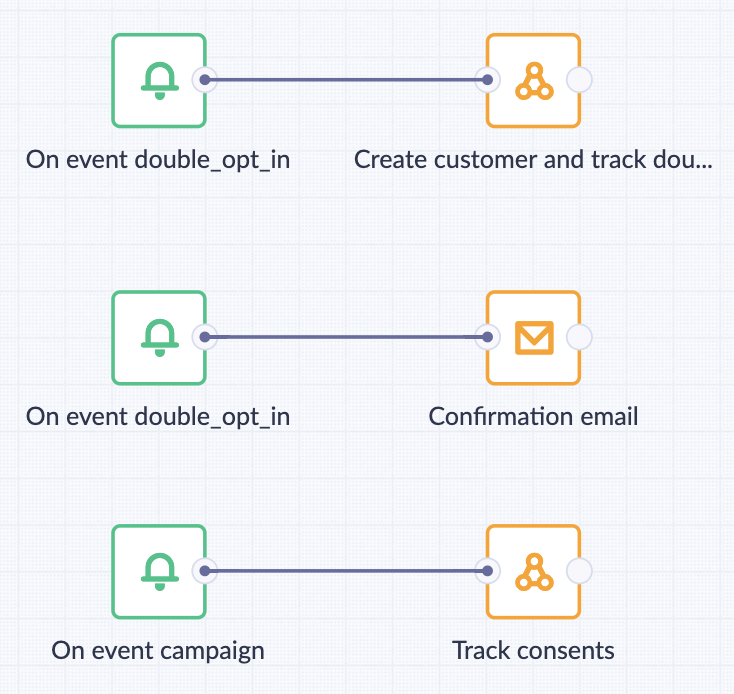
Proxy And Firewall Difference

Difference between Firewall and Proxy Server – GeeksforGeeks
1. Firewall:Firewall is software program that prevents unauthorized access to or from a private network. All data packets in it are entering or dropping network passes through the firewall and after checking whether the firewall allows it or not. All traffic must pass through the firewall and only authorized traffic must pass. It is a system located between two networks where it implements an access control policy between those networks. It works on network layer of the OSI model and uses encryption to encrypt the data before transmission. 2. Proxy Server:Proxy Server is a server that acts as a gateway or intermediary between any device and the rest of the internet. A proxy accepts and forwards connection requests, then returns data for those requests. It uses the anonymous network id instead of actual IP address of client (means it hides the IP address of client), so that the actual IP address of client couldn’t be reveal. Difference between Firewall and Proxy Server FirewallProxy Server1Firewall can monitor and filter all the incoming and outgoing traffic on a given local server connects an external client with a server to communicate with each other. 2It blocks connections from unauthorised facilitates connections over network. 3It filters data by monitoring IP packets that are filters the client-side requests that are made to connect to the network. 4It involves network and transport layer work on application layer data. 5It exist as an interface between a public and private can exist with public networks on both sides. 6It is used to protect an internal network against attacks is used for anonymity and to bypass restrictions. 7The overhead generated in firewall is more as compared to a proxy overhead generated in proxy server is less as compared to a firewall. 8It works on the packet level. It works on application protocol tention reader! Don’t stop learning now. Get hold of all the important CS Theory concepts for SDE interviews with the CS Theory Course at a student-friendly price and become industry ready.

What Is a Proxy Firewall and How Does It Work? | Fortinet
What Is a Proxy Firewall?
A proxy firewall is the most secure form of firewall, which filters messages at the application layer to protect network resources. A proxy firewall, also known as an application firewall or a gateway firewall, limits the applications that a network can support, which increases security levels but can affect functionality and speed.
Traditional firewalls are not designed to decrypt traffic or inspect application protocol traffic. They typically use an intrusion prevention system (IPS) or antivirus solution to protect against threats, which only covers a small fraction of the threat landscape that organizations now face.
A proxy server addresses this gap by providing a gateway or intermediary between computers and servers on the internet to secure data that goes in and out of a network. It determines which traffic should be allowed and denied and analyzes incoming traffic to detect signs of a potential cyberattack or malware. A proxy server firewall caches, filters, logs, and controls requests from devices to keep networks secure and prevent access to unauthorized parties and cyberattacks.
How Do Proxy Firewalls Work?
