
Black Proxy Server
Cb Defense: Does the sensor support proxy server a…
Cb Defense Sensor: All VersionsMicrosoft Windows: All Supported VersionsApple macOS: All Supported Versions
Does the Cb Defense sensor support proxy server authentication?
Yes, proxy server authentication is supported. Typically end users will not be required to enter their credentials for proxy authentication because the sensor will attempt to auto-detect the pre-existing proxy server and proxy credential configuration from the local system operating system (when applicable). However, this should be tested prior to sensor deployment.
If the automatic proxy detection doesn’t succeed, first specify server and port with the following command (authentication can be added as needed)
(Windows Sensor): PROXY_SERVER=
(MAC Sensor): -p
LAST_ATTEMPT_PROXY_SERVER=
PROXY_SERVER=10. 10. 1:8000 PROXY_USER=user01 PROXY_PASSWD=P*ssw0rd
To bypass the network proxy or firewall completely, configure the proxy server or firewall to allow outgoing connections from the sensor to the Cb Defense PSC Console. See for more details.
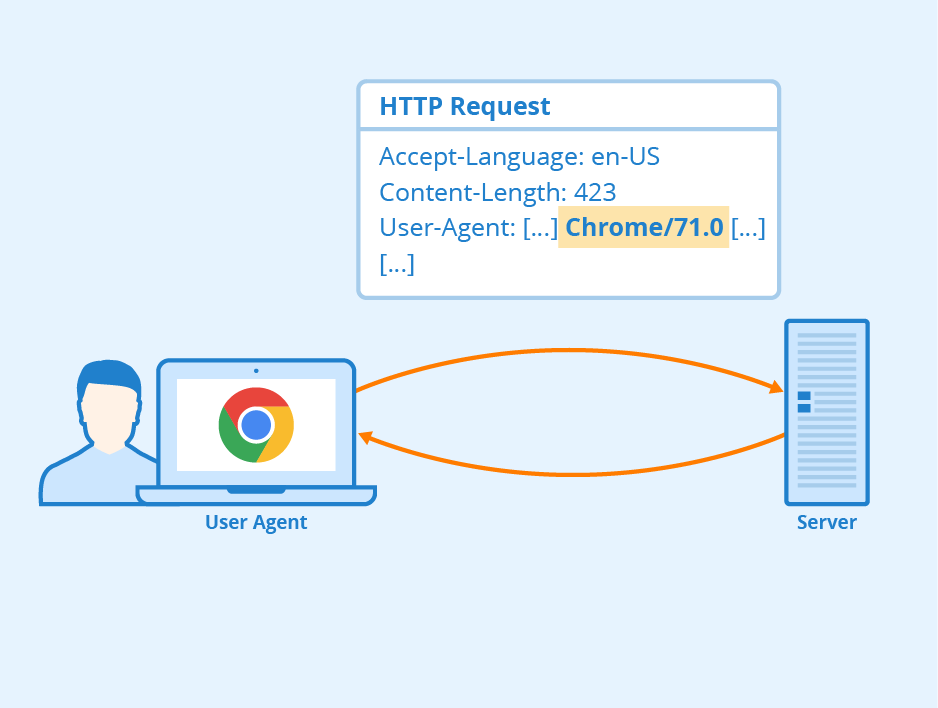
Configure a Proxy – VMware Carbon Black Cloud
The Carbon Black Cloud sensor uses a variety of mechanisms to determine whether a network proxy is present.
If a proxy is detected (or if one is specified at install time), the sensor attempts to use that proxy. If no proxy is detected, the sensor will attempt a direct connection through port 443 or 54443.
The sensor attempts to contact the Carbon Black Cloud backend by using the following methods:
A static configured proxy that is configured during sensor installation.
A direct connection over TCP/443.
Auto-detection of a proxy and proxy credentials (when applicable) from the local computer’s operating system settings.
If you cannot establish connectivity over the standard SSL port, the sensor can fail over to the alternate port, which is TCP/54443.
Note:
Carbon Black Cloud sensors automatically try to detect proxy settings during initial installation. This should be tested. If the automatic proxy detection doesn’t succeed, you must define the parameters to include the Proxy IP and Port in the MSI command line during a command line installation.
If user authentication is required, the user might be prompted for credentials. This typically does not occur in environments that require proxy credentials because the sensor uses an existing configuration that avoids requiring end users to enter credentials.
