
Proxy Network
What is a network Proxy? | Security Encyclopedia – HYPR
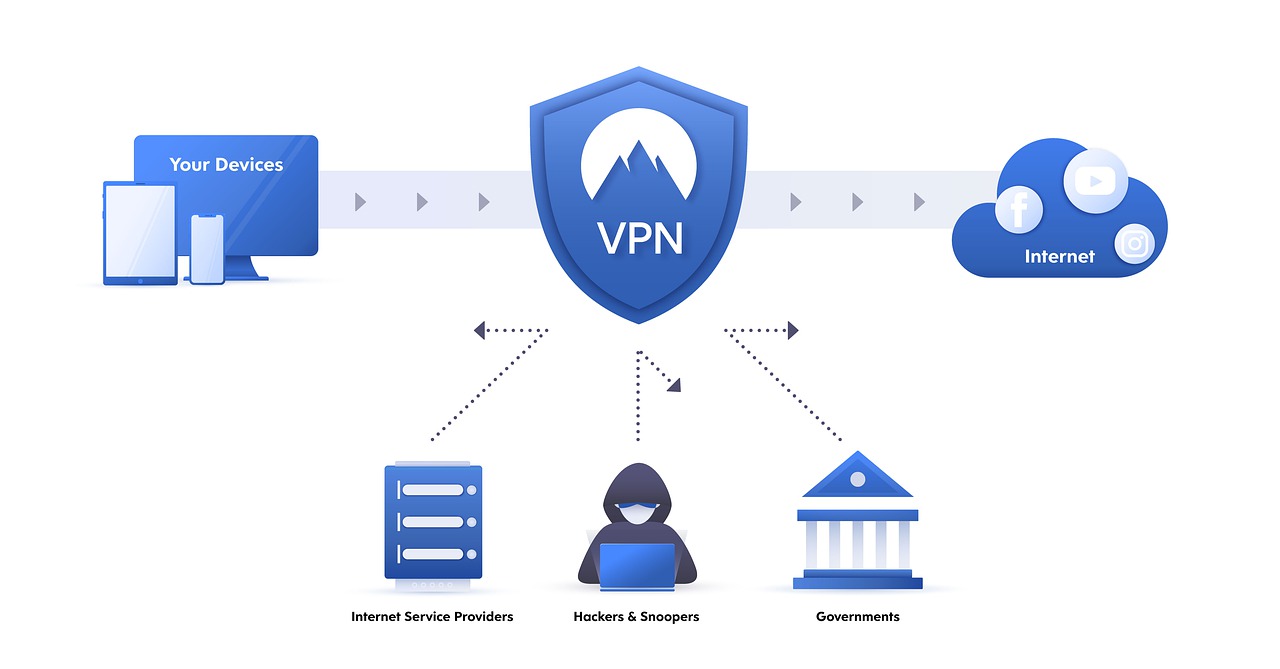
A Proxy or Proxy Server is an intermediary server, either software or hardware, the sits between an end user and a website or other service’s server. Proxies are used for different reasons including efficiency, privacy, and a proxy, web traffic moves through the proxy along its way to its ultimate destination. Requests are first sent to the proxy server, which handles the request along with the additional tasks of filtering content, scanning for malware, masking the origin of the request, encrypting messages, and oxies are commonly used for information security against threats and for system optimization, such as load balancing and cacheing similar requests for added speed. They may serve as a firewall, and handle authentication requests. At a minimum, a proxy would shield an enterprise’s internal infrastructure from known threats found on the external servers can have unintended consequences for security. Since they can obfuscate the true origin of a request, they can also mask the legitimate parties to a dialogue, exchange, or transaction. PCs all require a unique Internet Protocol (IP) address that serves as its legitimate identifier. Without the knowledge who the parties are, the masking of parties can result in the parties being spoofed or suffering a man-in-the-middle (MITM) attack. “We’re a small business and therefore don’t have an elaborate IDPS but our IT vendor does have us use a proxy that acts as a firewall against commonplace known threats, by filtering them. As we grow, we’ll hire an internal team assesses and build our infrastructure but for the foreseeable future we’ll stick with the IaaS vendor. ”
Previous
Proximity Authentication
Public Key Infrastructure (PKI)
Next
Share This Post
About proxy servers – IU KB
A proxy server, also known as a “proxy” or “application-level gateway”, is a computer that acts as a gateway between a local network (for example, all the computers at one company or in one building) and a larger-scale network such as the internet. Proxy servers provide increased performance and security. In some cases, they monitor employees’ use of outside resources.
