Home Proxy Server Ubuntu
How to Set Up & Install Squid Proxy Server on Ubuntu 18.04
Introduction
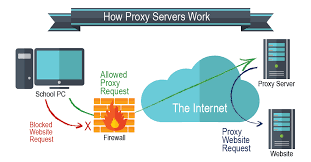
Squid is a Linux-based proxy application. The Squid proxy server is used for filtering traffic, security, and DNS lookups.
Also, Squid can speed up a web server by caching resources. The Squid Proxy allows a server to cache frequently visited web pages. When the user requests a web page or file, the request goes directly to the proxy server — an intermediary device between the user’s device and the internet. The proxy server pulls up the resources and relays them to the user.
This guide will walk you through how to set up and install Squid Proxy server on Ubuntu.
Prerequisites
An Ubuntu operating systemAccess to a terminal window/command line (Ctrl-Alt-T)An Ubuntu user with root or sudo privilegesThe apt package installer, included by defaultA text editor, such as nano
Installing Squid Proxy on Ubuntu
Step 1: Refresh the Software Repositories
Ensure you’re working with the latest software version available.
Launch a terminal window, and enter the following:
sudo apt-get update
Step 2: Install Squid Package on Ubuntu
To install Squid, run the command:
sudo apt-get install squid
The system should prompt for confirmation – enter Y and allow the process to complete itself.
Configuring Squid Proxy Server
The Squid configuration file is found at /etc/squid/
1. Open this file in your text editor with the command:
sudo nano /etc/squid/
2. Navigate to find the _port option. Typically, this is set to listen on Port 3218. This port usually carries TCP traffic. If your system is configured for traffic on another port, change it here.
You may also set the proxy mode to transparent if you’d like to prevent Squid from modifying your requests and responses.
Change it as follows:
_port 1234 transparent
3. Navigate to the _access deny all option. This is currently configured to block all HTTP traffic. This means no web traffic is allowed.
Change this to the following:
_access allow all
4. Navigate to the visible_hostname option. Add any name you’d like to this entry. This is how the server will appear to anyone trying to connect. Save the changes and exit.
5. Restart the Squid service by entering:
sudo systemctl restart squid
Configure Squid Client
All this configuration has been done to set up your Squid proxy server. Now, switch to your client machine and open your web browser.
If you’re using Firefox, you can find the proxy settings under:
Menu > Options > Network Settings > Settings
Tick the radio button for Manual proxy configuration.
If you’ve entered a hostname in Step 4, you should be able to enter that name plus the port you have designated. Otherwise, use the IP address for the system hosting your Squid proxy.
To test it, you can visit – if your proxy is working, your IP address should display as the proxy server’s IP address.
Add Squid ACL
Note: After each of these steps, you should save and exit, then restart the Squid service to apply the new configuration.
Create an access control list by editing the file again, as in Step 4.
Add a new line as follows:
acl localnet src 192. 168. 0. 15
This will create a rule that only allows the system at this IP address to connect. It is recommended that you comment the line to identify the rule:
acl localnet src 192. 15 # test computer
Anything after the # sign is ignored by Squid.
You can specify a range of IP addresses as follows:
acl localnet src 192. 15/30
Open Ports
To open a specific port, add the following:
acl Safe_ports port 123 # Custom port
Configure Proxy Authentication
This forces users to authenticate to use the proxy.
Start by installing apache2-utils:
sudo apt-get install apache2-utils
Create a passwd file, and change the ownership to the Squid user proxy:
sudo touch /etc/squid/passwd
sudo chown proxy: etc/squid/passwd
Add a new user and password
1. To add a new user to Squid, use the command:
sudo htpasswd /etc/squid/passwd newuser
The system will prompt you to enter and confirm a password for newuser.
2. Edit the /etc/squid/ file, and add the following command lines:
auth_param basic program /usr/lib64/squid/basic_ncsa_auth /etc/squid/passwd
auth_param basic children 5
auth_param basic realm Squid Basic Authentication
auth_param basic credentialsttl 2 hours
acl auth_users proxy_auth REQUIRED
_access allow auth_users
Block Websites on Squid Proxy
1. Create and edit a new text file /etc/squid/ by entering:
2. In this file, add the websites to be blocked, starting with a dot:..
Note: The dot specifies to block all subsites of the main site.
3. Open the /etc/squid/ file again:
4. Add the following lines just above your ACL list:
acl blocked_websites dstdomain “/etc/squid/”
_access deny blocked_websites
Commands When Working with the Squid Service
To check the status of your Squid software, enter:
sudo systemctl status squid
This will tell you whether the service is running or not.
