
How To Control Someones Computer Using Their Ip Address

How to Access Another Computer Using an IP Address – Small …
Often when you’re working on a computer, you need to connect to other computers to run software or check data on them. This could involve connecting to a business server used by your work team or opening a remote desktop session on your work PC from home. Either way, if you know the computer’s domain name or IP address, there are several tools to make this possible. Remote Computer Access With Remote Desktop One of the most common tools to connect to a remote Microsoft Windows computer is Microsoft’s Remote Desktop. This software enables you to connect to a computer running Windows 10 or many earlier versions of the operating system from another Windows computer or a smartphone running Android or iOS. It allows you to remotely control the computer using your keyboard and mouse, using the standard Windows interface. Before you can connect to a computer with Remote Desktop, you must enable it on the computer you’re connecting to. To do this, click the “Start Menu” and select “Settings. ” Within the Settings menu, click “Remote Desktop” and then choose “Enable Remote Desktop. ” Make a note of the name of the computer. Then, on another Windows computer, open the Remote Desktop app and type the name or IP address of the computer you want to connect to. You can also do this on a smartphone running iOS or Android using the Microsoft Remote Desktop app from the App Store or Google Play store. There are other third-party clients for the Remote Desktop protocol, known as RDP, which you can download for other operating systems. Other Remote Computer Access Tools In addition to Remote Desktop, other tools you can use to access a computer remotely include open-source VNC, which stands for Virtual Network Console. Like Remote Desktop, it allows you to use your keyboard and mouse to control a remote computer. Several VNC software packages are available, and you usually must install VNC on both your local computer and the remote computer you plan to control. Other commercial software, such as TeamViewer, is available for remote desktop connections or sharing your screen during conference calls and meetings so others can see data on your computer. SSH, which stands for Secure Shell, is often used by programmers and system administrators to talk to remote servers. Unlike Remote Desktop and VNC, SSH opens a command line connection to a remote computer, although you can also forward remote graphical and online content to your machine in many situations. It’s more commonly used to connect to Linux and other Unix systems than to Windows or Mac computers. You need to know the remote computer’s name or IP address to connect with SSH or VNC. Finding Your IP Address If you need to connect to a remote computer and aren’t sure of the IP address, you can check it in the Windows settings. Click the “Start Menu” and then “Settings. ” In the Settings menu, click “Network & Internet. ” If you’re using a wired connection on the computer, click “Ethernet” and then your connection to see the IP address. If you’re using a Wi-Fi connection, click “WiFi” and then “Advanced Options. ” Your IP address is a series of numbers separated by dots.

How to Remote Access a Computer Using IP Address?
Computing devices have come a long way over the last years. The modern family now has become mobile in the sense that now they have smartphones, tablets and various other gadgets with rich networking capabilities. Now, it’s easy for them to do home networking and remote access a computer with IP address.
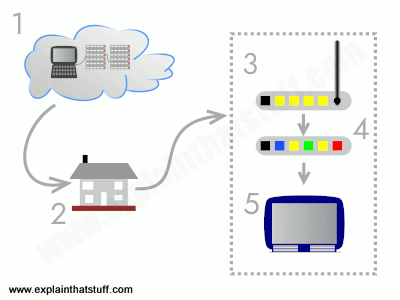
Home networking could be totally possible if you know how to configure your home router and other devices for you to be able to remote access a computer with IP address. To do that, there are a few things that you need to understand, including WAN(Wide Area Network), LAN (Local Area Network), DNS(Domain Name System) and many else.
While all of this might seem overwhelming and too technical, it is quite easy if you are familiar with the router’s Web interface. Just make sure to have a good backup of the settings before making any changes.
Basic terms to successfully remote access a computer with IP address
For you to be able to successfully remote access a computer with IP address, it is great to know some of the basic concepts involving home networking.
Gateway
Most of the internet providers supply their subscribers with devices that combine the functionality of a router and modem in a single pack. The router acts as the gateway that allows you to connect multiple devices to a network, while the modern establishes a connection to the internet. This is very vital if you want to remote access a computer with IP address successfully.
Connections
There are three options when you want to setup a home network and be able to remote access a computer with IP address.
1. WiredWith a wired type of network, you are using Ethernet cables into a network adapters to establish a connection. Although it lack mobility and generally suited for desktops, they do have their advantages. Since they provide a direct type of connection, wired network are able to transfer data faster and more stable. It also provide considerably better security among others and is best when you remote access a computer with IP address.