A proxy server works by intercepting connections between sender and receiver. All incoming data enters through one port and is forwarded to the rest of the network via another port. By blocking direct access between two networks, proxy servers make it much more difficult for hackers to get internal addresses and details of a private network.
Some proxy servers are a group of applications or servers that block common internet services. For example, an HTTP proxy intercepts web access, and an SMTP proxy intercepts email. A proxy server uses a network addressing scheme to present one organization-wide IP address to the internet. The server funnels all user requests to the internet and returns responses to the appropriate users. In addition to restricting access from outside, this mechanism can prevent inside users from reaching specific internet resources (for example, certain websites). A proxy server can also be one of the components of a firewall.
Proxies may also cache web pages. Each time an internal user requests a URL from outside, a temporary copy is stored locally. The next time an internal user requests the same URL, the proxy can serve the local copy instead of retrieving the original across the network, improving performance.
Note:
Do not confuse a proxy server with a
NAT (Network Address Translation) device. A proxy server connects to, responds to, and receives traffic from the internet, acting on behalf of the client computer, while a NAT device transparently changes the origination address of traffic coming through it before passing it to the internet.
For those who understand the OSI (Open System Interconnection) model of networking, the technical difference between a proxy and a NAT is that the proxy server works on the transport layer (layer 4) or higher of the OSI model, whereas a NAT works on the network layer (layer 3).
This is document ahoo in the Knowledge Base.
Last modified on 2018-11-15 11:25:00.
What is proxy and why do you need it? – Airtame
A web proxy can help keep your network safe from external threats. Here’s what you need to know.
Let’s talk about the least sexy but most vital part of your workplace: network security. At a school or large office, there is usually an intricate system of security measures keeping private data safe.
Many are familiar with firewalls when talking about network security, perhaps because of the vivid visual it calls to mind. The same unfortunately can’t be said for an integral part of a secure network: the web proxy.
Unlike a firewall, which is used purely for blocking threats, a web proxy acts more as a middleman between a device and the internet. This device could be a computer or even an Airtame. Luckily for Airtame, we now support a web proxy setup, so we can stay on the proxy’s good side.
In this article, we dig a little deeper to uncover why you need to know what a web proxy can do for your network.
What is a proxy?
As the need for internet access at the workplace grows, web proxies come from a need to secure an organization’s internal network from external threats. Broadly speaking, a web proxy, also referred to as a proxy or proxy server, is a way to filter the connection between your computer and the internet.
Let’s break it down.
Say you want to check your Facebook profile to see how many likes that picture of your dog received. You open up a web browser and type in “.
Without a web proxy, your computer would simply connect directly to the internet to access the website and display it for you.
With a proxy, your computer will connect to a separate server, the proxy, that sits between the computer and the internet. The web proxy acts like airport security and is in charge of screening what websites are allowed access or not.
What is and is not allowed is determined by your organization’s IT policy. If social media sites are restricted, then, unfortunately, that means you’ll have to wait until you get home to check your Facebook.
Why do you need web proxy?
There are two overall reasons why larger organizations use web proxies in their network security setup: to protect their private data and to improve the performance of their internal network.
Insure your assets against threats
The top reason why a web proxy is needed on a network is that it protects a company’s data assets by limiting websites that potentially contain malicious code.
And not just data assets, but physical assets too when you consider the possible costs of replacing an organization’s hardware when a virus renders it unusable.
