Bot Detection
Bot Detection – Auth0
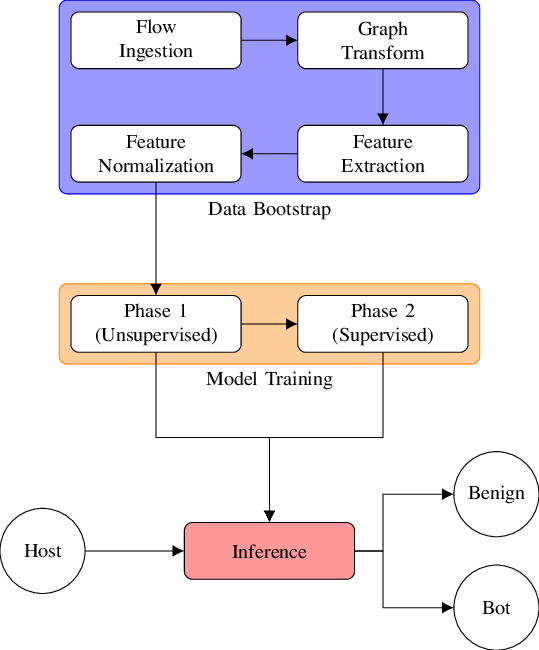
Bot detection mitigates scripted attacks by detecting when a request is likely to be coming from a bot. These types of attacks are sometimes called credential stuffing attacks or list validation attacks. It provides protection against certain attacks that adds very little friction to legitimate users. When such an attack is detected, it displays a CAPTCHA step in the login experience to eliminate bot and scripted traffic. To learn more, read our Credential Stuffing Attacks: What Are They and How to Combat Them th0 uses a large amount of data and statistical models to identify patterns that signal when bursts of traffic are likely to be from a bot or script. Users who attempt to log in or create accounts from IPs that are determined to have a high likelihood of being part of a credential stuffing attack will see a CAPTCHA step. The triggers are designed so that this only happens for bad traffic; the objective is to not add friction to legitimate you want to use Google reCAPTCHA Enterprise, you will need to obtain the Site Key, API Key, and Project ID from Google. To learn more, read Configure reCAPTCHA Enterprise on Google Cloud protection is enabled by default for all connections. Go to Dashboard > Security > Attack Protection and select Bot Detection. In the Detection section, enable the toggle.
Enabling attack protection features without any response settings enabled activates Monitoring mode, which records related events in your tenant log only. To learn more, read View Attack Protection Log Events.
If you cannot see the toggle to enable this feature, you may need to upgrade your the Response section, choose when you want to require CAPTCHA. Choose Never to never require your users to complete a CAPTCHA to log When Risky to only require your users to complete a CAPTCHA if the login appears to be high risk. Select the type of CAPTCHA in the next step. Choose Always to always require your users to complete a CAPTCHA to log in. Select the type of CAPTCHA in the next whether you wish to use simple CAPTCHA provided by Auth0 or Google reCAPTCHA (requires external setup and registration). If you choose Simple CAPTCHA, you are done. Choose this option if your login experience is required to work without you choose Google reCAPTCHA v2, enter the Site Key and Site Secret that you obtained when you registered your app with Google. If you choose Google reCAPTCHA Enterprise, enter the Site Key, API Key, and Project ID that you obtained when you configured Google reCAPTCHA Enterprise on the Google Cloud Platform. To learn more, read Configure reCAPTCHA Enterprise on Google Cloud Platform. Ensure that you have chosen When Risky or Always under Enforce CAPTCHA strictions and limitationsBot protection works for web and mobile apps that use Auth0 Universal Login. For experiences that do not use Universal Login, levels of support are limited, in particular for flows that cannot support a CAPTCHA or reCAPTCHA challenge. Please ensure all of your login experiences are supported before turning on this feature, or you may introduce errors into your application.
Flow
Limitation
New Universal Login
Supported by default.
Classic Universal Login (no customizations)
Classic Universal Login (custom login page using Lock template widget)
Supported if using Lock version 11. 30 or higher.
Classic Universal Login (custom login page using Custom Login Form template widget)
Supported if using version 9. 16 or higher to build custom login pages only if you enhance your code to handle a CAPTCHA or reCAPTCHA challenge.
Classic Universal Login (custom login page using Passwordless template)
Not supported.