2. WirelessWireless technology excels in mobility and convenience. However, it is essentially a compromise in terms of performance, security and reliability. The number of devices, obstruction-free router and proper use of security protocols are vital when deploying a wireless network. You have to make sure, you have established your security well before you remote access a computer with IP address.
3. Powerline NetworkingThis is more popular nowadays. With this type of connection, you need to plug a special receiver into your wall outlet, which connects to and communicates with your networked devices over an encrypted signal. It is also good if you remote access a computer with IP address. This method doesn’t add any additional costs to utility bills and offers a degree of reliability that is somewhere between wired and wireless networking.
DevicesIt is possible to connect far more than desktop and laptop computers to a network. Same goes with remote access a computer with IP address. Printers, network storage devices and a host of mobile gadgets, they can all be connected to the network.
In most cases, your devices will have to be manually configured. Your configuration will depend on the operating system running on your central networking computer.
Forming the network before you remote access a computer with IP address
Establishing your network is typically a matter of connecting the devices you want to integrate to your router. It may require cables depending on the device. Wireless products come equipped with built-in Wi-Fi capabilities that eliminate the need to build any physical wires.
With all the setup you have made, the last thing you need to do before you remote access a computer with IP address is make sure you have a data and network protection like Comodo Internet Security Software that gives you complete protection against viruses and any type of attacks.
Building a network in your home has lots of challenges, but the benefits of it outweigh the negatives. You should pay attention to all essentials, and you will be reaping the perks of your own home-based network.
Related Resources:
Remote Access
Best Remote Desktop Software
Remote Desktop Connection Manager
BEAST Attack
Backdoor Website
499 Error Code
Remote Access Software
Free Remote Desktop
Website Safety Check
HTTPS
Control Someones Computer by Their Ip – WonderHowTo
How To:
Set up & enable Remote Desktop in Windows Mobile
In this tutorial Brandon from will show you how to set up and use your remote desktop on a Windows mobile smart phone. Windows mobile remote desktop allows you to remotely access and control your Windows computer from your cellphone device, it is just like contro..
Hack into a Windows computer
This is how to hack a computer for educational purposes. First you need its IP address, radmin viewer 3. 3 or later, and an open port scanner. Okay so first you need the IP and scan the IP address of the computer. Now find what open port it has. Ok then open up radmin viewer an..
Turn Your House Lights On & Off Using the Internet
Haven’t you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security..
Find your IP address in Windows 7 and Vista
In this video tutorial, viewers learn how to find their I. P address in Windows 7 and Vista. Begin by clicking on the Start menu. Then type “cmd” into the search bar and press Enter. When the command prompt window opens, type in “ipconfig” and press the Enter button. Now search..
Find the IP address of a printer
In this video, we learn how to find the IP address of a printer on your computer. Before you begin, make sure you start on your main desktop. First, click on the “start” menu, then click on “control panel” and last click on “printers and faxes”. Once you’re in there, right cli..
Configure your Mac to accept VNC connections
This video demonstrates how to set your Mac up to accept VNC we open up the “system preferences”. Double click on Sharing and then go down to remote management and check this. We can see some options. Check the options Open and quit the application, Change s..
Hacker Fundamentals:
The Everyman’s Guide to How Network Packets Are Routed Across the Web
In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts. In the last Hacker Fundamentals, we talked about the OSI model as well as a little on TCP/IP and the protocols that make..
Hack Like a Pro:
How to Cover Your Tracks So You Aren’t Detected
Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevol..
Real Scenarios #1:
The New MacBook
You’re at your friend’s house. All you’ve heard about all day is his new laptop. He’s got a brand new top-specced MacBook Pro, and he won’t stop going on about it. It particularly annoys you as all you’ve got is a 4 year old cheap laptop, even if it is running Linux. If only..
Your Complete Guide to Using Remote Desktop on the Microsoft Surface and Windows 8
Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely. Left an important document on your work computer? Want to run a legacy x86 desktop app from your Surface? You can use Remote Desktop..
How to Save the World from Nuclear Annihilation
Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this in..
Cripple Websites with DDoS Attacks or Auto-Hacking Botnets
WikiLeaks. In recent weeks, it’s been the hottest topic on the web. It’s been attacked on a multinational level by political influence peddling. First, U. S. Senator Joe Lieberman swayed Amazon’s decision to stop hosting WikiLeaks. Then, Tableau Software removed graphs from th..
Control your PC from anywhere
Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episode..