Enterprise companies might have confidential proprietary information, their employees’ private data, as well as their customers’ personal information sitting on their local network. With all this valuable data to protect, it doesn’t seem so excessive to monitor internet usage.
Improve network performance
Depending on the type of proxy you use and how it is set up, it is possible that using a proxy can improve performance by caching web pages.
For example, let’s say you recently visited The proxy can save a temporary copy of the webpage which it stores locally so that when your colleague visits later that day, the proxy can serve up that copy instead of having to retrieve the original from the internet.
This is most useful for frequently visited websites, for instance, if you often refer to your company’s website. It’s saving you the loading time of the page every time you visit.
Every organization’s network is different and can have different needs. Luckily, there are several ways to incorporate a web proxy, or even a set of web proxies, into any network setup, which makes it a flexible solution.
Proxy in action
Not every company makes use of web proxies. The majority of web proxy users are enterprise-level companies or educational institutions that need a manageable way of monitoring the large volume of internet users on their network.
Enterprise companies and educational institutions use proxies to keep their network safe, but they go about it in slightly different ways.
Enterprise
For larger corporations, corporate espionage is not just the stuff of James Bond films. It is a real threat that makes it necessary for companies to monitor the traffic coming in and out of their network. These companies use proxies to filter everything – websites, emails, and any applications that access internet.
Of course, sometimes a web proxy also protects us from ourselves. Checking social media may seem harmless, but let’s admit that it is a productivity threat. In this case, companies use proxies to set time limits for social media use during business hours.
At schools and universities
For schools and universities, it is important to use a web proxy that blocks access to adult content. In this case, purchasing a quality service that keeps an up-to-date database of known adult content sites is key.
In certain instances, it is necessary to block access to radically political websites or sites that promote hate speech, both to ensure a safe environment for students, as well as make sure students cite quality source material in their research.
Another reason schools and universities invest in a good database is to monitor sites known to carry malicious code. Even if a malicious website attempts to hide behind a normal website and redirect you to a site running malware, the web proxy flags this as abnormal behavior and blocks access.
Using Airtame with a web proxy setup
Our latest product update introduces web proxy support. This means that, if your organization uses a web proxy setup, you can now configure Airtame to access the proxy and thereby reach the internet.
[quote: “Web proxy support is a big step forward for Airtame and our enterprise customers, where security and wireless screen sharing go hand-in-hand. ” – Simon Hangaard, Head of Product Management at Airtame]
Airtame requires internet access in order to receive important product updates and to make use of certain tools. For example, you can register your Airtame devices to Airtame Cloud, our web-based device management tool that, among other things, lets you remotely monitor devices.
Another useful Airtame feature that requires internet is our Homescreen, which lets you display web-based dashboards or even slideshows.
Wondering how exactly to configure a web proxy with Airtame? Check out our help article here or reach out to our Customer Success team by clicking the blue chat button
Interested? Let’s talk.
Work email
Full name
Job title
Phone
Organization
Country
State
Please briefly describe your request
All product, all the time. As Product Communications Manager, Jessica takes complicated product stuff and makes it easy to read stuff. When she isn’t writing and editing for Airtame, she’s on the hunt for the best Mexican food in Denmark.
Frequently Asked Questions about proxy network
What is proxy example?
Some proxy servers are a group of applications or servers that block common internet services. For example, an HTTP proxy intercepts web access, and an SMTP proxy intercepts email. … A proxy server can also be one of the components of a firewall. Proxies may also cache web pages.Nov 15, 2018
Do I need a network proxy?
Without a web proxy, your computer would simply connect directly to the internet to access the website and display it for you. With a proxy, your computer will connect to a separate server, the proxy, that sits between the computer and the internet.Apr 3, 2019
Is there a proxy on my network?
Click the “Connections” tab in the Internet Options window. Click the “LAN Settings” button. If there is a check mark in the box next to the “Us a proxy server for your LAN” option, then your PC accesses the Web through a proxy server.