To start the service enter:
sudo systemctl start squid
Then set the Squid service to launch when the system starts by entering:
sudo systemctl enable squid
You can re-run the status command now to verify the service is up and running.
To stop the service, use the command:
sudo systemctl stop squid
To prevent Squid from launching at startup, enter:
sudo systemctl disable squid
Conclusion
If you’ve followed along closely, you should now have a basic understanding of how Squid works, and how to install and configure Squid Proxy on Ubuntu.
Proxy servers are a valuable tool for securing network traffic, preventing attacks and restricting access.
Check out our article on how to set up your Ubuntu system to work with a proxy server to configure your Ubuntu machine to use a proxy.
Interested in setting up this application on a different OS? You may want to check out how to install Squid on CentOS 7.

Proxy Servers – Squid | Ubuntu
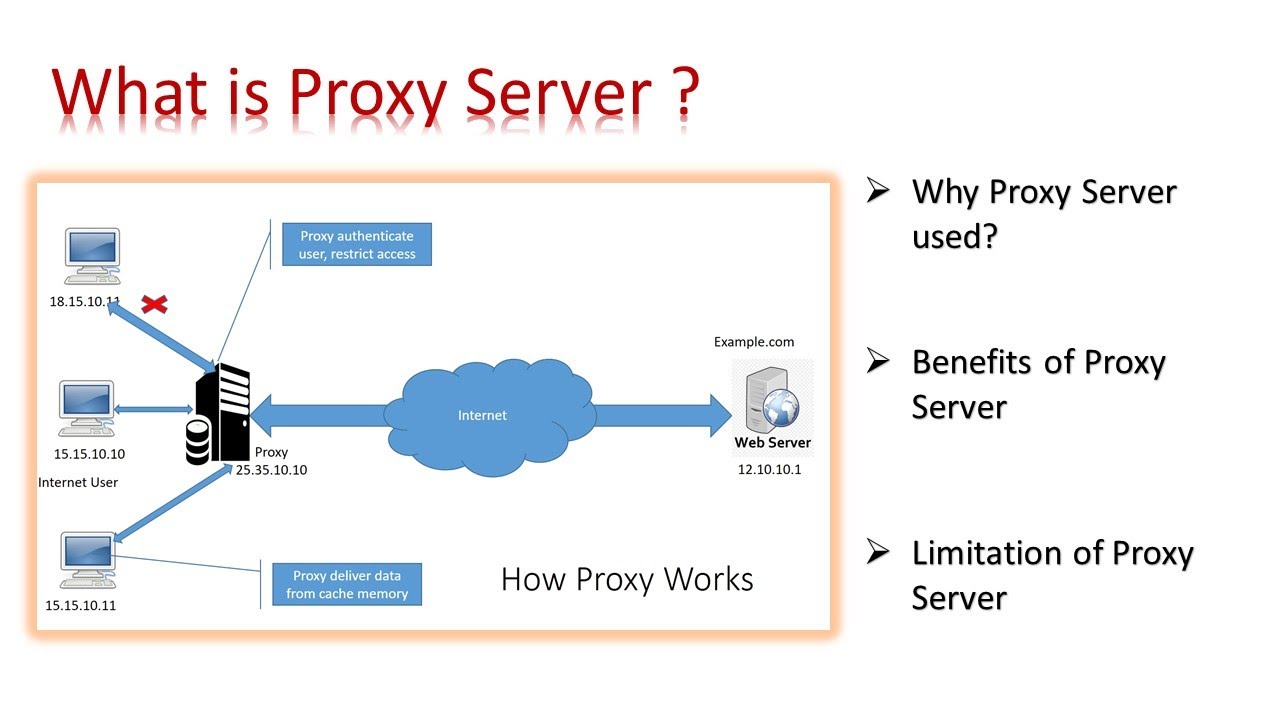
Squid is a full-featured web proxy cache server application which provides proxy and cache services for Hyper Text Transport Protocol (HTTP), File Transfer Protocol (FTP), and other popular network protocols. Squid can implement caching and proxying of Secure Sockets Layer (SSL) requests and caching of Domain Name Server (DNS) lookups, and perform transparent caching. Squid also supports a wide variety of caching protocols, such as Internet Cache Protocol (ICP), the Hyper Text Caching Protocol (HTCP), the Cache Array Routing Protocol (CARP), and the Web Cache Coordination Protocol (WCCP).