Hack a remote Internet browser with XSS Shell
XSS Shell is a cross-site scripting backdoor into the victim’s browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim’s browser; however, the XSS Shell keeps the connection betwe..
Play Better in Counter Strike Source
So You’re New to Counter Strike Source? So you’re new to Counter Strike Source and you want to improve your gameplay? Great. You’ve come to the right place. The first step to improving your game is to admit that you are a NEWB or NEWBIE. Do not confuse this with NOOB. A “new..
Spy on Your “Buddy’s” Network Traffic: An Intro to Wireshark and the OSI Model
Wouldn’t it be nice to just sit at your buddy’s house, plug into his network, and see exactly what he’s doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared E..
Control iPhone/iPod Touch from a computer
In this video from iPT2gGeec we learn how to control an iPhone from your computer. You need a jailbroken iPhone to do this and use a program called Veency. Open Cydia. Search for Veency. Install it. That is all you need to do with your iPhone. Now to get it to work on your co..
Bypass Common Windows Restrictions, Activate God Mode, and More
A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc. Obviously, not all places use the same methods, and not all of the m..
Control an iPhone from a computer
In this tutorial, we learn how to control an iPhone from a computer. First, go to Google and search for “real vnc”. Then, download and install the program. Now, go to your iPhone and open the program “Cydia” up. Once opened, search for a program called “veency” and download an..
Control iTunes with your iPhone
All you need to remotely access your computer’s iTunes library is your iPhone. Control itunes with your iPhone with this Howcast guide. You Will Need * An iPhone or iPod Touch with software version 2. 0 or later * A computer with iTunes 7. 7 or later * A wireless network Step..
Control your computer remotely via your iPod Touch
This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer’s IP address. Click on Download Here..
Mastering Security, Part 2:
How to Create a Home VPN Tunnel
When you’re out and about in the dangerous world of Wi-Fi, it’s hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Priv..
Pull a compilation of computer pranks on a friend
In this video, we learn how to pull a compilation of computer pranks on a friend. The first trip is a mouse prank where you will open up the control panel and find the mouse settings. From here, you can switch the buttons from left to right and change the speeds of the mouse…
Update a website with an FTP client (à la FileZilla)
In this Computers & Programming video tutorial you will learn how to update a website with an FTP client (v† la FileZilla). Download FileZilla client from. Find your server IP address from your web host, which will be found in the hosting control cent..
Change the default Windows Remote Desktop port
In this Computers & Programming video tutorial you will learn how to change the default Windows Remote Desktop port. It is actually a registry hack. You can check the IP address of our machine by typing ipconfig into the cmd prompt. For hacking into a machine, you should have..
Quickly find an IP address
In this video tutorial, viewers learn how to find an I. P. address. Every computer that has Internet connection has a unique identifier called a Internet Protocol Address. This video provides 2 methods on how to find your I. The first method is to simply open your we..
Remotely Control Computers Over VNC Securely with SSH
VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense th..
SSH into a jailbroken iPod Touch or iPhone
In this video from rscp1050 we learn how to SSH into a jailbroken ipod touch or iphone. First go into Cydia and search for SSH. You need to download OpenSSH. Then also install Toggle SSH. After installed, restart the iphone. Now on your computer, download WinSCP. Once installe..
Setup a VPN connection on Windows XP
1. Describes how to setup a VPN connection on Windows XP. Goto Start-> Control Panel-> Network connections. 3. Then click on “Create a new connection” under the Network task panel. 4. Click Next. 5. Then select the “Connect to the network to my workplace’ radio button…
Open a port for torrent downloading
This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window. Press..
A Hitchhiker’s Guide to the Internet: A Brief History of How the Net Came to Be
You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering… how would someone take down th..
Assign a Static IP Address in Windows 7
This article will be about setting up a static IP (Internet Protocol) address in Windows Seven. To see whether you should set one up, ask yourself the following: Do I have many computers in the house hold? Do I get connection issues often? Did you answer yes to both? Then you..
Hack Wireless Router Passwords & Networks Using Hydra
Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they’ve penetrated your network, hackers will change your router settings so they’ll have an easy way back in. This allows them to change your network into a she..
Share Your Laptop’s Wireless Internet with Ethernet Devices
Sharing a laptop’s wireless Internet connection with other computers connected to its Ethernet port is a great skill to know. It can be good for a number of reasons; Your computer may not have proper hardware to have a standard setup, or you may have an awkward network topolog..