Web or native apps using Resource Owner Password Flow (including those using and SDKs)
Native apps using newest version of SDKs
Supported. The SDKs handle a risky login by invoking the Universal Login flow.
Flows not hosted by Auth0 using, which perform cross-origin authentication (co/authenticate endpoint)
Depending on the types of connections you use, bot detection has the following limitations.
Connection Type
Database connections Custom database connections Active Directory/LDAP connections
Supported if the login uses a compatible login flow as described in the table below.
Enterprise connections Social Login Passwordless connection
If you build a custom login page using, you can enable bot detection to render a CAPTCHA step in scenarios when a login request is determined by Auth0 to be high-risk. Your custom login form code must handle scenarios where the user is asked to pass a CAPTCHA step. To learn more, read Add Bot Detection to Custom Login you build native applications using an Auth0 SDK for the login flow, you can enable bot detection to render a CAPTCHA step in scenarios when a login request is determined by Auth0 to be high-risk. To learn more, read Add Bot Detection to Native nfigure reCAPTCHA Enterprise on Google Cloud PlatformAdd Bot Detection to Custom Login PagesAdd Bot Detection to Native ApplicationsBreached Password DetectionBrute-Force ProtectionSuspicious IP Throttling
What is bot traffic? | How to stop bot traffic | Cloudflare
What is bot traffic?
Bot traffic describes any non-human traffic to a website or an app. The term bot traffic often carries a negative connotation, but in reality bot traffic isn’t necessarily good or bad; it all depends on the purpose of the bots.
Some bots are essential for useful services such as search engines and digital assistants (e. g. Siri, Alexa). Most companies welcome these sorts of bots on their sites.
Other bots can be malicious, for example those used for the purposes of credential stuffing, data scraping, and launching DDoS attacks. Even some of the more benign ‘bad’ bots, such as unauthorized web crawlers, can be a nuisance because they can disrupt site analytics and generate click fraud.
It is believed that over 40% of all Internet traffic is comprised of bot traffic, and a significant portion of that is malicious bots. This is why so many organizations are looking for ways to manage the bot traffic coming to their sites.
How can bot traffic be identified?
Web engineers can look directly at network requests to their sites and identify likely bot traffic. An integrated web analytics tool, such as Google Analytics or Heap, can also help to detect bot traffic.
The following analytics anomalies are the hallmarks of bot traffic:
Abnormally high pageviews: If a site undergoes a sudden, unprecedented and unexpected spike in pageviews, it’s likely that there are bots clicking through the site.
Abnormally high bounce rate: The bounce rate identifies the number of users that come to a single page on a site and then leave the site before clicking anything on the page. An unexpected lift in the bounce rate can be the result of bots being directed at a single page.
Surprisingly high or low session duration: Session duration, or the amount of time users stay on a website, should remain relatively steady. An unexplained increase in session duration could be an indication of bots browsing the site at an unusually slow rate. Conversely, an unexpected drop in session duration could be the result of bots that are clicking through pages on the site much faster than a human user would.
Junk conversions: A surge in phony-looking conversions, such as account creations using gibberish email addresses or contact forms submitted with fake names and phone numbers, can be the result of form-filling bots or spam bots.
Spike in traffic from an unexpected location: A sudden spike in users from one particular region, particularly a region that’s unlikely to have a large number of people who are fluent in the native language of the site, can be an indication of bot traffic.
How can bot traffic hurt analytics?
As mentioned above, unauthorized bot traffic can impact analytics metrics such as page views, bounce rate, session duration, geolocation of users, and conversions. These deviations in metrics can create a lot of frustration for the site owner; it is very hard to measure the performance of a site that’s being flooded with bot activity. Attempts to improve the site, such as A/B testing and conversion rate optimization, are also crippled by the statistical noise created by bots.
How to filter bot traffic from Google Analytics
Google Analytics does provide an option to “exclude all hits from known bots and spiders” (spiders are search engine bots that crawl webpages). If the source of the bot traffic can be identified, users can also provide a specific list of IPs to be ignored by Google Analytics.
While these measures will stop some bots from disrupting analytics, they won’t stop all bots. Furthermore, most malicious bots pursue an objective besides disrupting traffic analytics, and these measures do nothing to mitigate harmful bot activity outside of preserving analytics data.
How can bot traffic hurt performance?