The Squid proxy cache server is an excellent solution to a variety of proxy and caching server needs, and scales from the branch office to enterprise level networks while providing extensive, granular access control mechanisms, and monitoring of critical parameters via the Simple Network Management Protocol (SNMP). When selecting a computer system for use as a dedicated Squid caching proxy server for many users ensure it is configured with a large amount of physical memory as Squid maintains an in-memory cache for increased performance.
Installation
At a terminal prompt, enter the following command to install the Squid server:
sudo apt install squid
Configuration
Squid is configured by editing the directives contained within the /etc/squid/ configuration file. The following examples illustrate some of the directives which may be modified to affect the behavior of the Squid server. For more in-depth configuration of Squid, see the References section.
Tip
Prior to editing the configuration file, you should make a copy of the original file and protect it from writing so you will have the original settings as a reference, and to re-use as necessary. Make this copy and protect it from writing using the following commands:
sudo cp /etc/squid/ /etc/squid/
sudo chmod a-w /etc/squid/
To set your Squid server to listen on TCP port 8888 instead of the default TCP port 3128, change the _port directive as such:
_port 8888
Change the visible_hostname directive in order to give the Squid server a specific hostname. This hostname does not necessarily need to be the computer’s hostname. In this example it is set to weezie
visible_hostname weezie
The cache_dir option allows one to configure an on-disk cache, the default option is on-memory cache. The cache_dir directive takes the following arguments:
cache_dir
In the config file you can find the default cache_dir directive commented out:
# Uncomment and adjust the following to add a disk cache directory.
#cache_dir ufs /var/spool/squid 100 16 256
You can just use the default option but you can also customize your cache directory, basically changing the
ufs: the old well-known Squid storage format that has always been there.
aufs: uses the same storage format as ufs, utilizing POSIX-threads to avoid blocking the main Squid process on disk-I/O. This was formerly known in Squid as async-io.
diskd: uses the same storage format as ufs, utilizing a separate process to avoid blocking the main Squid process on disk-I/O.
rock: is a database-style storage. All cached entries are stored in a “database” file, using fixed-size slots. A single entry occupies one or more slots.
If you want to use a different directory type please take a look at their different options.
Using Squid’s access control, you may configure use of Internet services proxied by Squid to be available only users with certain Internet Protocol (IP) addresses. For example, we will illustrate access by users of the 192. 168. 42. 0/24 subnetwork only:
Add the following to the bottom of the ACL section of your /etc/squid/ file:
acl fortytwo_network src 192. 0/24
Then, add the following to the top of the _access section of your /etc/squid/ file:
_access allow fortytwo_network
Using the excellent access control features of Squid, you may configure use of Internet services proxied by Squid to be available only during normal business hours. For example, we’ll illustrate access by employees of a business which is operating between 9:00AM and 5:00PM, Monday through Friday, and which uses the 10. 1. 0/24 subnetwork:
acl biz_network src 10. 0/24
acl biz_hours time M T W T F 9:00-17:00
_access allow biz_network biz_hours
Note
After making changes to the /etc/squid/ file, save the file and restart the squid server application to effect the changes using the following command entered at a terminal prompt:
sudo systemctl restart rvice
If formerly a customized squid3 was used that set up the spool at /var/log/squid3 to be a mountpoint, but otherwise kept the default configuration the upgrade will fail. The upgrade tries to rename/move files as needed, but it can’t do so for an active mountpoint. In that case please either adapt the mountpoint or the config in /etc/squid/ so that they match.
The same applies if the include config statement was used to pull in more files from the old path at /etc/squid3/. In those cases you should move and adapt your configuration accordingly.
References
Squid Website
Ubuntu Wiki Squid page.