To avoid going through a network proxy (and/or to avoid being blocked by a firewall), you might need to configure a bypass on your proxy server/firewall to allow outgoing connections from the sensor to the backend. Options for bypass configuration include the following:
Configure a bypass on your firewall or proxy to allow outgoing connections to your Carbon Black Cloud domain over TCP/443.
Configure a bypass in your firewall or proxy to allow outgoing connections to the Carbon Black Cloud alternate port TCP/54443.
Important: The host domain name for the
Carbon Black Cloud backend server is included in the server’s certificate. Some network proxies and gateways might try to validate the certificate and deny the
Carbon Black Cloud backend application connection because of a name mismatch between the certificate and real host name of the system that is running in AWS. If this occurs, you must configure the proxy or gateway so that it does not validate the backend server certificate. Note that you cannot access the certificate or hostname in the server’s certificate.
Black proxy server – Fineproxy
How to disable a proxy server in Firefox?
Turning off the proxy server in Firefox is comparably simple. We’ll describe a simple set of procedures you have to do below. Click the icon to open the browser and access the Tools section. Look for the Options and choose Advanced. In the window opened, select Network, and finally, reach out to the Settings menu. There will be a bunch of options. Your preferable one is obviously the No proxy mode. Agree to save, close the window, and make sure to be able to use the Internet without a proxy on.
What are rotating proxies?
During web scraping or collection of data from several websites, you can face a problem because security systems can block your IP address. You can apply rotating proxies to prevent the blockage of your home IP address. Rotating proxies are the systems that create new IP addresses for you as often as you want. You can set a period or a number of requests after which you want the service to generate a new proxy for you. Moreover, these proxies are residential, so only you will have access to their activity.
What is an HTTPS proxy?
HTTPS is an extension to HTTP; it’s not a separate protocol. Data from the client to the source server and back is transferred over the SSL and TLS cryptographic protocols with such a connection.
The probability of hacker attacks during HTTPS connection is excluded only if a verified public and private key certificate are installed on the source server system. The public and private key certificate is needed not only to protect against hacker attacks but can also be used to give only authorized users access to the server.
How to test a proxy?
Proxy testing is an important process by which you can check if your proxies really work or even save yourself from unnecessary waste. Some proxy sellers give you money back if your proxies don’t work as expected, but there is a limited period of time for verification.
There are three basic methods of how you can do it. You can use the online IP Checker and check if a server changes your location and IP address. You can use a free tool like FOGLDN Proxy Tester that allows you to test not only performance but also speed. Finally, you can try the IP database, which will show you the type and anonymity of your proxies.
What is a sip proxy?
Today, you can make phone calls not only using landline telephony or cellphones. You can also use the Internet. Making voice (and video) calls via the Internet is possible due to the SIP, which stands for Session Initiation Protocol. This is the technology that consolidates various elements necessary for internet phone calls. A SIP proxy server operates as a receiver and a processor of incoming SIP data that travels from distant endpoints. As a result, the established connection transmits audio and video data.
What is a squid proxy?
A Squid proxy server is a type of caching server used in Linux OS and Unix platforms. A Squid proxy server operates as data storage, and redirects requested information to the closest computer (if the requested server sits further than the Squid proxy server). This makes for faster responses and helps decrease bandwidth usage.
How to use a proxy to access blocked sites?
One of the great benefits of using a proxy is that it allows you to access blocked content. For instance, you can’t watch a cool YouTube video or visit a foreign news site. There is no need to collect your belongings and move. Just install a proxy on your gadget.
The specific guidelines depending on which system your gadget is using to operate. Although in general, the steps are always the same:
You find proxies using free sites or sellers
Check them on special services
Go to the network settings of your browser or gadget
Look for additional or advanced network settings
Switch to manual mode
Enter the required information
Save the result
How to use a proxy in Opera?
In this age, it is very important to follow the rules of using security on the network. One of these ways can be the use of a proxy, which acts as a filtering intermediary between you and the web. When applying such a server, you can not only gain access to content banned in your region but also increase your anonymity and protection on the network. To do this, you require to buy or find free proxies. After that, it is highly advisable to test them utilizing available free tools such as an IP checker. Then you can add them to Opera settings. Open your browser settings and tap Advanced (it will be on the left), then go to the Browser. Find the System tab and go to the proxy settings.