Sending massive amounts of bot traffic is a very common way for attackers to launch a DDoS attack. During some types of DDoS attacks, so much attack traffic is directed at a website that the origin server becomes overloaded, and the site becomes slow or altogether unavailable for legitimate users.
How can bot traffic be bad for business?
Some websites can be financially crippled by malicious bot traffic, even if their performance is unaffected. Sites that rely on advertising and sites that sell merchandise with limited inventory are particularly vulnerable.
For sites that serve ads, bots that land on the site and click on various elements of the page can trigger fake ad clicks; this is known as click fraud. While this may initially result in a boost in ad revenue, online advertising networks are very good at detecting bot clicks. If they suspect a website is committing click fraud, they will take action, usually in the form of banning that site and its owner from their network. For this reason, owners of sites that host ads need to be ever-wary of bot click fraud.
Sites with limited inventory can be targeted by inventory hoarding bots. As the name suggests, these bots go to e-commerce sites and dump tons of merchandise into their shopping carts, making that merchandise unavailable for purchase by legitimate shoppers. In some cases this can also trigger unnecessary restocking of inventory from a supplier or manufacturer. The inventory hoarding bots never make a purchase; they are simply designed to disrupt the availability of inventory.
How can websites manage bot traffic?
The first step to stopping or managing bot traffic to a website is to include a file. This is a file that provides instructions for bots crawling the page, and it can be configured to prevent bots from visiting or interacting with a webpage altogether. But it should be noted that only good bots will abide by the rules in; it will not prevent malicious bots from crawling a website.
A number of tools can help mitigate abusive bot traffic. A rate limiting solution can detect and prevent bot traffic originating from a single IP address, although this will still overlook a lot of malicious bot traffic. On top of rate limiting, a network engineer can look at a site’s traffic and identify suspicious network requests, providing a list of IP addresses to be blocked by a filtering tool such as a WAF. This is a very labor-intensive process and still only stops a portion of the malicious bot traffic.
Separate from rate limiting and direct engineer intervention, the easiest and most effective way to stop bad bot traffic is with a bot management solution. A bot management solution can leverage intelligence and use behavioral analysis to stop malicious bots before they ever reach a website. For example, Cloudflare Bot Management uses intelligence from over 25, 000, 000 Internet properties and applies machine learning to proactively identify and stop bot abuse. Super Bot Fight Mode, available on Pro and Business plans, offers smaller organizations similar visibility and control over their bot traffic.
How to Scrape Websites Without Getting Blocked – ScrapeHero
Web scraping is a task that has to be performed responsibly so that it does not have a detrimental effect on the sites being scraped. Web Crawlers can retrieve data much quicker, in greater depth than humans, so bad scraping practices can have some impact on the performance of the site. While most websites may not have anti-scraping mechanisms, some sites use measures that can lead to web scraping getting blocked, because they do not believe in open data access.
If a crawler performs multiple requests per second and downloads large files, an under-powered server would have a hard time keeping up with requests from multiple crawlers. Since web crawlers, scrapers or spiders (words used interchangeably) don’t really drive human website traffic and seemingly affect the performance of the site, some site administrators do not like spiders and try to block their access.
In this article, we will talk about the best web scraping practices to follow to scrape websites without getting blocked by the anti-scraping or bot detection tools.
Web Scraping best practices to follow to scrape without getting blocked
Respect
Make the crawling slower, do not slam the server, treat websites nicely
Do not follow the same crawling pattern
Make requests through Proxies and rotate them as needed
Rotate User Agents and corresponding HTTP Request Headers between requests
Use a headless browser like Puppeteer, Selenium or Playwright
Beware of Honey Pot Traps
Check if Website is Changing Layouts
Avoid scraping data behind a login
Use Captcha Solving Services
How can websites detect web scraping?
How do you find out if a website has blocked or banned you?
Basic Rule: “Be Nice”
An overarching rule to keep in mind for any kind of web scraping is
BE GOOD AND FOLLOW A WEBSITE’S CRAWLING POLICIES
Here are the web scraping best practices you can follow to avoid getting web scraping blocked:
Web spiders should ideally follow the file for a website while scraping. It has specific rules for good behavior such as how frequently you can scrape, which pages allow scraping, and which ones you can’t. Some websites allow Google to scrape their websites, by not allowing any other websites to scrape. This goes against the open nature of the Internet and may not seem fair but the owners of the website are within their rights to resort to such behavior.
