case where data is inserted or removed. The
algorithm addresses this by supplying for this block both a `weak’ CRC
checksum, and a `strong’ MD4 hash. The weak checksum algorithm is
such that the server can efficiently check for a match at every byte
offset. If a match is found, then the strong checksum is compared.
If both match, the probability is astronomically high that the blocks
are in fact identical.
The server also generates and sends down the signature of the new
instance. The client is required to store this signature and return
it on any future requests in which it wishes to use the cached
instance. This mechanism will allow the differencing algorithm to be
enhanced in the future without changing the client software.
The rproxy algorithm is based on the well-known and trustworthy
rsync software by
Andrew Tridgell.
project plan
An early implementation of rproxy achieved bandwidth savings on the
order of 90% for portal web sites.
Our plans for the future are to
Provide a liberally licensed reference implementation of the
algorithms.
Release a usable stand-alone proxy and encourage community testing
and comments.
Integrate our implementation into popular open source web software
such as Apache 2. 0,
Squid, and
Mozilla.
Document the protocol extensions and encoding formats and shepherd
them through the IETF standards
process to become a standard extension to HTTP.
Copyright (C) 1999-2001 by Martin Pool unless otherwise noted.
$Id:, v 1. 5 2002/10/03 07:58:07 mbp Exp $
rproxy is fed and clothed by
Linuxcare OzLabs, and
sleeps on the sofa at SourceForge.
rProxy.com – Ultimate privacy tool!
Welcome to rProxy!
My friend! I am glad to see you again on rProxy! We have lots dedicated users from many countries and they all prefer rProxy on their secure and secret browsing needs.
rProxy will let you get into sites which are blocked in your contry by your entities.
Enter your URL here:
We welcome you to Your ultimate privacy tool!
rProxy will provide you a simple and fast way to change your local IP address when you are surfing the internet.
Our service is completely portable and we wont ask you to install any other softwares or make any modifications to your PC settings.
There are possibly several sites blocked by your our free proxy service to bypass those filters.
rProxy uses encryption technology to keep your information secure and has features like agent masking, cookine management,
advertisement removal.
You just need your browser like firefox or google chrome to use our free thirdparty software is needed.
We dont show any irritating advertisements or pop-ups.
We support video watching on Youtube, Dailymotion and Vimeo.
You will be able to browse your favorite social networks such as Twitter, Facebook and Instagram
Those websites wont see your personal information as we are hiding them to make you invisible.
Noone will know which sites you are browsing on the internet.
Warmest regards.
rProxy.
Home
Browser Settings
Delete Cookies
Privacy Policy
Contact US