Run a Free Web Server From Home on Windows or Linux with Apache
Paying for web hosting isn’t ideal in most situations. If you have your own website, hosting it yourself is very acceptable and easy to do, assuming your internet bandwidth permits. Most people want to run a personal site, nothing crazy, so hosting from home on low-bandwidth i..
Run an FTP Server from Home with Linux
File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common w..
Make Your Internet Faster in Windows XP, 7, Vista and Mac OS X
How to Make the Internet Faster in Windows 7 Go to Control Panel. Click on your Start menu, and then select the Control Panel. Click on Network and Internet. Click on View Network Stats and Tasks. Find the Internet Protocol. Find your network and click on it. B. A dialog..
News:
Anonymity, Darknets and Staying Out of Federal Custody, Part One: Deep Web
You’ve probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images ar..
Defeat SSL in Practice with SSL Strip
SSL stands for Secure Socket Layer. It’s an encryption standard used on most sites’ login pages to avoid their users’ passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an “” connection. So, w..
An Entry Level Guide to Finding and Reading Logs (And Maybe Staying Out of Jail)
Big brother is watching when you’re playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying vario..
Anonymity Networks. Don’t use one, use all of them!
Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the “best” one to use the answer is simple. Use all three! Each anonymity network is designed for a different specific purpose. One network al..
A Tale of Two Standards
If you read my article on the OSI model, you got a good overview on communications from that model’s perspective, but how does that relate to TCP/IP? We’re going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC a..
Use VNC to Remotely Access Your Raspberry Pi from Other Devices
With Virtual Network Computing, you don’t need to carry a spare keyboard, mouse, or monitor to use your headless computer’s full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone. Virtual Network Computing, be..
Advice from a Real Hacker:
How to Know if You’ve Been Hacked
It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn’t reach the headlines are the many individual breaches that happen..
Analyzing the Hacks:
The Girl in the Spider’s Web Explained
The latest film addition in the American-produced Millennium series, The Girl in the Spider’s Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centere..
Set Up a Headless Raspberry Pi Hacking Platform Running Kali Linux
The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners,..
Secure Your Identity & Become Anonymous Online in 2019
Your social security number, credit card information, and medical history can fall into the wrong hands if you’re not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself..
Gain Complete Control of Any Android Phone with the AhMyth RAT
There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device’s location, see SMS messages, take c..
Control Apps & System Functions on Your Mac Using Your Samsung Galaxy S3
I still remember when I had to get up from my comfy spot on the couch to change the channel on my old television. So for me, the remote control may be one of the most underrated inventions of the last century. These days, remotes take on all sorts of shapes, not just the typic..
Locate & Exploit Devices Vulnerable to the Libssh Security Flaw
Computers all over the world rely on a program called “libssh” to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you alre..
Hacking macOS:
How to Create a Fake PDF Trojan with AppleScript, Part 1 (Creating the Stager)
While hackers have taken advantage of numerous vulnerabilities in Adobe’s products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that’s using the default Preview app. So think twice before double-clicking a PDF open on y..
Use Your Android as a Microphone for Your PC
You need a good microphone on your computer in order to make audio recordings, voice chat, or use speech recognition. However, not every computer comes with a built-in mic, and not every built-in mic works great. You can purchase a cheap computer microphone on Amazon for as l..
Discover & Attack Raspberry Pis Using Default Credentials with Rpi-hunter
When setting up a Raspberry Pi, it’s easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi’s default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called r..
Hijack Chromecasts with CATT to Display Images, Messages, Videos, Sites & More
Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called “Cast All the Things, ” we..
Dump a MacOS User’s Chrome Passwords with EvilOSX
Barrow’s article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user’s stored credentials for many accounts. The best loot lives in..
Control Anything with a Wi-Fi Relay Switch Using aRest
A relay is an electrical component that works like a light switch, where it’s turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of..
Intercept Images from a Security Camera Using Wireshark
It’s common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to interce..
Learn How Elliot from Mr. Robot Hacked into His Therapist’s New Boyfriend’s Email & Bank Accounts (Using Metasploit)
Social engineering is a pretty important item in a hacker’s toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist’s boyfriend’s email and bank accounts by calling him and pretending to be someone from his bank, then Elli..
Lock Down Your DNS with a Pi-Hole to Avoid Trackers, Phishing Sites & More
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from eve..
Use Common Features of Windows Command Prompt
Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don’t know anything about it, even how to access it. Even if you aren’t a Windows user, it’s good to know how command prompt works b..