You can find the file on websites. It is usually the root directory of a website –
If it contains lines like the ones shown below, it means the site doesn’t like and does not want to be scraped.
User-agent: *
Disallow:/
However, since most sites want to be on Google, arguably the largest scraper of websites globally, they do allow access to bots and spiders.
What if you need some data, that is forbidden by You could still go and scrape it. Most anti-scraping tools block web scraping when you are scraping pages that are not allowed by
What do these tools look for – is this client a bot or a real user. And how do they find that? By looking for a few indicators that real users do and bots don’t. Humans are random, bots are not. Humans are not predictable, bots are.
Here are a few easy giveaways that you are bot/scraper/crawler –
scraping too fast and too many pages, faster than a human ever can
following the same pattern while crawling. For example – go through all pages of search results, and go to each result only after grabbing links to them. No human ever does that.
too many requests from the same IP address in a very short time
not identifying as a popular browser. You can do this by specifying a ‘User-Agent’.
using a user agent string of a very old browser
The points below should get you past most of the basic to intermediate anti-scraping mechanisms used by websites to block web scraping.
Web scraping bots fetch data very fast, but it is easy for a site to detect your scraper as humans cannot browse that fast. The faster you crawl, the worse it is for everyone. If a website gets too many requests than it can handle it might become unresponsive.
Make your spider look real, by mimicking human actions. Put some random programmatic sleep calls in between requests, add some delays after crawling a small number of pages and choose the lowest number of concurrent requests possible. Ideally put a delay of 10-20 seconds between clicks and not put much load on the website, treating the website nice.
Use auto throttling mechanisms which will automatically throttle the crawling speed based on the load on both the spider and the website that you are crawling. Adjust the spider to an optimum crawling speed after a few trials runs. Do this periodically because the environment does change over time.
Humans generally will not perform repetitive tasks as they browse through a site with random actions. Web scraping bots tend to have the same crawling pattern because they are programmed that way unless specified. Sites that have intelligent anti-crawling mechanisms can easily detect spiders by finding patterns in their actions and can lead to web scraping getting blocked.
Incorporate some random clicks on the page, mouse movements and random actions that will make a spider look like a human.
When scraping, your IP address can be seen. A site will know what you are doing and if you are collecting data. They could take data such as – user patterns or experience if they are first time users.
Multiple requests coming from the same IP will lead you to get blocked, which is why we need to use multiple addresses. When we send requests from a proxy machine, the target website will not know where the original IP is from, making the detection harder.
Create a pool of IPs that you can use and use random ones for each request. Along with this, you have to spread a handful of requests across multiple IPs.
There are several methods can be used to change your outgoing IP.
TOR
VPNs
Free Proxies
Shared Proxies – the least expensive proxies, shared by many users. Chances to get blocked are high.
Private Proxies – usually used only by you, and lower chances of getting blocked if you keep the frequency low.
Data Center Proxies, if you need a large number of IP Address and faster proxies, larger pools of IPs. They are cheaper than residential proxies and coulde be detected easily.
Residential Proxies, if you are making a huge number of requests to websites that block to actively. These are very expensive (and could be slower, as they are real devices). Try everything else before getting a residential proxy.
In addition, various commercial providers also provide services for automatic IP rotation. A lot of companies now provide residential IPs to make scraping even easier – but most are expensive.
Learn More:
How To Rotate Proxies and IP Addresses using Python 3
How to make anonymous requests using TorRequests and Python
A user agent is a tool that tells the server which web browser is being used. If the user agent is not set, websites won’t let you view content. Every request made from a web browser contains a user-agent header and using the same user-agent consistently leads to the detection of a bot. You can get your User-Agent by typing ‘what is my user agent’ in Google’s search bar. The only way to make your User-Agent appear more real and bypass detection is to fake the user agent. Most web scrapers do not have a User Agent by default, and you need to add that yourself.
You could even pretend to be the Google Bot: Googlebot/2. 1 if you want to have some fun! ()
Now, just sending User-Agents alone would get you past most basic bot detection scripts and tools. If you find your bots getting blocked even after putting in a recent User-Agent string, you should add some more request headers.