A proxy firewall is considered the most secure form of firewall because it prevents networks from directly contacting other systems. It has its own Internet Protocol (IP) address, which means an external network connection cannot receive packets directly from the network.
A proxy firewall works by providing a single point that enables organizations to assess the threat level of application protocols and implement attack detection, error detection, and validity checks. It uses tactics like deep packet inspection (DPI) and proxy-based architecture to analyze application traffic and discover advanced threats.
A proxy network will likely have one computer directly connected to the internet. Other computers in the network access the internet by using the main computer as a gateway, which enables the proxy to cache documents requested by multiple users. A user attempting to access an external site through a proxy firewall would do so through this process:
The user requests access to the internet through a protocol such as File Transfer Protocol (FTP) or Hypertext Transfer Protocol (HTTP).
The user’s computer attempts to create a session between them and the server, sending a synchronize (SYN) message packet from their IP address to the server’s IP address.
The proxy firewall intercepts the request, and if its policy allows, replies with a synchronize-acknowledge (SYN-ACK) message packet from the requested server’s IP
When the SYN-ACK packet is received by the user’s computer, it sends a final ACK packet to the server’s IP address. This ensures a connection to the proxy but not a valid Transmission Control Protocol (TCP) connection.
The proxy completes the connection to the external server by sending a SYN packet from its IP address. When it receives the server’s SYN-ACK packet, it responds with an ACK packet. This ensures a valid TCP connection between the proxy and the user’s computer and between the proxy and the external server.
Requests made through the client-to-proxy connection then the proxy-to-server connection will be analyzed to ensure they are correct and comply with the corporate policy until either side terminates the connection.
This process ensures a highly secure network that provides deep inspection of the contents of every packet that flows in and out of a network.
Examples of a Proxy Firewall’s Work
Proxy servers are often implemented through bastion hosts, which are systems likely to come under direct cyberattack. Proxy firewalls monitor network traffic for core internet protocols, such as Layer 7 protocols, and must be run against every type of application it supports. These include Domain Name System (DNS), FTP, HTTP, Internet Control Message Protocol (ICMP), and Simple Mail Transfer Protocol (SMTP).
A proxy firewall is essentially a go-between for every connection on a network. Every computer on the network establishes a connection through the proxy, which creates a new network connection. For example, if a user wants to visit an external website, then packets are processed through an HTTP server before they are forwarded to the requested website. Packets from the website are then processed through the server before being forwarded to the user.
Proxy firewalls centralize application activity into one single server. This enables organizations to inspect packets for more than simply source and destination addresses and port numbers. As a result, most firewalls now have some form of proxy server architecture.
Proxy firewalls will often be deployed within a set of trusted programs that support a specific application protocol. This ensures complete analysis of the protocol’s security risk and offers enhanced security control than is possible through a standard firewall.
Advantages and Disadvantages of Proxy Firewalls
Proxy firewalls offer advanced network security levels, but at the same time, can impact network speed and performance.
Advantages
The main goal of a proxy firewall is to provide a single point of access. This enables organizations to assess the level of threat posed by application protocols, effectively detect threats, and check the validity of network traffic. A proxy firewall also enables refined setup control, which allows organizations to fine-tune it to their network needs and corporate policies.
A proxy firewall also prevents direct connections between a user’s computer and the external sites they want to visit, which offers substantial security benefits. It offers one of the most secure network connections possible because it provides deep inspection of every data packet in and out of a network. This ensures organizations can prevent the most sophisticated and high-risk malware attacks.
Disadvantages
Despite the extra security a proxy firewall offers, there are drawbacks to the approach. One of the main disadvantages is that a proxy firewall creates a new connection for each outgoing and incoming packet. This can result in the firewall creating a bottleneck in traffic flow, significantly slowing down the process and negatively affecting network performance, and creating a single point of failure. Some proxy firewalls might only support particular network protocols, which limits the applications that the network can support and secure.
How Fortinet Can Help
Fortinet protects organizations’ networks with its secure web gateway (SWG) solution FortiProxy, a high-performance proxy that consists of physical and virtual appliances. The solution is designed to ensure compliance, threat protection, visibility, and web security for organizations of all sizes.
