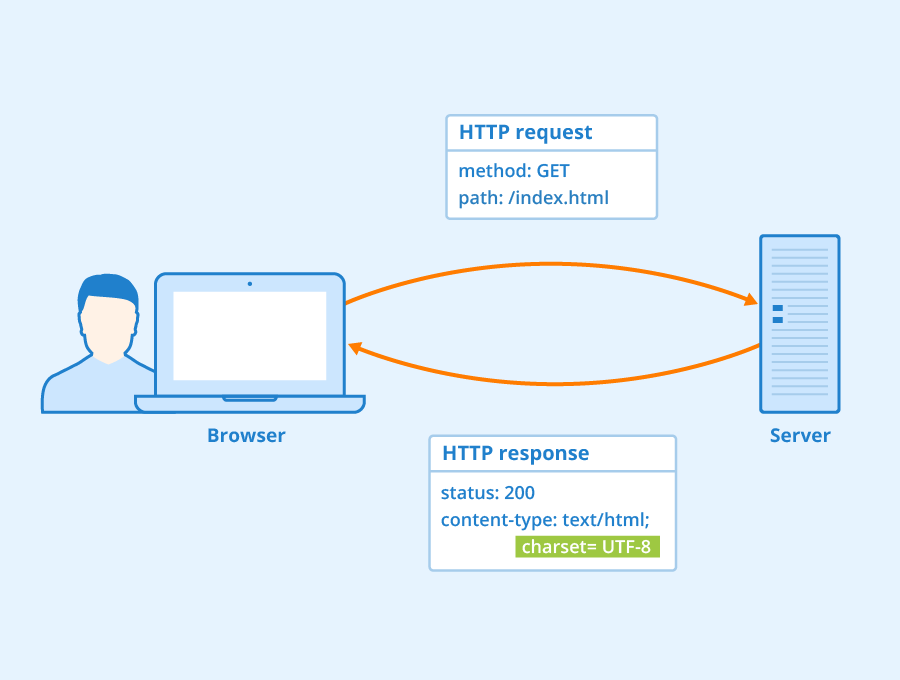
Proxy Server Authentication Methods

Proxy Authentication Types – ItStillWorks
i Jupiterimages/ Images Proxy servers route Internet traffic for various reasons. You might use a proxy server to hide your Internet Protocol address while browsing, as the IP address of a proxy server will substitute for your own. Other times, however, local area networks use proxy servers to control traffic in and out of a network. In these cases, authentication is typically required. This authentication can come by way of simple passwords or more comprehensive authentication suites such as NT LAN Manager or Kerberos. TransparentWhile not, strictly speaking, a type of authentication, the state of nonauthentication in proxy servers has a particular class, called the “transparent” proxy. This sort of proxy does not necessarily require a user authentication, but forces particular users into particular networks based on their identities, and as such usually involves some sort of authentication. This typically works through verifying users based on IP address. Password-BasedA simple form of proxy authentication is simple password authentication. In order to use the proxy server, you have to provide a username and password. This measure can keep unwanted users out. However, password authentication suffers from a few pitfalls, namely that passwords are often easy to break and only offer a single level of security. Usually, you should package password authentication with another authentication measure for two-step authentication. Windows Challenge/ResponseMicrosoft NTLM involves password authentication coupled with a challenge/response algorithm. After you log on to the NTLM server, the server sends an package of data based on the password and username used, as well as on the domain of the server. Your client application must encrypt the data and send it back to the server. If the server can decrypt it using its key, then your computer has been authenticated to use that proxy. KerberosKerberos, developed at MIT, works in a similar fashion as NTLM. When your client application tries to use a Kerberos proxy, it files a ticket with the server. The server uses the information on the ticket to encrypt a package of data, which it sends back to your client application. The client application must decrypt the ticket using a shared authentication key. The decrypted data now represents an authorization ticket that allows your computer access to use the Kerberos server. References Writer Bio G. S. Jackson specializes in topics related to literature, computers and technology. He holds a Bachelor of Arts in English and computer science from Southern Illinois University Edwardsville.
Configuring Proxy Authentication Method – GFI Software
Configuring Proxy Authentication Method
Proxy Authentication enables you to configure the authentication method used by the proxy. This determines how client machines are validated when accessing the Internet. Proxy Authentication must be enabled to be able to create new policies for users or groups. By default, Proxy Authentication is disabled. When Proxy Authentication is disabled, you are only allowed to configure new policies using IP addresses.
For enhanced security we recommend using Integrated Authentication. This method is more secure since unlike Basic Authentication it does not transmit user credentials over the network.
NOTE
The Configuration Wizard is launched automatically after installing GFI WebMonitor or manually from the Settings menu.
Proxy authentication settings
To configure user authentication method:
Go to Core Settings > Connection Settings.
Click the Proxy Authentication switch to enable.
In the Proxy Authentication area, select one of the following options:
Option 1: Leave Proxy Authentication off if the user is not required to provide login credentials when new Internet sessions are launched.
Option 2: If proxy authentication is required, select one of the following options:
Option
Description
Basic authentication
Select if user is required to provide login credentials when new Internet sessions are launched. When using Basic authentication, the browser prompts the user for a user name and password. This information is transmitted across HTTPHypertext Transfer Protocol. as plain text and considered insecure.
Integrated authentication
(Recommended) This option enables GFI WebMonitor proxy to authenticate users by using the client machine access control service. User is not prompted to provide login credentials when new Internet sessions are launched. We recommend using Integrated authentication in a Windows domain environment since this method of authentication does not transmit user passwords across the network.
Integrated authentication is disabled if the GFI WebMonitor machine authenticates local users as Guest. The Guest only network access model grants all users the same level of access to system resources and so GFI WebMonitor proxy will not be able to differentiate between the different users using a client machine.
[Optional] In the IP’s that will bypass the authentication field, key in IP addresses to exclude from proxy authentication. IP addresses specified in this field will not be prompted to provide login credentials when new Internet sessions are launched.
Click Save.
Proxy-Authenticate – HTTP – MDN Web Docs
The HTTP Proxy-Authenticate response header defines the
authentication method that should be used to gain access to a resource behind a
proxy server. It authenticates the request to the proxy server, allowing
it to transmit the request further.
The Proxy-Authenticate header is sent along with a 407
Proxy Authentication Required.
Header type
Response header
Forbidden header name
no
SyntaxProxy-Authenticate:
DirectivesExamplesProxy-Authenticate: Basic
Proxy-Authenticate: Basic realm=”Access to the internal site”
SpecificationsSpecificationHypertext Transfer Protocol (HTTP/1. 1): Authentication (HTTP/1. 1)# compatibilityBCD tables only load in the browserSee also
HTTP authentication
Authorization
Proxy-Authorization
WWW-Authenticate
401, 403, 407
Frequently Asked Questions about proxy server authentication methods
How do I authenticate a proxy server?
Configuring Proxy Authentication MethodGo to Core Settings > Connection Settings.Click the Proxy Authentication switch to enable.In the Proxy Authentication area, select one of the following options:
What is authentication proxy server?
The HTTP Proxy-Authenticate response header defines the authentication method that should be used to gain access to a resource behind a proxy server. It authenticates the request to the proxy server, allowing it to transmit the request further.Aug 13, 2021
What are some authentication methods?
5 Common Authentication TypesPassword-based authentication. Passwords are the most common methods of authentication. … Multi-factor authentication. … Certificate-based authentication. … Biometric authentication. … Token-based authentication.