Most browsers sends more headers to the websites than just the User-Agent. For example, here is a set of headers a browser sent to (Our Web Scraping Test Site). It would be ideal to send these common request headers too.
The most basic ones are:
User-Agent
Accept
Accept-Language
Referer
DNT
Updgrade-Insecure-Requests
Cache-Control
Do not send cookies unless your scraper depends on Cookies for functionality.
You can find the right values for these by inspecting your web traffic using Chrome Developer Tools, or a tool like MitmProxy or Wireshark. You can also copy a curl command to your request from them. For example
curl ” \
-H ‘authority: ‘ \
-H ‘dnt: 1’ \
-H ‘upgrade-insecure-requests: 1’ \
-H ‘user-agent: Mozilla/5. 0 (Macintosh; Intel Mac OS X 10_15_4) AppleWebKit/537. 36 (KHTML, like Gecko) Chrome/83. 0. 4103. 61 Safari/537. 36’ \
-H ‘accept: text/html, application/xhtml+xml, application/xml;q=0. 9, image/webp, image/apng, */*;q=0. 8, application/signed-exchange;v=b3;q=0. 9’ \
-H ‘sec-fetch-site: none’ \
-H ‘sec-fetch-mode: navigate’ \
-H ‘sec-fetch-user:? 1’ \
-H ‘sec-fetch-dest: document’ \
-H ‘accept-language: en-GB, en-US;q=0. 9, en;q=0. 8’ \
–compressed
You can get this converted to any language using a tool like Here is how this was converted to python
import requests
headers = {
‘authority’: ”,
‘dnt’: ‘1’,
‘upgrade-insecure-requests’: ‘1’,
‘user-agent’: ‘Mozilla/5. 36’,
‘accept’: ‘text/html, application/xhtml+xml, application/xml;q=0. 9’,
‘sec-fetch-site’: ‘none’,
‘sec-fetch-mode’: ‘navigate’,
‘sec-fetch-user’: ‘? 1’,
‘sec-fetch-dest’: ‘document’,
‘accept-language’: ‘en-GB, en-US;q=0. 8’, }
response = (”, headers=headers)
You can create similar header combinations for multiple browsers and start rotating those headers between each request to reduce the chances of getting your web scraping blocked.
If none of the methods above works, the website must be checking if you are a REAL browser.
The simplest check is if the client (web browser) can render a block of JavaScript. If it doesn’t, then it pretty much flags the visitor to be a bot. While it is possible to block running JavaScript in the browser, most of the Internet sites will be unusable in such a scenario and as a result, most browsers will have JavaScript enabled.
Once this happens, a real browser is necessary in most cases to scrape the data. There are libraries to automatically control browser such as
Selenium
Puppeteer and Pyppeteer
Playwright
Anti Scraping tools are smart and are getting smarter daily, as bots feed a lot of data to their AIs to detect them. Most advanced Bot Mitigation Services use Browser Side Fingerprinting (Client Side Bot Detection) by more advanced methods than just checking if you can execute Javascript.
Bot detection tools look for any flags that can tell them that the browser is being controlled through an automation library.
Presence of bot specific signatures
Support for nonstandard browser features
Presence of common automation tools such as Selenium, Puppeteer, Playwright, etc.
Human-generated events such as randomized Mouse Movement, Clicks, Scrolls, Tab Changes etc.
All this information is combined to construct a unique client-side fingerprint that can tag one as bot or human.
Here are a few workarounds or tools which could help your headless browser-based scrapers from getting banned.
Honeypots are systems set up to lure hackers and detect any hacking attempts that try to gain information. It is usually an application that imitates the behavior of a real system. Some websites install honeypots, which are links invisible to normal users but can be seen by web scrapers.
When following links always take care that the link has proper visibility with no nofollow tag. Some honeypot links to detect spiders will have the CSS style display:none or will be color disguised to blend in with the page’s background color.
This detection is obviously not easy and requires a significant amount of programming work to accomplish properly, as a result, this technique is not widely used on either side – the server side or the bot or scraper side.
Some websites make it tricky for scrapers, serving slightly different layouts.
For example, in a website pages 1-20 will display a layout, and rest of the pages may display something else. To prevent this, check if you are getting data scraped using XPaths or CSS selectors. If not, check how the layout is different and add a condition in your code to scrape those pages differently.
Login is basically permission to get access to web pages. Some websites like Indeed and Facebook do not allow permission.