FortiProxy is a secure, unified web proxy product that protects organizations from web-based attacks through advanced threat defense, malware protection, and Uniform Resource Locator (URL) filtering. This defends users against internet-based threats and enforces corporate policy compliance.
FortiProxy incorporates multiple threat detection techniques deployed as a bundle that offers crucial network protection tools and functionalities. This includes advanced threat protection (ATP), antivirus, data loss prevention (DLP), DNS filtering, FortiSandbox Cloud, intrusion prevention, secure sockets layer (SSL) inspection, and web filtering. It is effective in reducing organizations’ bandwidth demands and optimizing their network with content and video caching. The solution also includes advanced caching and wide-area network (WAN) optimization, as well as a content analysis add-on service that helps organizations detect toxic or offensive visual content.
Crucially, the services and licenses included in the Fortinet bundle are all-inclusive and cannot be purchased individually. This offers a major cost advantage compared to being charged for each individual service separately and purchasing expensive individual renewals.
Information Security MCQs – Computer Science – EXAMRADAR
This section contains more frequently asked Information Security MCQs in the various competitive exams.
1. Which of the following are possible security threats?
Illegitimate use
Backdoors
Masquerading
All of the given options are correct
2. What is a firewall?
Firewalls are network-based security measures that control the flow of incoming and outgoing traffic
A firewall is a program that encrypts all the programs that access the Internet.
A firewall is a program that keeps other programs from using the network.
Firewalls are interrupts that automatically disconnect from the internet when a threat appears
3. Which of the following involves submitting as many requests as possible to a single Internet computer or service, overloading it and preventing it from servicing legitimate requests?
Distributed denial-of-service attacks
Backdoor
Phishing
4. Which of the following symmetric keys can be derived from Symmetric master key?
Authentication keys
Key wrapping keys
Data encryption keys
5. Which of the following are valid Cryptographic key types?
Public authentication key
Public signature verification key
Private signature key
6. Is true that HTTP is an insecure protocol?
True
False
7. Which is the best way a system can be hardened?
Total disk encryption coupled with strong network security protocols.
White-list ad filtering only.
Installing a commercial security suite.
Virus scanning only.
8. Why is it crucial to encrypt data in transit?
To assure that all of your information cannot be decrypted.
To decrease your resources.
So you can increase your chances of testing your encryption capabilities.
To prevent unauthorized access to private networks and sensitive information during its most vulnerable state.
9. Which of the following are the basic functionalities of the IPsec Protocol?
Security association for policy management and traffic processing
Security protocols for AH and ESP
Manual and automatic key management for the internet key exchange
10. Can a proxy be used as a firewall? If so, how?
No. Proxies are data encryption stations whose sole purpose is to encrypt and re-rout data.
No. Proxies are firewalls that are maintained at locations other than that of the user.
No. All a proxy does is re-rout Internet traffic, and thus all the malicious signals that go with it.
Yes. A proxy acts as a network intermediary for the user that serves to control the flow of incoming and outgoing traffic.
You may be interested in:
Cyber Security Online Tests
Cryptography in the Networking MCQs
Network Security MCQs
Security in Internet – IPSEC-SSL-TLS-PGP-VPN-FIREWALLS MCQs
Cyber Security Tutorials
If you have any Questions regarding this free Computer Science tutorials, Short Questions and Answers, Multiple choice Questions And Answers-MCQ sets, Online Test/Quiz, Short Study Notes don’t hesitate to contact us via Facebook, or through our us @ [email protected] We love to get feedback and we will do our best to make you happy.
Frequently Asked Questions about proxy and firewall difference
What is proxy and firewall?
A proxy firewall is the most secure form of firewall, which filters messages at the application layer to protect network resources. … A proxy server addresses this gap by providing a gateway or intermediary between computers and servers on the internet to secure data that goes in and out of a network.
Can a proxy be used as a firewall?
Can a proxy be used as a firewall? … All a proxy does is re-rout Internet traffic, and thus all the malicious signals that go with it. Yes. A proxy acts as a network intermediary for the user that serves to control the flow of incoming and outgoing traffic.
Is VPN a proxy firewall?
A VPN is quite similar to a proxy. Your computer is configured to connect to another server, and it may be that your route web traffic through that server. But where a proxy server can only redirect web requests, a VPN connection is capable of routing and anonymising all of your network traffic.Dec 12, 2018