What is the purpose of a proxy server?
A proxy server can execute several functions. The most famous of them is obviously anonymity. To execute this function proxy server hides the IP address of a computer and makes it look like an internet page was accessed from the IP address of a proxy server.
The second function of a proxy server is to filter internet traffic. For example, a proxy can check all emails entering an address for viruses, spam, or size limitations, facilitating the work of a company.
The third function is networking. As an example, your wifi router at home is also a proxy because every computer connected to it will enter the internet under the same IP address.
How do proxy servers work?
A proxy server is a PC with its own one-of-a-kind IP address, to which your web requests go first. For the usage of the internet, an IP address is required. It’s always granted to your computer or other device based on the home address. Such IPs are known as residential ones. When you go searching for anything on the web, a proxy server, as a mediator, is the first one to get your requests. After that, the server finds the info needed and gives it back to you, the user. But the residential IP address has its own certain restrictions, such as geographical ones, which will not allow you to visit some websites that are frozen in your region. In order to overcome this problem, other types of proxies are used.
How to set a proxy in Firefox?
Mozilla Firefox stands out among other popular browsers as it has more options for setting up a proxy. Unlike Chrome or Internet Explorer, which use only system-wide settings, it allows you to customize the proxy settings. Besides, with Firefox, it is possible to choose the SOCKS-protocol version you need and make remote DNS requests when using SOCK5.
Setting up a proxy server starts with opening the Firefox menu. The button is located at the upper right corner right below the close button (the instructions are written for Firefox Version 89 but can be used for earlier ones). Click the “Setting” option (you automatically get to the “General Settings” window) and scroll the screen down till you get to the “Network Settings” section. Click the “Settings” button and choose one of the five proxy options. Your next steps depend on whether or not you want to use a proxy and, if you do, what type of proxy you wish to set up. The options are the following: no proxy, auto-detect proxy settings, system proxy settings, manual configuration, and automatic configuration.
What is a proxy used for?
There are many functions a proxy server can perform. The main one is to act as an intermediary between a user’s computer (local network) and the global network. The traffic goes through a proxy server on its way to the final destination (a web resource). The request travels back to the proxy, and then the server transmits the content from the resource to you. Now that you know how a proxy works, you can guess another important function — adding a level of security. It runs as a filter preventing you from assessing dangerous websites and seeing inappropriate content. On the other hand, proxies help users to maintain anonymity and privacy, thus, making content from blocked sites available for some users.
How to change proxy setting in Chrome?
As in many other cases, your first step would be to find Chrome settings, which location is on the top right’s angle of the three dots figure. Scroll down and choose the “Advanced” button, then search for “Open proxy setting. ” Here, in accordance with the situation, you can either delete the proxy or click on these proxy settings and configure them on your computer. The second option would be to google for browser proxy extensions and implement one of them on your browser.
What is web proxy authentication?
Web proxy authentification is used for the creation of a gateway for an internet page or a service. This proxy collects data of clients and requires them to enter a password and other information (for example, login) each time when a client tries to enter the site. Normally this option is disabled. However, when web proxy is enabled, it becomes possible to control the web environment and therefore investigate the actions of every user.
What are socks proxies?
The SOCKS proxy is one of the methods people use to protect their computer from identifying its location. This is a protocol that allows connecting your device to the desired server through the mediator. So, the final destination of the connection will be achieved from a third-party IP address, and it will hide your local IP. The usage of SOCKS proxy is practical when you want to overcome geographical barriers. However, you should be aware that these proxies do not encrypt data, and it means that you still should take care of its security.
Frequently Asked Questions about black proxy server
What is a proxy server used for?
A proxy server is a system or router that provides a gateway between users and the internet. Therefore, it helps prevent cyber attackers from entering a private network. It is a server, referred to as an “intermediary” because it goes between end-users and the web pages they visit online.
Is proxy server legal?
Yes, it is legal to use a proxy server. Proxies have many different uses, including enabling remote work; setting up a support system for users who are located outside a particular network; protecting networks and Internet users from malicious content; streaming online content from outside a country and more.
What does it mean to be behind a proxy server?
A proxy server acts sort of like a middleman between your browser and servers that display Web pages. … Many businesses use proxy servers to block access to certain sites or provide network users with more anonymity while surfing the Web.