If a page is protected by login, the scraper would have to send some information or cookies along with each request to view the page. This makes it easy for the target website to see requests coming from the same address. They could take away your credentials or block your account which can in turn lead to your web scraping efforts being blocked.
Its generally preferred to avoid scraping websites that have a login as you will get blocked easily, but one thing you can do is imitate human browsers whenever authentication is required you get the target data you need.
Many websites use anti web scraping measures. If you are scraping a website on a large scale, the website will eventually block you. You will start seeing captcha pages instead of web pages. There are services to get past these restrictions such as 2Captcha or Anticaptcha.
If you need to scrape websites that use Captcha, it is better to resort to captcha services. Captcha services are relatively cheap, which is useful when performing large scale scrapes.
How can websites detect and block web scraping?
Websites can use different mechanisms to detect a scraper/spider from a normal user. Some of these methods are enumerated below:
Unusual traffic/high download rate especially from a single client/or IP address within a short time span.
Repetitive tasks performed on the website in the same browsing pattern – based on an assumption that a human user won’t perform the same repetitive tasks all the time.
Checking if you are real browser – A simple check is to try and execute javascript. Smarter tools can go a lot more and check your Graphic cards and CPUs to make sure you are coming from real browser.
Detection through honeypots – these honeypots are usually links which aren’t visible to a normal user but only to a spider. When a scraper/spider tries to access the link, the alarms are tripped.
How to address this detection and avoid web scraping getting blocked?
Spend some time upfront and investigate the anti-scraping mechanisms used by a site and build the spider accordingly, it will provide a better outcome in the long run and increase the longevity and robustness of your work.
If any of the following signs appear on the site that you are crawling, it is usually a sign of being blocked or banned.
CAPTCHA pages
Unusual content delivery delays
Frequent response with HTTP 404, 301 or 50x errors
Frequent appearance of these HTTP status codes is also indication of blocking
301 Moved Temporarily
401 Unauthorized
403 Forbidden
404 Not Found
408 Request Timeout
429 Too Many Requests
503 Service Unavailable
Here is what tells you when you are blocked.
To discuss automated access to Amazon data please contact
For information about migrating to our APIs refer to our Marketplace APIs at or our Product Advertising API at for advertising use cases.
Sorry! Something went wrong!
With pictures of cute dog of Amazon.
You may also see response or message from website like these ones from some popular anti scraping tools.
We want to make sure it is actually you that we are dealing with and not a robot
Please check the box below to access the site
Why is this verification required? Something about the behaviour of the browser has caught our attention.
There are various possible explanations for this:
you are browsing and clicking at a speed much faster than expected of a human being
something is preventing Javascript from working on your computer
there is a robot on the same network (IP address) as you
Having problems accessing the site? Contact Support
Authenticate your robot
or
Please verify you are a human
Access to this page has been denied because we believe you are using automation tools to browse the website
This may happen as a result of the following:
Javascript is disabled or blocked by an extension (ad blockers for example)
Your browser does not support cookies
Please make sure that Javascript and cookies are enabled on your bowser and that you are not blocking them from loading
Pardon our interruption
As you were browsing
You’re a power user using moving through this website with super-human speed
You’ve disabled JavaScript in your web browser
A third-party bowser plugin such as Ghostery or NoScript, is preventing Javascript from running. Additional information is available in this support article.
After completing the CAPTCHA below, you will immediately regain access to
Error 1005 Ray ID:
Frequently Asked Questions about bot detection
How bots are detected?
How can bot traffic be identified? Web engineers can look directly at network requests to their sites and identify likely bot traffic. An integrated web analytics tool, such as Google Analytics or Heap, can also help to detect bot traffic.
How do you get around bot detection?
Web Scraping best practices to follow to scrape without getting blockedRespect Robots.txt.Make the crawling slower, do not slam the server, treat websites nicely.Do not follow the same crawling pattern.Make requests through Proxies and rotate them as needed.More items…•Jun 8, 2020
How do you detect a web bot?
Bot Detection TechniquesMouse movements (non-linear, randomized vs linear, patterned)Mouse clicks (bots might have certain uniformed rhythms)Scroll.Key pressed.Total number of requests during a session.The number of pages seen during a session.The order of pages seen and the presence of a pattern.More items…•May 20, 2020