How to Install and Configure Squid Proxy on Ubuntu 20.04
Squid is a full-featured caching proxy supporting popular network protocols like HTTP, HTTPS, FTP, and more. It can be used to improve the web server’s performance by caching repeated requests, filter web traffic, and access geo-restricted tutorial explains how to set up a Squid Proxy on Ubuntu 20. 04 and configure Firefox and Google Chrome web browsers to use stalling Squid on Ubuntu The squid package is included in the standard Ubuntu 20. 04 repositories. To install it, run the following commands as sudo user:sudo apt updatesudo apt install squidOnce the installation is completed, the Squid service will start automatically. To verify it, check the service status:sudo systemctl status squidThe output will look something like this:● rvice – Squid Web Proxy Server
Loaded: loaded (/lib/systemd/system/rvice; enabled; vendor preset: enabled)
Active: active (running) since Fri 2020-10-23 19:02:43 UTC; 14s ago
Docs: man:squid(8)…
Configuring Squid The squid service can be configured by editing the /etc/squid/ file. The configuration file contains comments that describe what each configuration option does. You can also put your configuration settings in separate files, which can be included in the main configuration file using the “include” making any changes, it is recommended to back up the original configuration file:sudo cp /etc/squid/{,. orginal}To start configuring your squid instance, open the file in your text editor:sudo nano /etc/squid/ default, squid is set to listen on port 3128 on all network interfaces on the you want to change the port and set a listening interface, locate the line starting with _port and specify the interface IP address and the new port. If no interface is specified Squid will listen on all interfaces. /etc/squid/ Squid normally listens to port 3128
_port IP_ADDR:PORT
Running Squid on all interfaces and on the default port should be fine for most allows you to control how the clients can access the web resources using Access Control Lists (ACLs). By default, access is permitted only from the all clients who use the proxy have a static IP address, the simplest option to restrict access to the proxy server is to create an ACL that will include the allowed IPs. Otherwise, you can set squid to use stead of adding the IP addresses in the main configuration file, create a new dedicated file that will hold the allowed IPs:/etc/squid/allowed_ips. txt192. 168. 33. 1
# All other allowed IPs
Once done, open the main configuration file and create a new ACL named allowed_ips (first highlighted line) and allow access to that ACL using the _access directive (second highlighted line):/etc/squid/…
acl allowed_ips src “/etc/squid/”
#…
#_access allow localnet
_access allow localhost
_access allow allowed_ips
# And finally deny all other access to this proxy
_access deny allThe order of the _access rules is important. Make sure you add the line before _access deny _access directive works in a similar way as the firewall rules. Squid reads the rules from top to bottom, and when a rule matches, the rules below are not processed. Whenever you make changes to the configuration file, you need to restart the Squid service for the changes to take effect:sudo systemctl restart squidSquid Authentication If restricting access based on IP doesn’t work for your use case, you can configure squid to use a back-end to authenticate users. Squid supports Samba, LDAP, and HTTP basic this guide, we’ll use basic auth. It is a simple authentication method built into the HTTP generate a crypted password, use the openssl tool. The following command appends the USERNAME:PASSWORD pair to the /etc/squid/htpasswd file:printf “USERNAME:$(openssl passwd -crypt PASSWORD)\n” | sudo tee -a /etc/squid/htpasswd
For example, to create a user “josh” with password “P@ssvv0rT”, you would run:printf “josh:$(openssl passwd -crypt ‘P@ssvv0rd’)\n” | sudo tee -a /etc/squid/htpasswdjosh:QMxVjdyPchJl6
The next step is to enable the HTTP basic authentication and include the file containing the user credentials to the squid configuration the main configuration and add the following:sudo nano /etc/squid/…
auth_param basic program /usr/lib/squid3/basic_ncsa_auth /etc/squid/htpasswd
auth_param basic realm proxy
acl authenticated proxy_auth REQUIRED
_access allow authenticated
_access deny allThe first three highlighted lines are creating a new ACL named authenticated, and the last highlighted line is allowing access to authenticated start the Squid service:sudo systemctl restart squidConfiguring firewall To open the Squid ports, enable the UFW
‘Squid’ profile:sudo ufw allow ‘Squid’If Squid is running on another, non-default port, for example, 8888 you can allow traffic on that port with: sudo ufw allow 8888/nfiguring Your Browser to Use Proxy Now that you have Squid set up, the last step is to configure your preferred browser to use refox The steps below are the same for Windows, macOS, and the upper right-hand corner, click on the hamburger icon ☰ to open Firefox’s menu:Click on the ⚙ Preferences down to the Network Settings section and click on the Settings… button. A new window will the Manual proxy configuration radio your Squid server IP address in the HTTP Host field and 3128 in the Port the Use this proxy server for all protocols on the OK button to save the this point, your Firefox is configured, and you can browse the Internet through the Squid proxy. To verify it, open, type “what is my ip” and you should see your Squid server IP revert back to the default settings, go to Network Settings, select the Use system proxy settings radio button and save the are several plugins that can also help you to configure Firefox’s proxy settings, such as FoxyProxy
Chrome Google Chrome uses the default system proxy settings. Instead of changing your operating system proxy settings, you can either use an addon such as SwitchyOmega
or start Chrome web browser from the command launch Chrome using a new profile and connect to the Squid server, use the following command:Linux:/usr/bin/google-chrome \
–user-data-dir=”$HOME/proxy-profile” \
–proxy-server=”SQUID_IP:3128″
macOS:”/Applications/Google Chrome” \
Windows:”C:\Program Files (x86)\Google\Chrome\Application\” ^